Windows Device Management
Windows Device Operations
Add New Operation
-
Log in to the Endpoint Management portal.
-
View the device that you have enrolled.
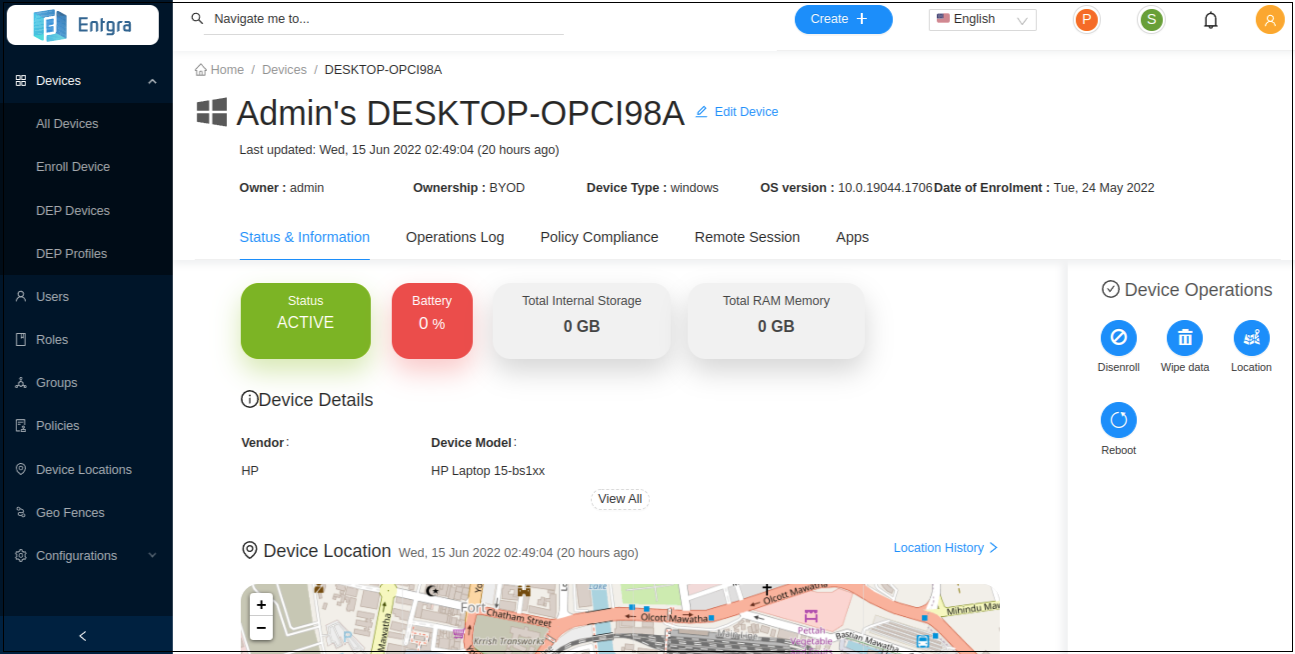
-
Click on the operation you need to apply to the device. (Ex: let’s apply Location operation.)
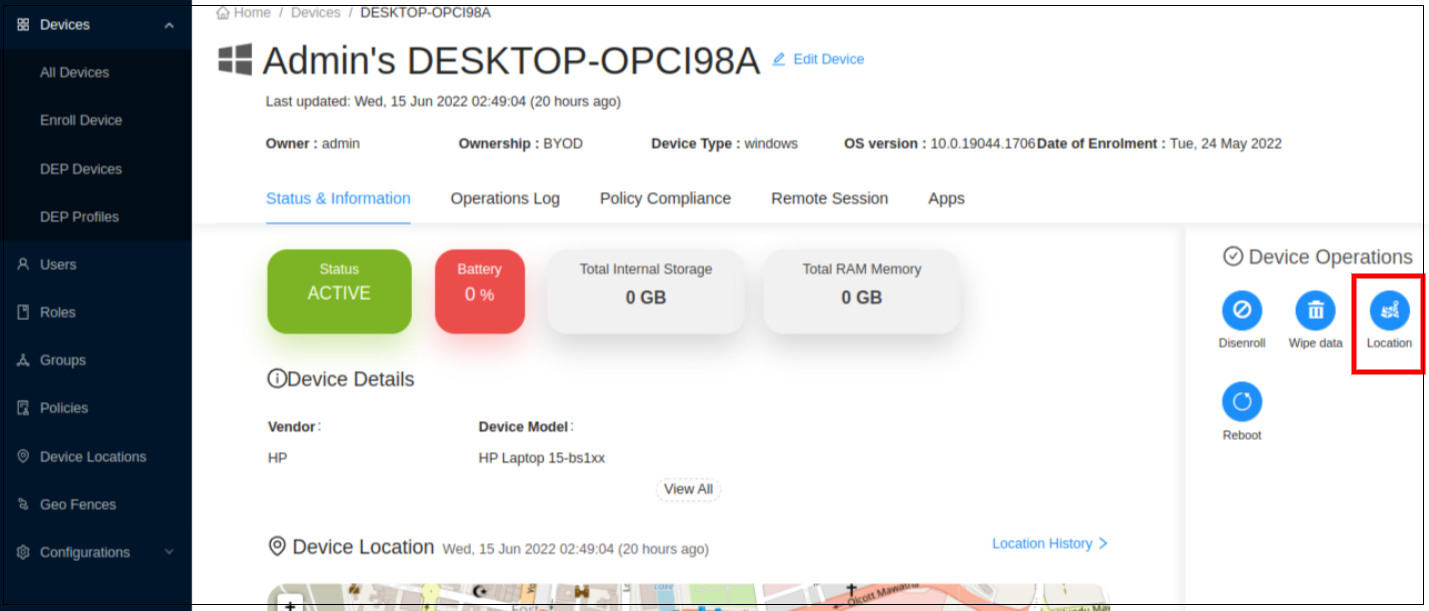
-
A pop-up message will be displayed on the screen. Click Send to Device to confirm the operation.
