Device Policies
In this section, you will find comprehensive guides on managing policies across various operating systems supported by Entgra UEM. Detailed explanations and procedures for each of the following subsections are provided:
- General Policy Operations: Outlines the fundamental steps for creating, applying, and managing policies across all supported platforms.
- Android Policies: Detailed instructions for managing policies specific to Android devices.
- iOS & MacOS Policies: Guidance on managing policies for Apple devices, including iPhones, iPads, and Macs.
- Windows Policies: Guidelines for configuring and controlling policies for Windows devices
General Policy Operations
Add New Policy
Prerequisites
- The server has to be downloaded and started.
- Must have been logged on to the server's Endpoint Management Portal and enrolled a device.
-
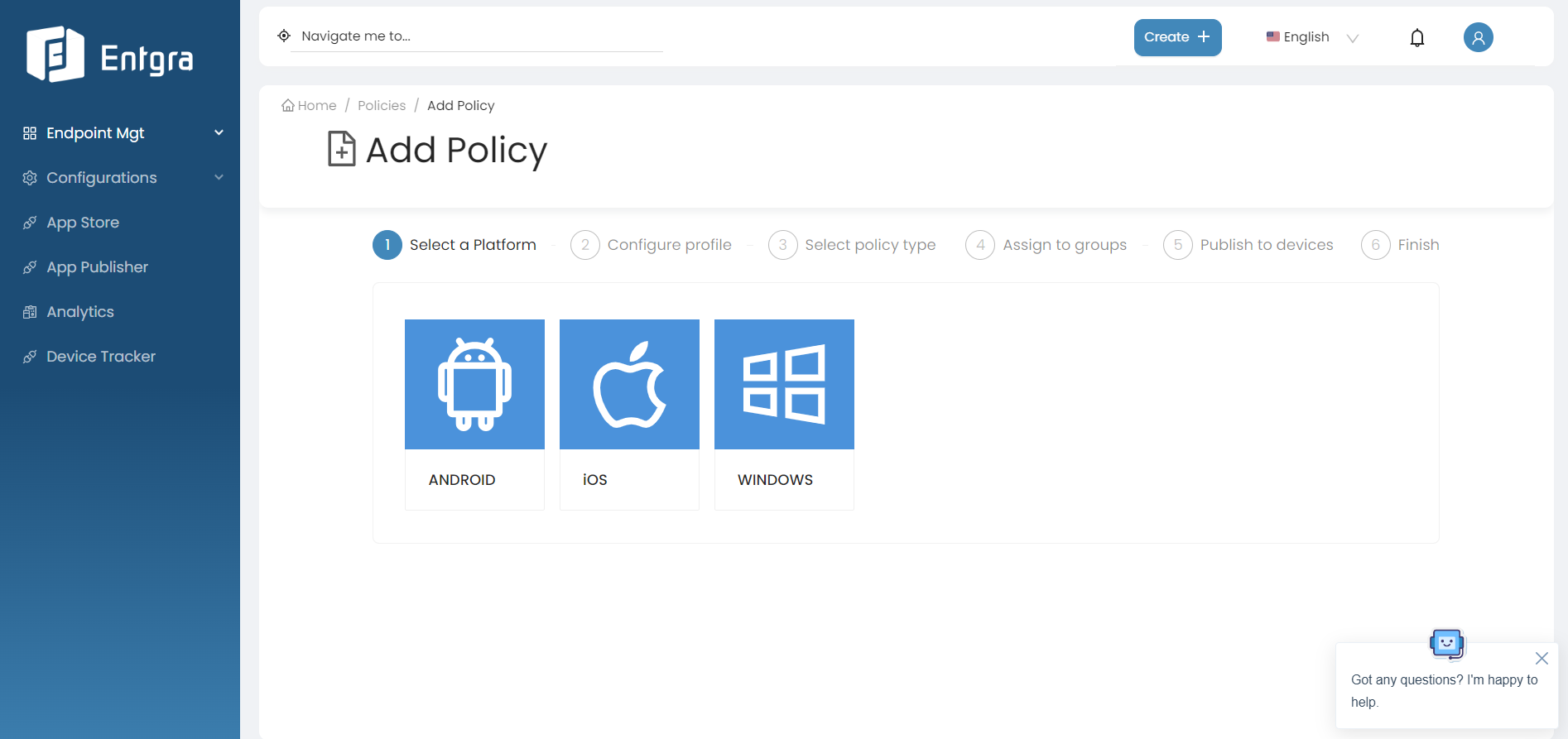
Select Policies in the left navigation.
-
Go to Create + and select Policy.
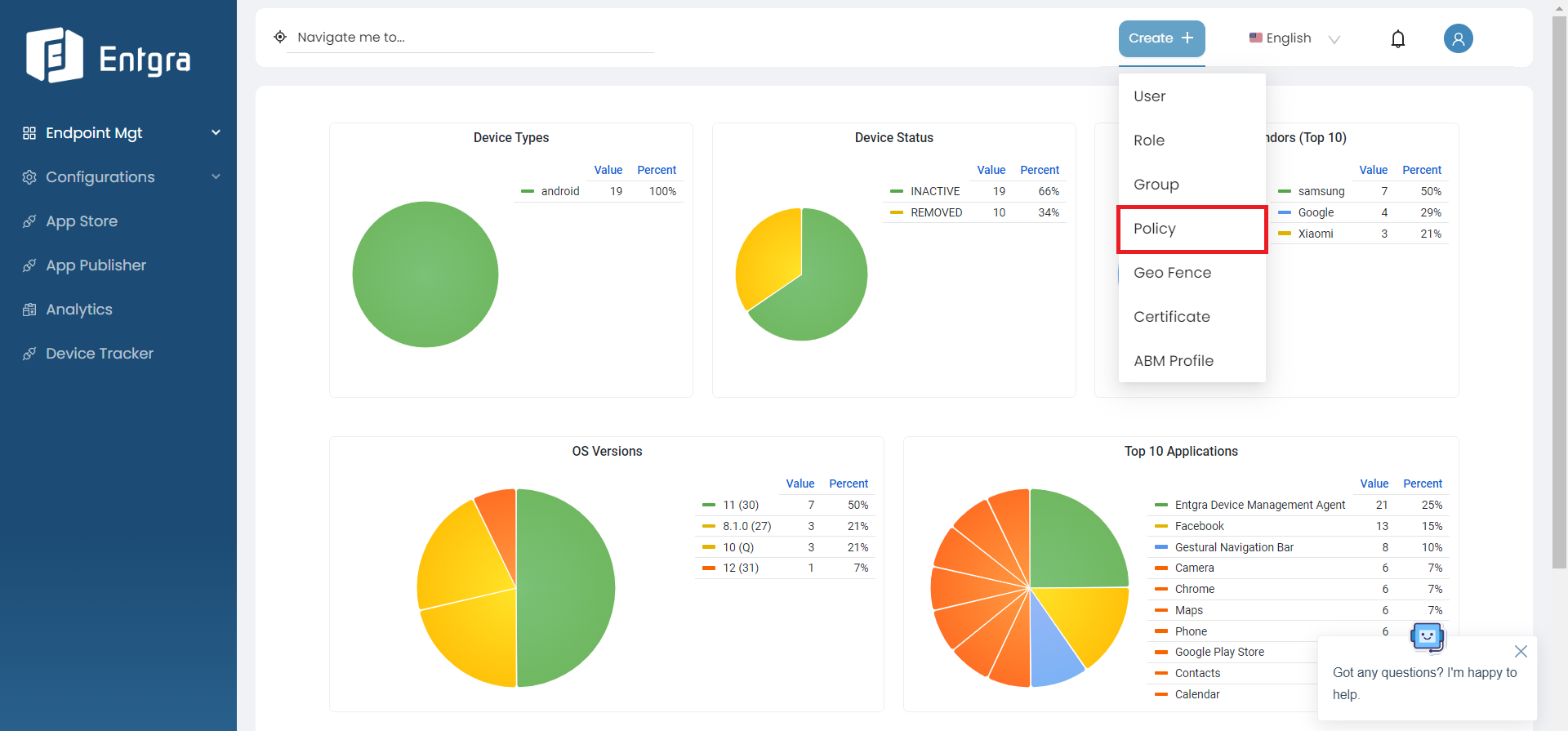
-
Select the platform from the listed device types. (Example : Android)
-
Create your policy. In this tutorial, let us create a passcode policy.