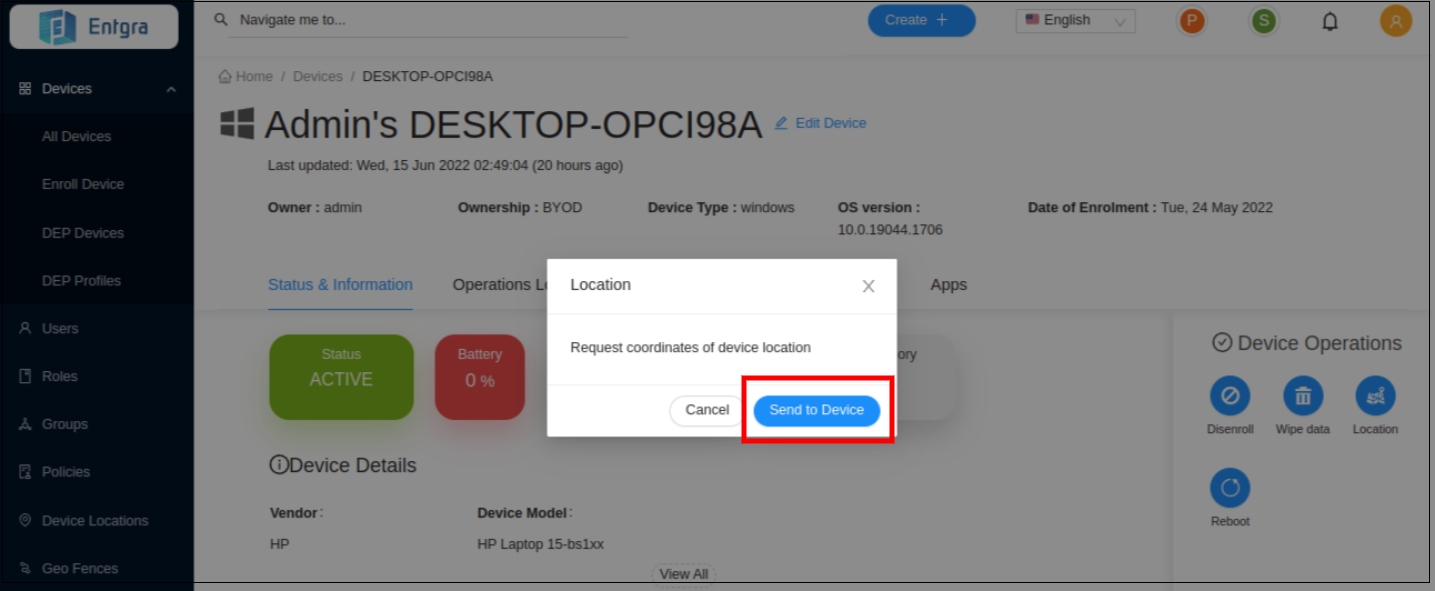
Windows Device Policies
Add New Policy
-
Log in to the Endpoint Management portal.
-
Select Policies in the left navigation.
-
Go to Create + and select Policy.
-
Select the platform by clicking Windows from the listed device types.
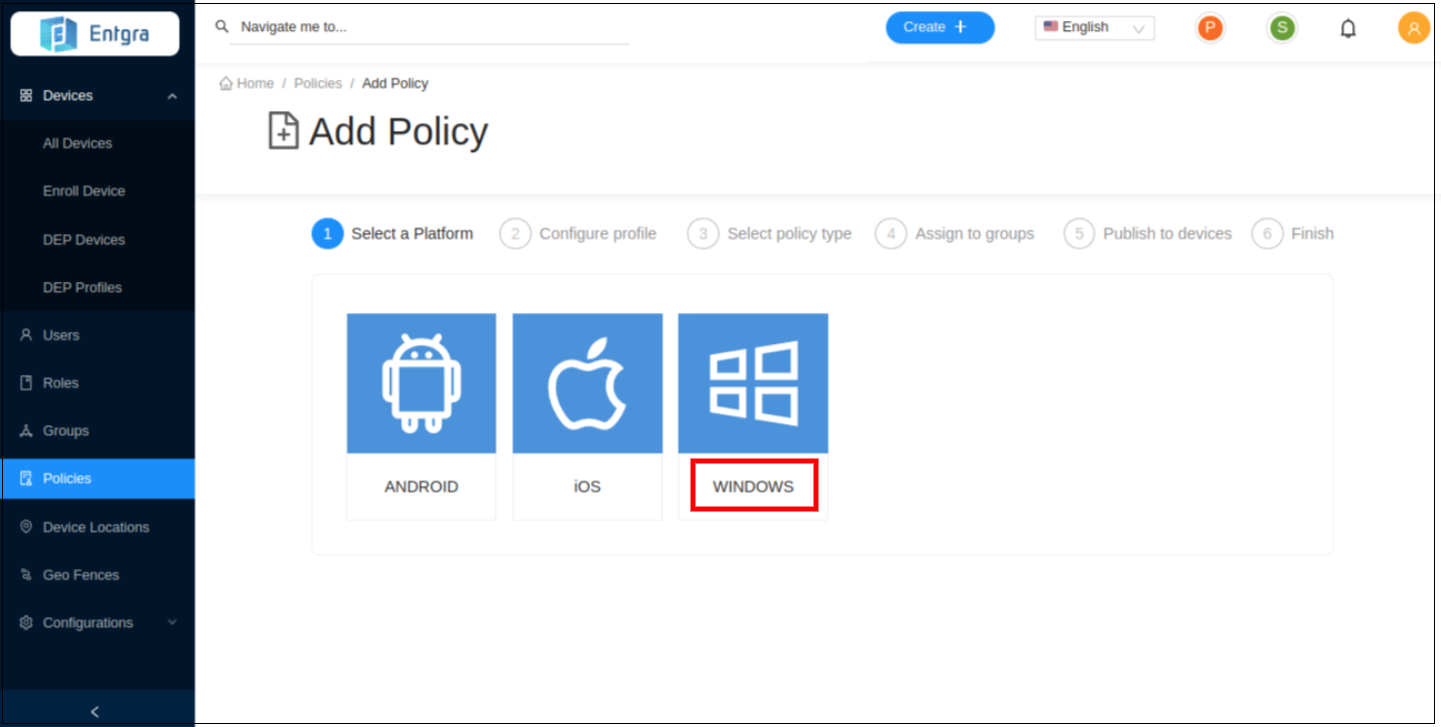
-
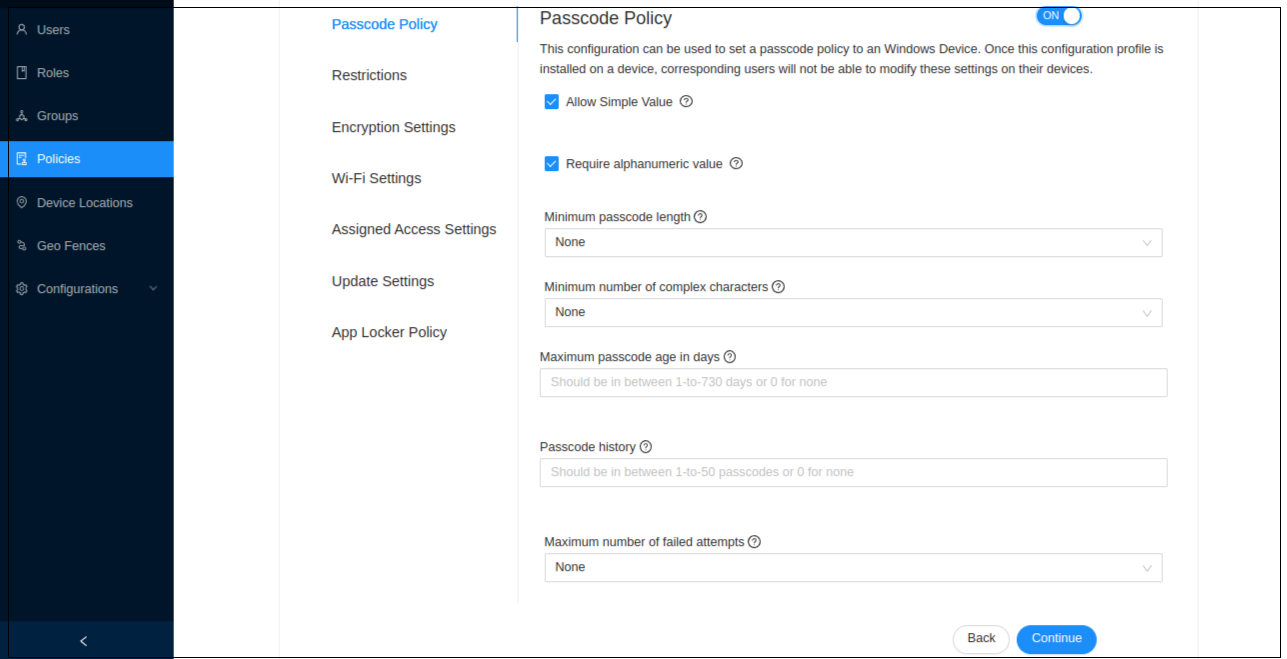
Create your policy. Ex: let’s create a passcode policy. After defining the required settings, click Continue.