Note
A profile in the context of Entgra UEM Server refers to a collection of policies. For example, in this use case you are only creating one policy that is the passcode policy. If you want to, you can add an restrictions policy too. All these policies will be bundled as a profile and then pushed to the devices.
-
After defining the required settings, click Continue.
-
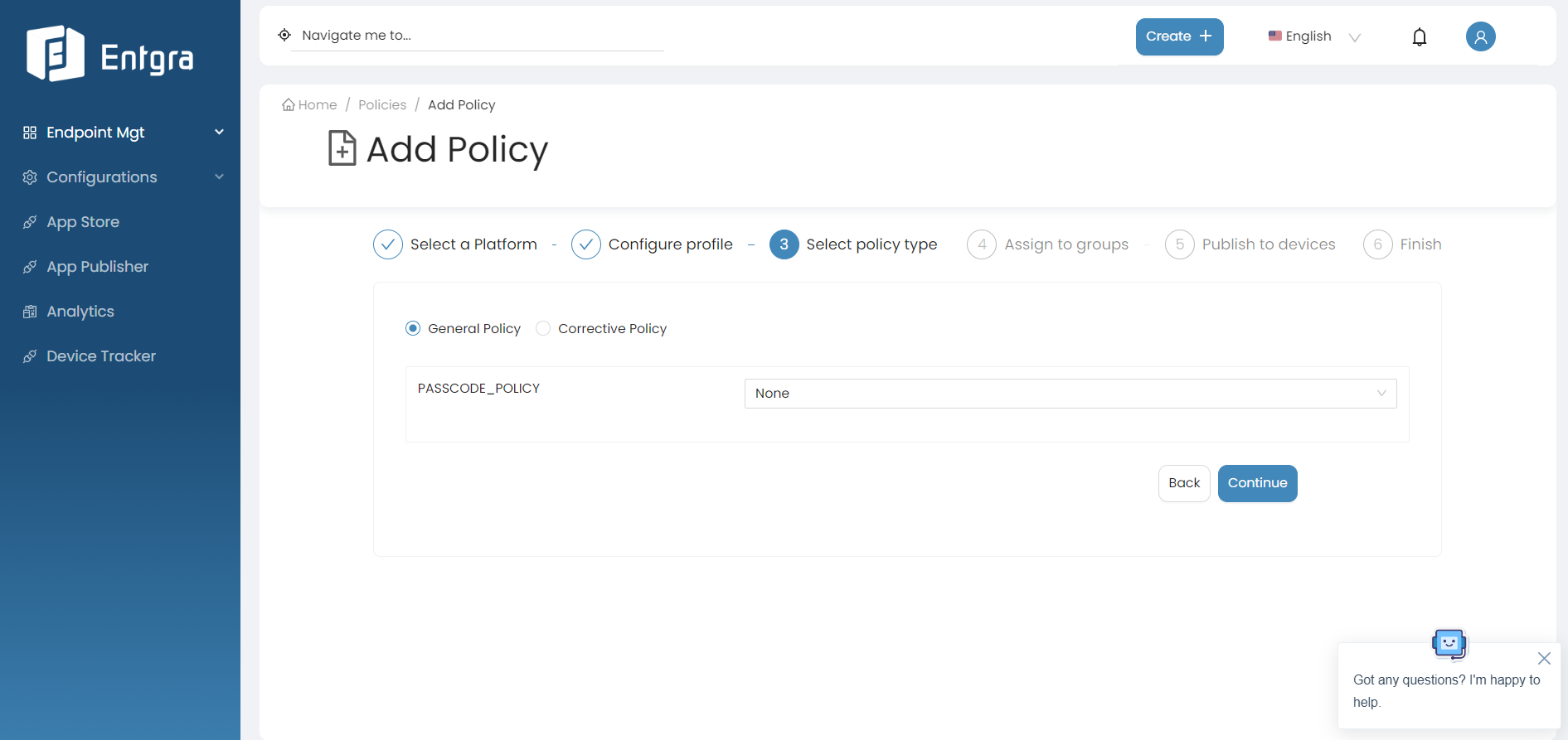
Select the policy type.
There are two types of policies.
-
General Policy: General policy is applied to the device by default.
-
Corrective Policy: Corrective policy is applied to the device when the general policy is violated. When the general policy is not violated the correctiv policy is disabled.
If you wish to apply a corrective policy with a general policy;
-
First create a corrective policy by selecting the policy type as the corrective policy.
-
Then create a general policy by selecting the policy type as the general policy. Select the corrective policy from the dropdown list to be applied when this general policy is violated.
-
-
-
Click Continue.
-
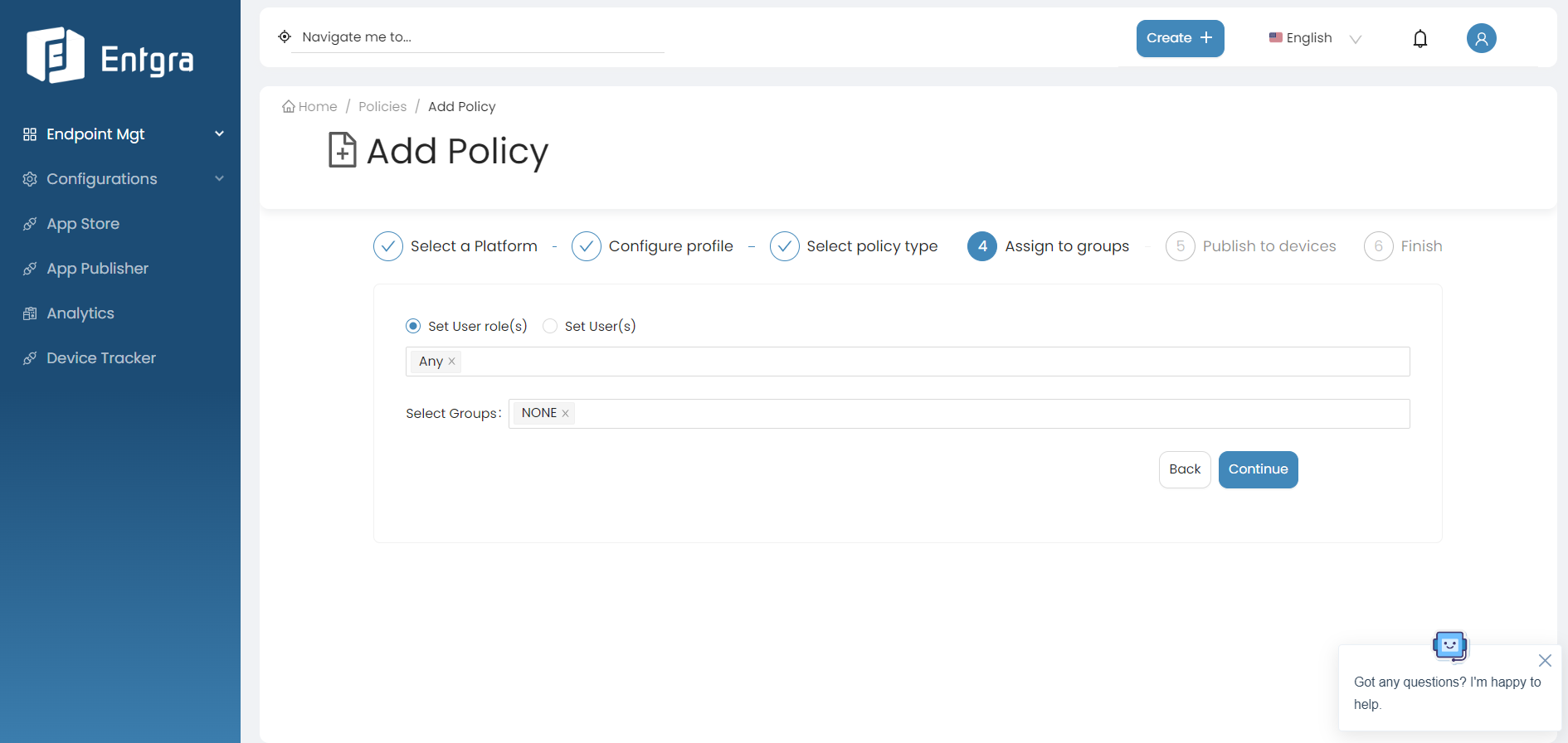
Define the user groups that the passcode policy needs to be assigned to:
- Select Set User role(s) and then select the roles from the item list to be assigned the policy.