-
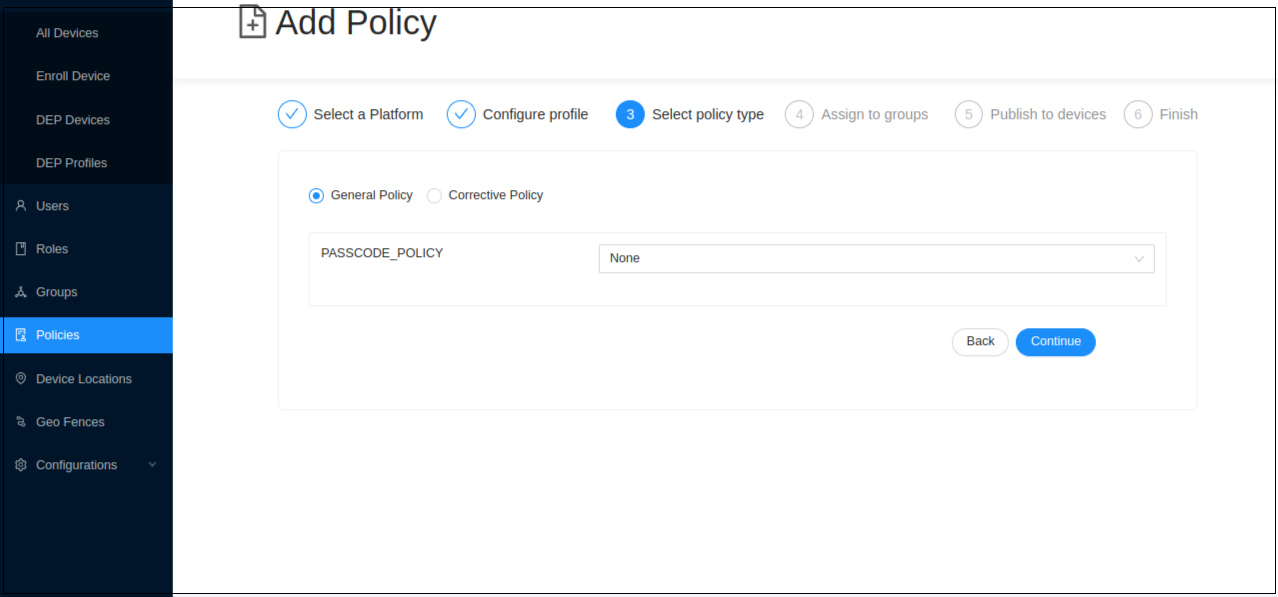
Select the Policy Type.
There are two types of policies:
General Policy: General policy is applied to the device by default.
Corrective Policy: Corrective policy is applied to the device when the general policy is violated. When the general policy is not violated the corrective policy is disabled.
Ex: With the above scenario, let’s select the type as General and click Continue.
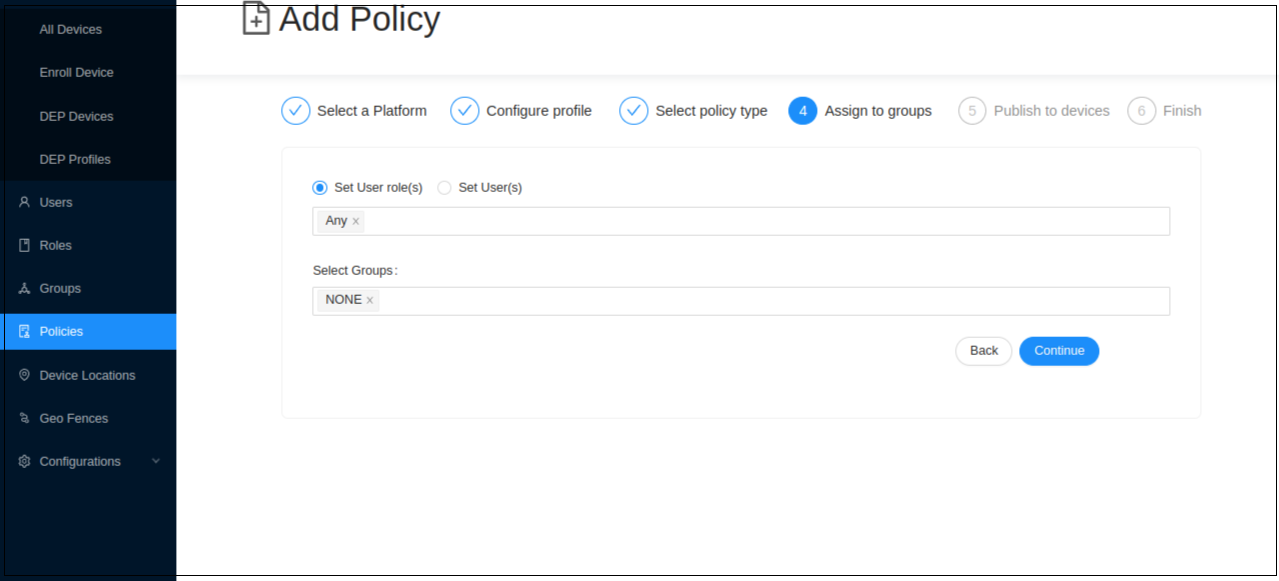
- Define the user groups that the policy needs to be assigned to. Select the Set User Roles or Set users option and select the users/roles from the item list or you can assign a device group. Then click Continue.
- Set a name for your policy and add a description under Publish to devices. Click Save and Publish to save and publish the configured profile as an active policy to the database.