- Select Set User(s) and then select the users from the item list to be assigned the policy.
- Select Groups from the item list to be assigned the policy.
For this example, let's select Set User role(s) and then select ANY here.
-
Click Continue.
-
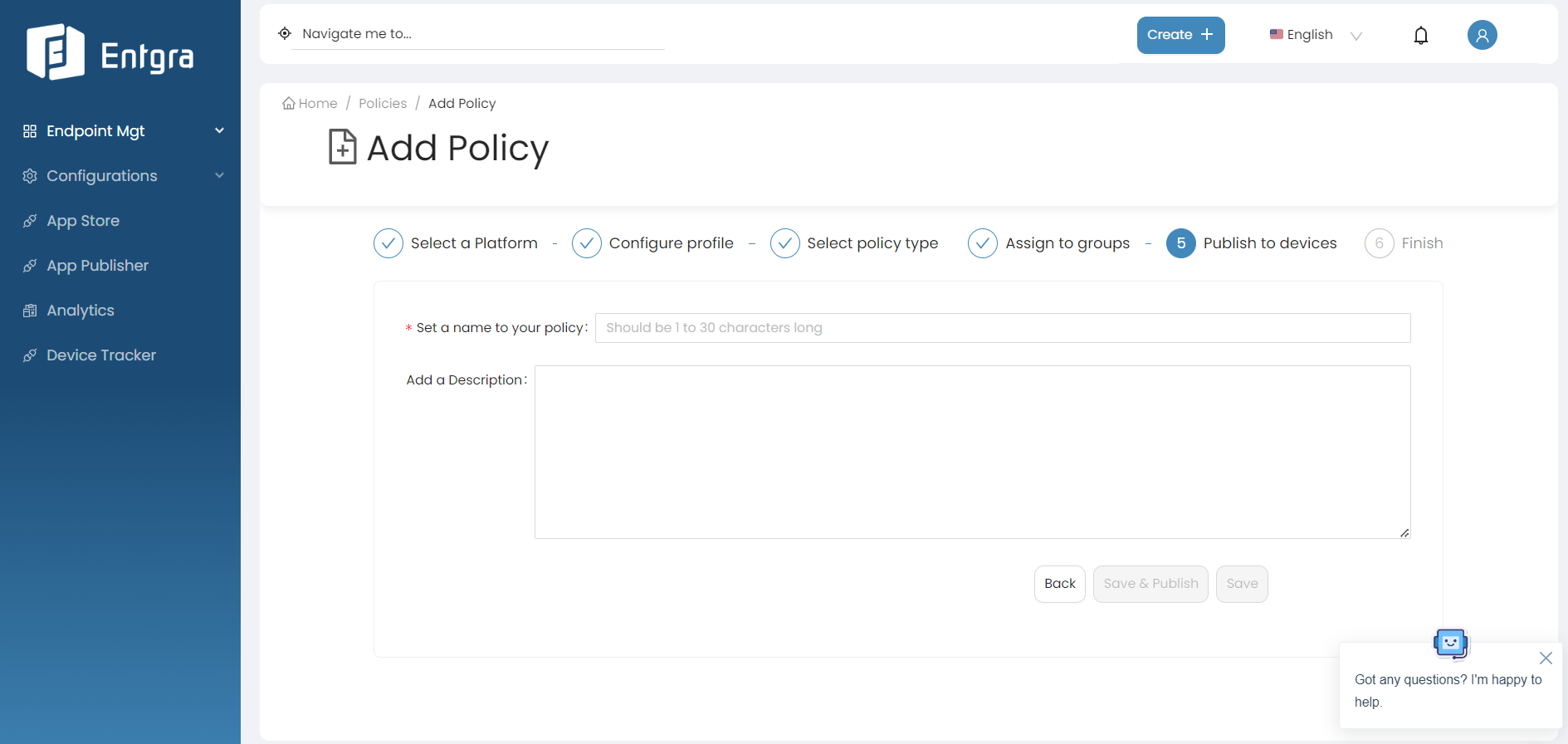
Set a name for your policy and add a description under Publish to devices.
-
Click Save and publish to save and publish the configured profile as an active policy to the database.
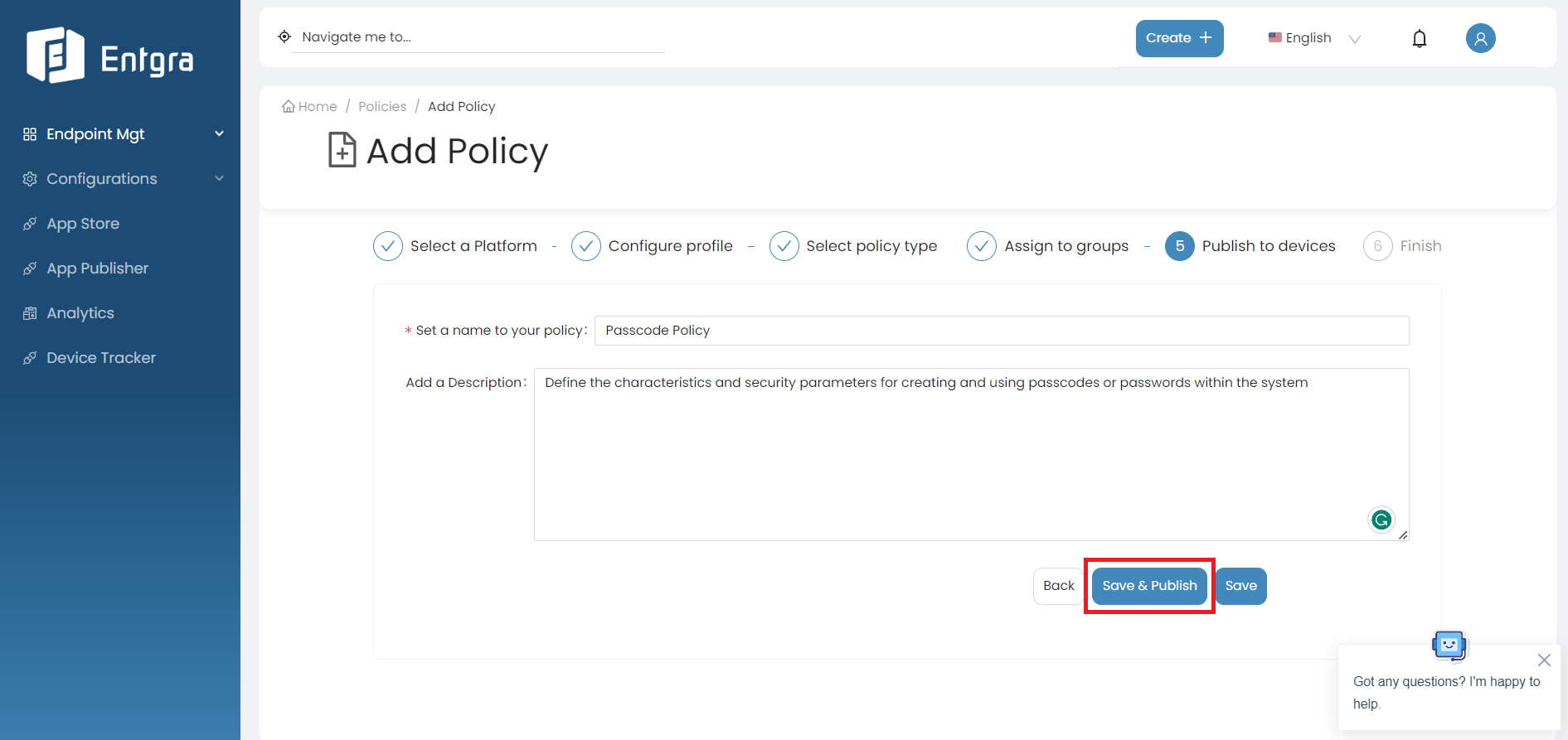
Note
If you Save the configured profile, it will be in the Inactive state and will not be applied to any devices. If you save and publish the configured profile of policies, it will be in Active state.