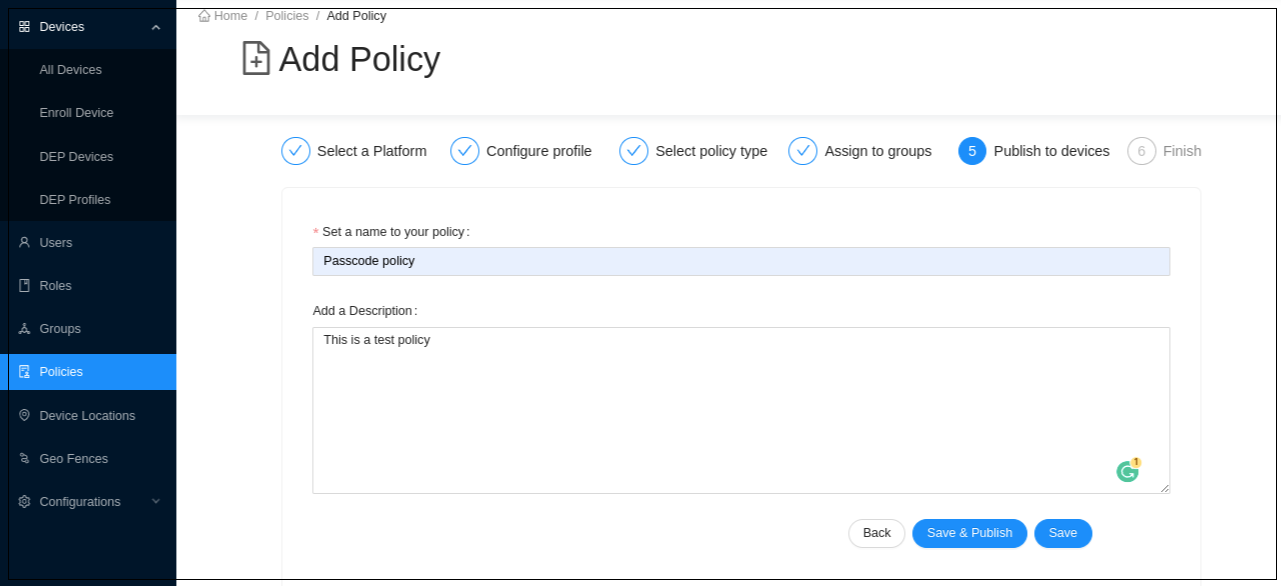
NOTE: If you save the configured profile, it will be in the Inactive state and will not be applied to any device. If you save and publish the configured profile of policies, it will be in an Active state.
- You have now successfully created the new policy. Click Go to Policies to view the policy in the policies list.
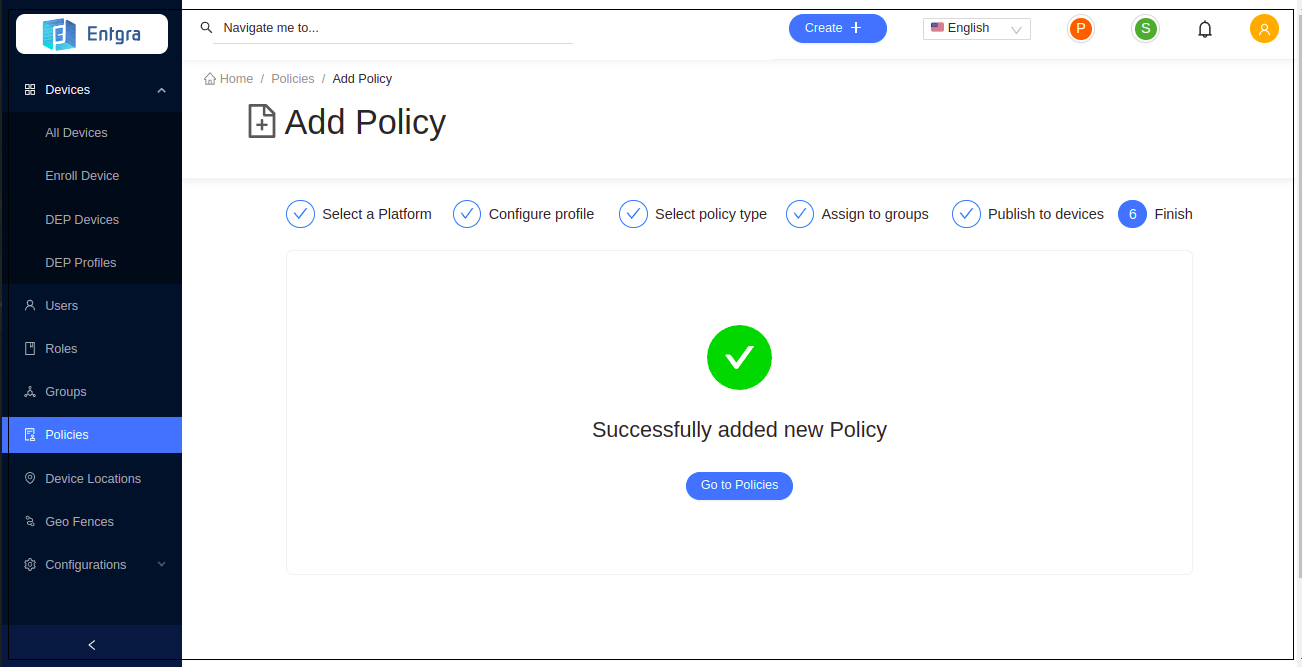
View a Policy
-
Log in to the Endpoint Management portal.
-
Select Policies in the left navigation. You can view all the published policies for the device.
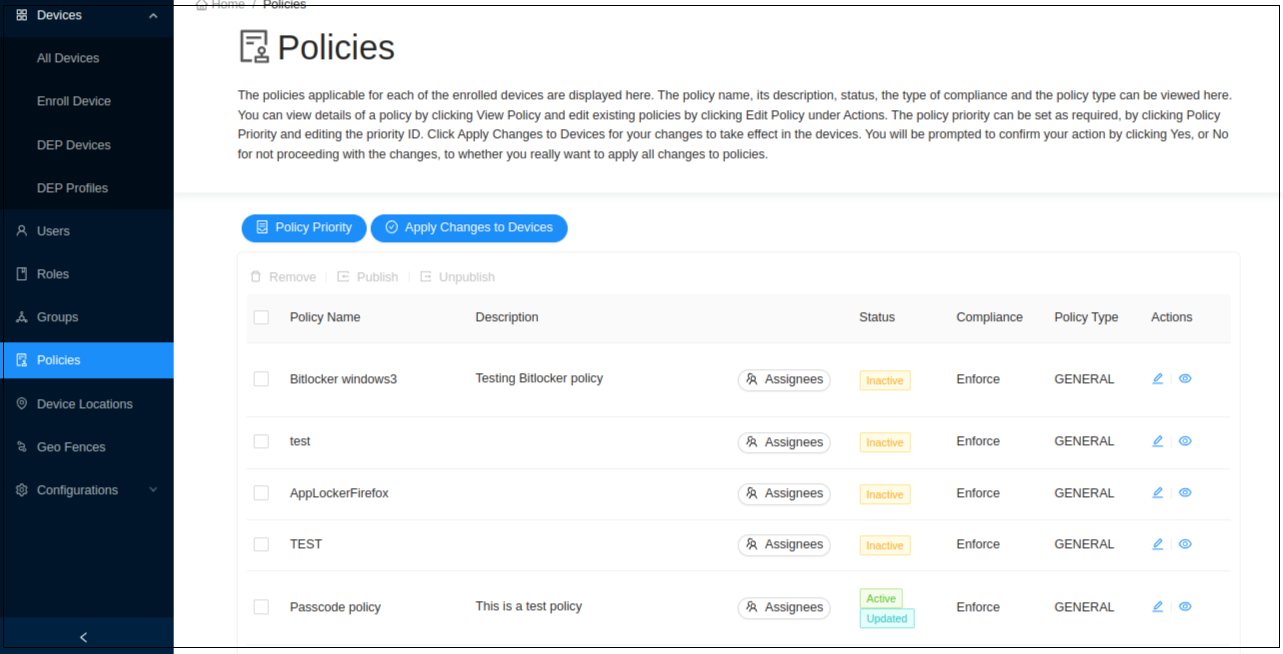
Publish a Policy
-
Click Policies to get the list of the available policies.
-
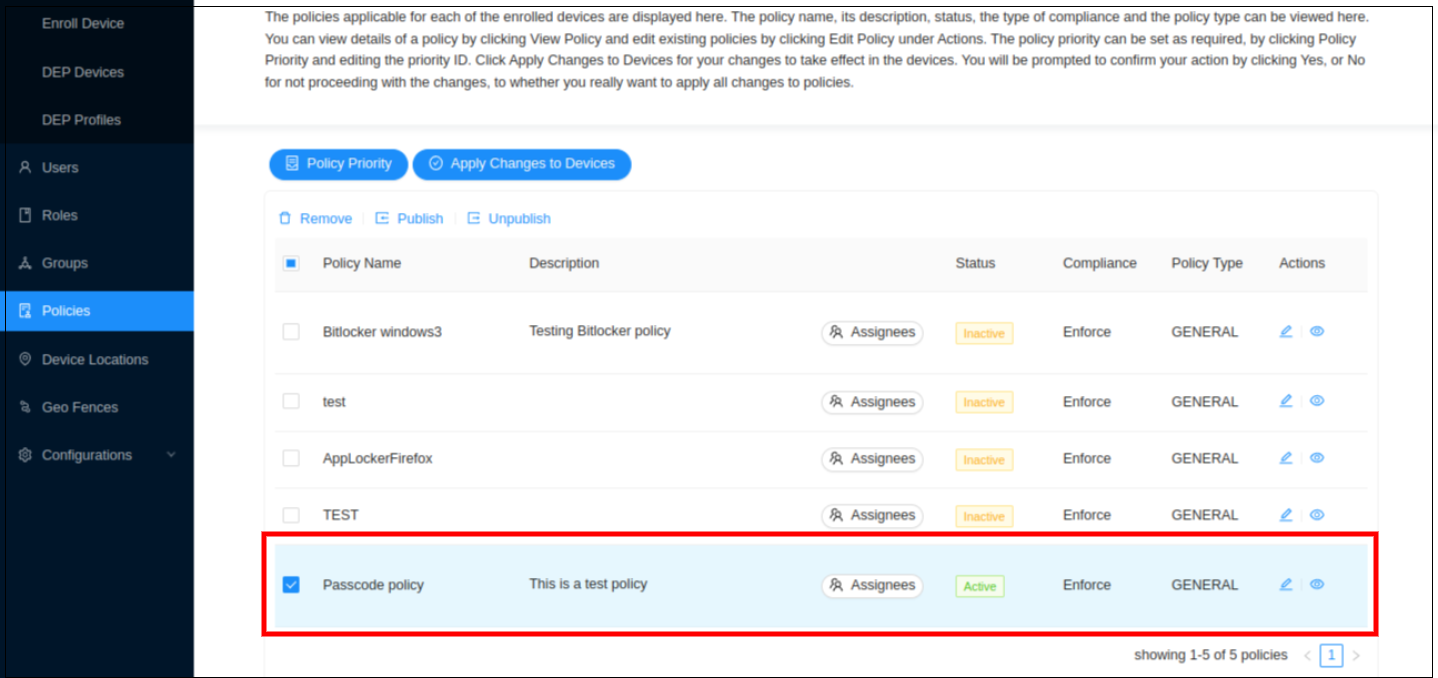
Select the policy that you wish to publish which has not been published already.
-
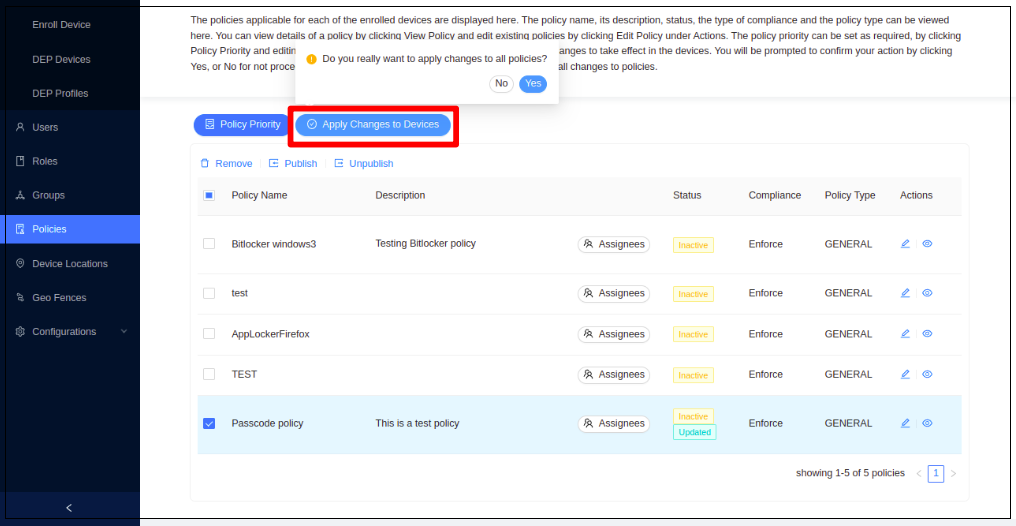
Click Publish.
-
Click Yes to confirm publishing the policy.
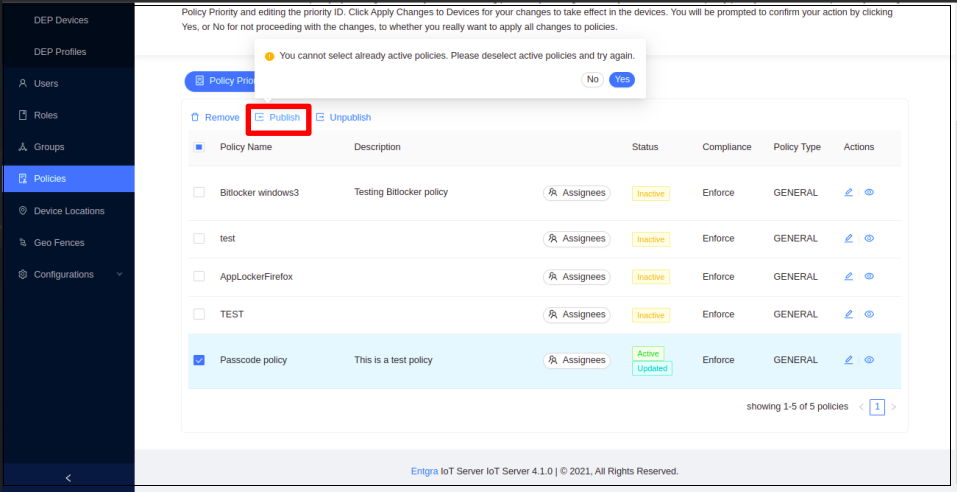
- Next, click Apply Changes to Devices to apply the policy to the devices.
Unpublish A Policy
-
Log in to the Endpoint Management portal.
-
Click Policies.
-
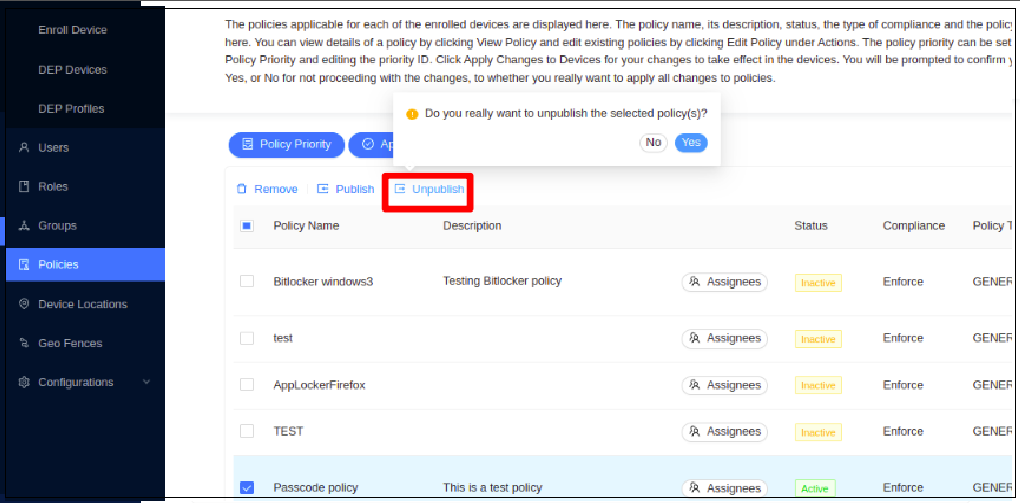
Select the policies that you wish to unpublish from those that have already been published.

-
Click Yes to confirm unpublishing the selected policy.
-
Then click Apply Changes to Devices to apply the change to all the devices.
The selected policy has now been unpublished and is in an inactive/updated state. Therefore, this policy will not be applied to devices that are newly enrolled with the Entgra IoT Server.
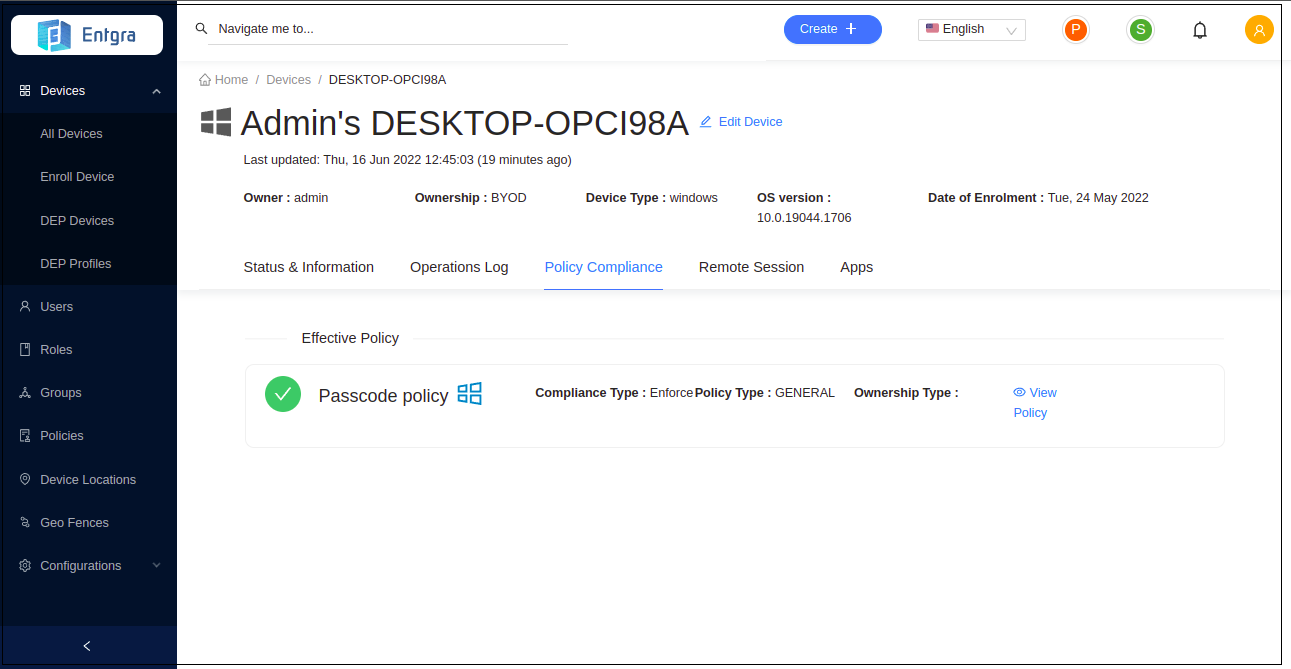
Verify Enforced Policy
-
Click on your device to view the device details.
-
Click Policy Compliance.
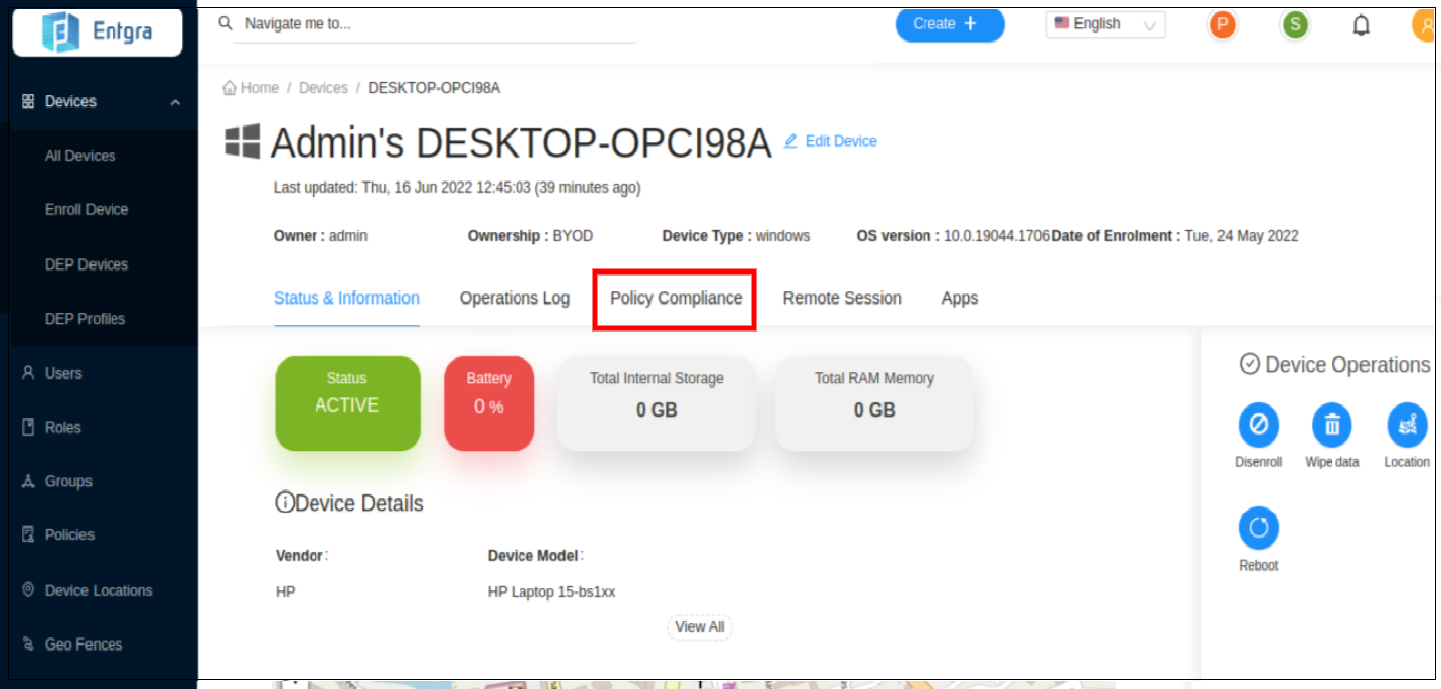
-
You can see the policies that are currently applied to your device.
Manage Policy Priority Order
-
Click Policies to get the list of the available policies.
-
Click Policy Priority.
-
Manage Policy Priority - Drag and drop the policies to prioritize the policies accordingly. Manage the policy priority order by defining the order using the edit box.
-
Click Save New Priority Order to save the changes.
-
Click Apply Changes to Devices to push the changes to the existing devices.
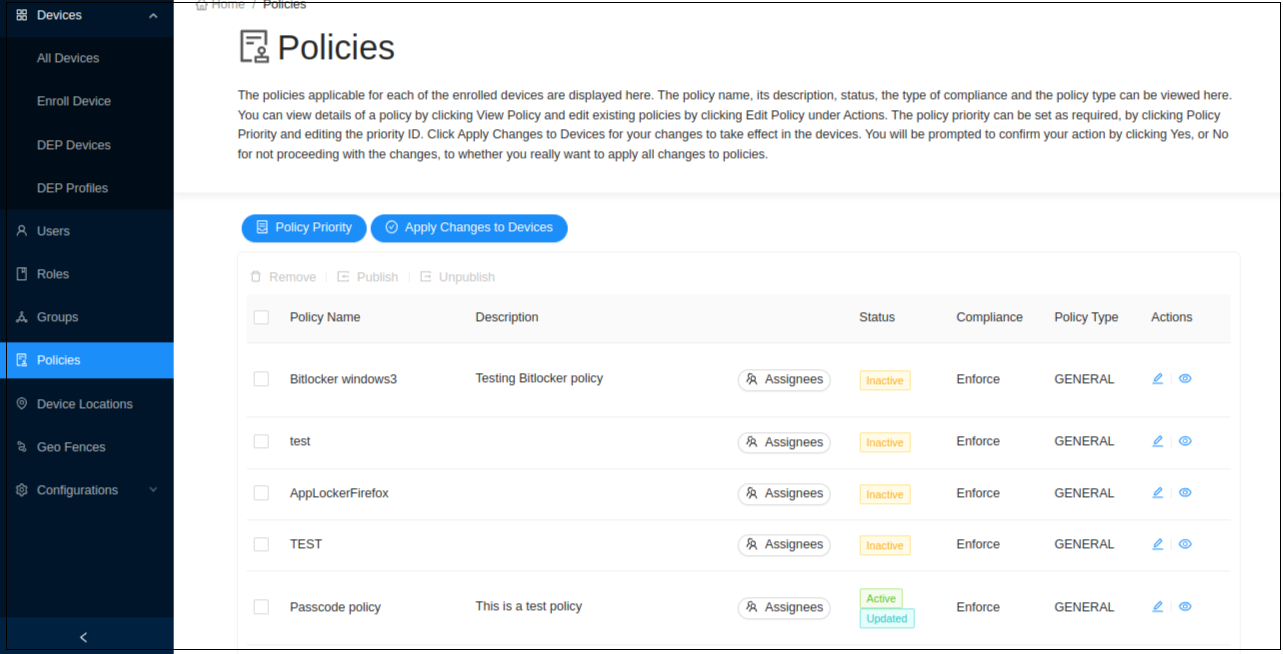
Updating A Policy
-
Click Policies to get the list of the available policies.
-
On the policy you wish to edit, click Edit.
Windows Applicable Policies
The following Policies can be executed on a Windows device.
Passcode Policy
This policy can be used to enforce a configured password on Windows devices.
| Data Key | Policy Description |
|---|---|
| Allow simple value | Allows a sequence of repeating, ascending and descending characters for the password |
| Require alphanumeric value | This indicates that the password must contain both letters and numbers |
| Minimum passcode length | Determines the least number of characters that can make up a password for a user account |
| Minimum number of complex characters | Determines how many complex characters or non-alphanumeric characters could be included in the applying passcode |
| Maximum passcode age in days | Determines the period of time (in days) that a password can be used before the system requires the user to change it. |
| Passcode history | Determines the number of unique new passwords that must be associated with a user account before an old password can be reused |
| Maximum number of failed attempts before device reset | This specifies how many times a user can enter the wrong password before all the data of the device gets wiped. |
Encryption Settings
This configuration can be used to encrypt data on a Windows device when the device is locked and make it readable when the passcode is entered.
| Data Key | Policy Description |
|---|---|
| Enable store encryption | Encryption is the process of encoding all user data on a Windows device using symmetric encryption keys. Having this checked would enable Storage-encryption in the device. |
Wi-Fi Settings
This policy is helped to configure Wi-Fi settings on Windows devices. The users will not be able to modify the settings on their device after the policy applied.
| Data Key | Policy Description |
|---|---|
| Service Set Identifier (SSID) | The identification of the configured Wi-Fi connection. |
| Security | The security type of the configured Wi-Fi connection. |
| Password | Password of the Wi-Fi connection that the device is connected to. |
Assigned Access Settings
This policy is used to set the device to run in kiosk mode. Once this has been executed, the next user log-in that is associated with the kiosk mode puts the device into the kiosk mode running the application specified in the policy configuration.
It is important to keep in mind if there is a single user when the policy is being applied, there is no way to access the settings and manually sync and revoke the policy. The IoT server sends requests every minute and if there are any pending revoked policies it will sync at that time. Alternatively, the device could be manually synced using another user account and the changes will be applied. A computer restart is required for the policy enforcement and revokes to take effect.
| Data Key | Policy Description |
|---|---|
| Account name | The account name will be used to find the target user. The account name includes the domain name (the domain is optional if the user name is unique across the system) and the user name. |
| Application AUMID | The application AUMID is the identifier for Universal Apps (UWP) installed from the Windows Store. Steps to finding the AUMID can be found here. |
Update Settings
Configure update settings on Windows devices.
| Data Key | Policy Description |
|---|---|
| Active hours end | This is used to manage a range of active hours where update reboots are not scheduled. This value sets the end time. There is a 12-hour maximum from start time. |
| Active hours maximum range | Allows admin to specify the max active hours range. This value sets the max number of active hours from start time. Supported values are 8-18. |
| Active hours start | Used to manage a range of hours where update reboots are not scheduled. This value sets the start time. There is a 12-hour maximum from end time. |
| Allow automatic updates | Enables admin to manage automatic update behavior to scan, download, and install updates. |
| Allow automatic updates over metered connections | This is an option to download updates automatically over metered connections. This policy is accessible through the Update setting in the user interface or Group Policy. |
| Allow automatic updates signed by non-microsoft entities | This allows admin to manage whether Automatic Updates accept updates signed by entities other than Microsoft when the update is found at the Update Service URL location. |
| Allow update service | Specifies whether the device could use Microsoft Update, Windows Server Update Services (WSUS), or Microsoft Store. |
| Auto restart deadline in days | Specifies the deadline in days before automatically executing a scheduled restart outside of active hours. The deadline can be set between 2 and 30 days from the time the restart is scheduled. |
| Auto restart deadline in days for feature updates | For Feature Updates, this specifies the deadline in days before automatically executing a scheduled restart outside of active hours. The deadline can be set between 2 and 30 days from the time the restart is scheduled. |
| Notification schedule | This allows admin to specify the period for auto restart reminder notifications. |
| Auto restart notification dismissal | This allows admin to specify the method by which the auto restart required notification is dismissed. |
App Locker Policy
Using this Windows App Locker policy, it is possible to block apps that need to be restricted from the users.
| Data Key | Policy Description |
|---|---|
| Application ID | The ID of the application that is to be added to the policy. |
| Application Name | The name of the application that is to be added to the policy. |
| Type | The application type. |
| Description | A brief description about the application. Optionally, this can be left blank. |
| User or Group SID | |
| Publisher Name | Full name of the application. |
| Product Name | The product name is the first part of the PackageFullName followed by the version number. In the Windows Camera example, the ProductName is Microsoft.WindowsCamera. |
| Binary Name | Indicates the app name with the extension. |
| High Section | Defines the highest version number that should be trusted. |
| Low Section | Defines the lowest version number that should be trusted. |
| Enforcement Mode | |
| Action | Action is to whether allow the app or deny the app usage. |
Defender Policy
Various Windows Defender actions can be configured throughout the enterprise using the Windows Defender Configuration Service Provider.
| Data Key | Policy Description |
|---|---|
| Allow archive scanning | Windows Defender will scan the contents of compressed (archive) files when a scan is scheduled or when the user starts the scanning process manually. |
| Allow behavior monitoring | This policy setting allows you to configure behavior monitoring. When you enable this setting behavior monitoring will be enabled. |
| Allow cloud protection | Standard real-time protection is improved by this cloud protection, also known as Microsoft Advanced Protection Service (MAPS) |
| Allow email scanning | This is specifying if email scanning is permitted or not. |
| Allow full scan of mapped network drives | Determines whether a complete scan of mapped network drives is permitted or not. |
| Allow full scan removable drives scanning | Whether a complete scan of removable drives is permitted or not. Removable drives may still be scanned during a fast scan. |
| Allow IOAV protection | This policy setting specifies whether Windows Defender IOAVP Protection is permitted or not. |
| Allow on access protection | Allowing or disallowing Windows Defender On Access Protection functionality. |
| Allow real-time monitoring | Specifies whether Windows Defender real-time monitoring is allowed or not. |
| Allow scanning network files | Specifies whether Windows Defender real-time monitoring is allowed or not. |
| Allow real-time monitoring | Determines if it is permissible to scan network files. |
| Allow script scanning | Specifies whether the Windows Defender Script Scanning feature is allowed or not. |
| Allow user UI access | Gives or denies users access to the Windows Defender user interfaces. Note: There is a dashboard view available to display security analytics data captured from Windows devices. #1466. The dashboard contains a few charts which are showing below listed information: - Defender updated vs not, - Viruses found devices vs not, - Reboot required vs not, - Full scan done vs not, - Defender enabled vs not, - Tamper protection enabled vs not. |
BitLocker Settings
This policy can be used to encrypt storage devices of a Windows using the BitLocker encryption tool. It can be used on devices which are containing TPM and not.
This can be used to encrypt different drive types: 1. System drives (Operating system drive) 2. Fixed data drives (Non-operating system disk partitions of the device) 3. Removable storage devices (Portable hard drives, USB flash drives)
The BitLocker decryption key can be generated and stored in the following ways:
-
Devices containing TPM
- Use only TPM and store the decryption key in TPM
- TPM + USB key
- TPM + PIN
- TPM + USB key + PIN
-
Devices not containing TPM
- Using a USB key
- Using a PIN
| Data Key | Policy Description |
|---|---|
| Require device encryption | Allowing the administrator to require encryption that needs to be turned on by using BitLocker\Device Encryption. |
| Require storage card encryption | |
| Removable devices require encryption | This setting is a direct mapping to the BitLocker Group Policy "Deny write access to removable drives not protected by BitLocker" |
| Enable non-TPM key | This is used to allow BitLocker without a compatible TPM. A password or a USB drive is required for start-up in this mode. |
| Enable TPM startup PIN and key | Used to configure the TPM startup PIN and TPM startup key. |
| Enable TPM startup | Used to configure the TPM startup. |
| System drives enhanced PIN | Allowing users to configure whether or not enhanced startup PINs are used with BitLocker. |
| Disable standard user to change system drive PIN | Disallow changing PIN of system drives by non-admin users. |
| TPM minimum startup PIN length | PIN length can be set to a minimum character count. |
| Allow certificate-based data recovery agent | Allow users to configure a certificate-based data recovery agent. |
| Enable recovery password | Prompt users to enter a recovery password. |
| Save Bitlocker recovery information to Archive Directory Domain Services | Save the recovery key to Active Directory. |
| Save recovery key to Archive Directory Domain Services | Disable encryption until the Recovery key is stored in an Active Directory server. |
Restrictions Policies
Restrictions policies are those that can be applied on a device restricting or controlling the use of certain specific device features.
The following restriction policies are applicable on a Windows device.
| Data Key | Policy Description |
|---|---|
| Disable Camera | This restriction disables the camera on the device. |
| Disable Location | Selecting this undermines the location service for the device. |
| Disable Storage Card | When enables, the device is restricted from accessing the SD card slot. |
| Disable Device Reset | This is used for disabling the device resetting remotely. |
| Disable OneDrive sync | This will disable sync files with OneDrive. |
| Disable manual root certificate install | This restriction would disable manual root certificate installation in the device. |
| Disable Bluetooth | Disabling Bluetooth control in the device. |
| Disable cellular data | Disabling mobile data roaming on the device. Applicable only for mobile devices. |
| Disable data roaming | This restriction will disable the cellular data roaming on the device. Applicable only for mobile devices. |
| Disable connected devices | When enables, users are not allowed to connect with other devices. |
| Disable Disable connect with PC | Users are not allowed to connect with other devices after disabling this. |
| Disable connected devices | Disallowing connection with a PC of the device. |
| Disable NFC | This will disable Near Field Communications (NFC) and transfer data between devices using NFC technology. |
| Disable USB connection | This restriction will disable the USB drivers connection through USB ports. This only works for mobile devices. |
| Disable VPN configurations | By using this user can restrict the VPN configuration settings in the device. Applicable only for mobile devices. |
| Disable VPN roaming | This policy restriction will disable VPN roaming in the device. Applicable only for mobile devices. |
| Disable date time | This would disable date and time configurations in the device. |
| Disable non Microsoft accounts | This could be used to block users from switching to Microsoft accounts. |
| Disable private windows in the browser | Users will be restricted from using private browsing on the devices. |
| Disable indexing of removable drivers | This is used to search results containing files from removable devices. |
| Disable language settings | Users are not allowed to disable the language settings on the device. |
| Disable Disable region settings | Users are not allowed to disable the region settings on the device. |
| Disable Cortana | Once applied, Cortana gets disabled. |