-
You have now successfully created a new policy and applied it to devices. Click Go to Policies to view all applicable policies.
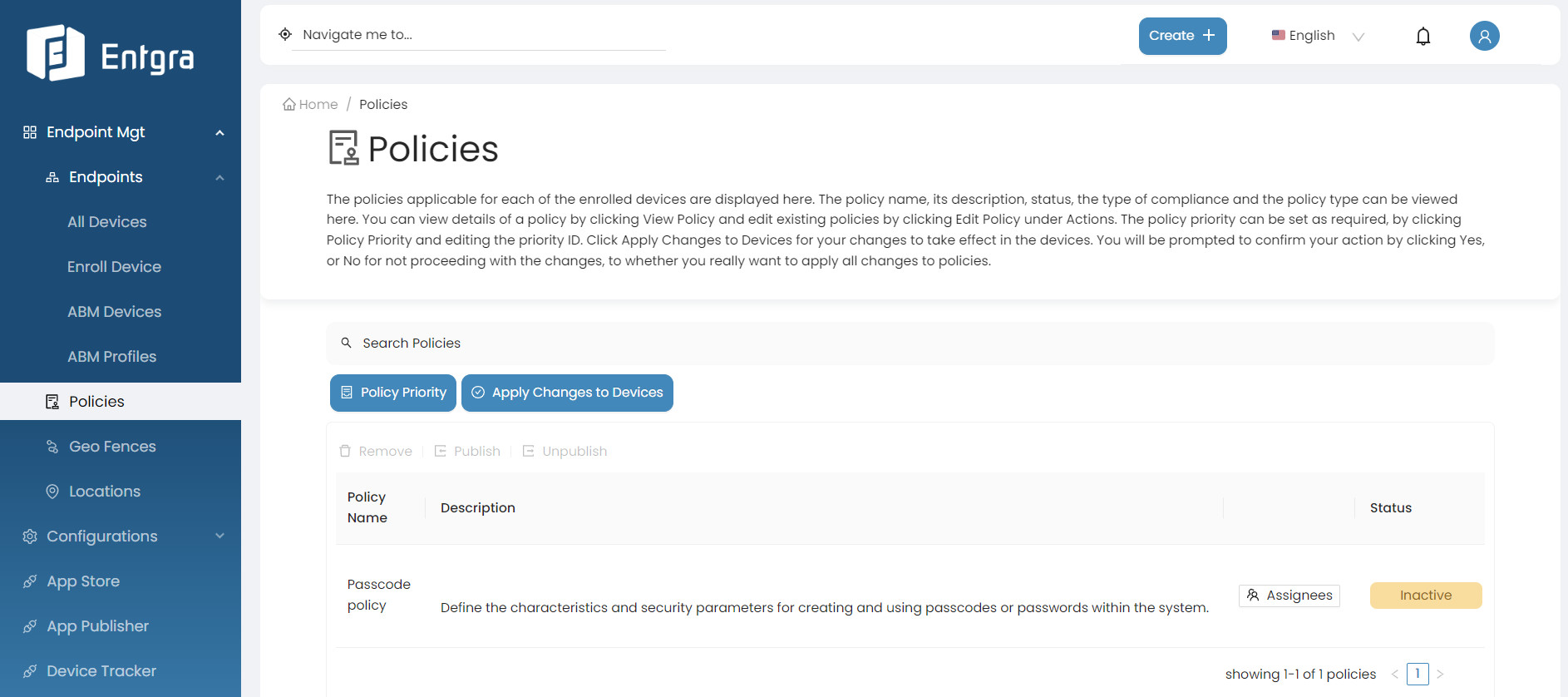
View Policies
-
Sign in to the Entgra UEM Server console.
-
Select Policies. You can view all the available policies.
Search Policies
-
Sign in to the Entgra UEM Server console.
-
Select Policies.
-
Click on the Search Devices bar on top of the policies table.
-
Add relevant tags for searching and then click Search icon.
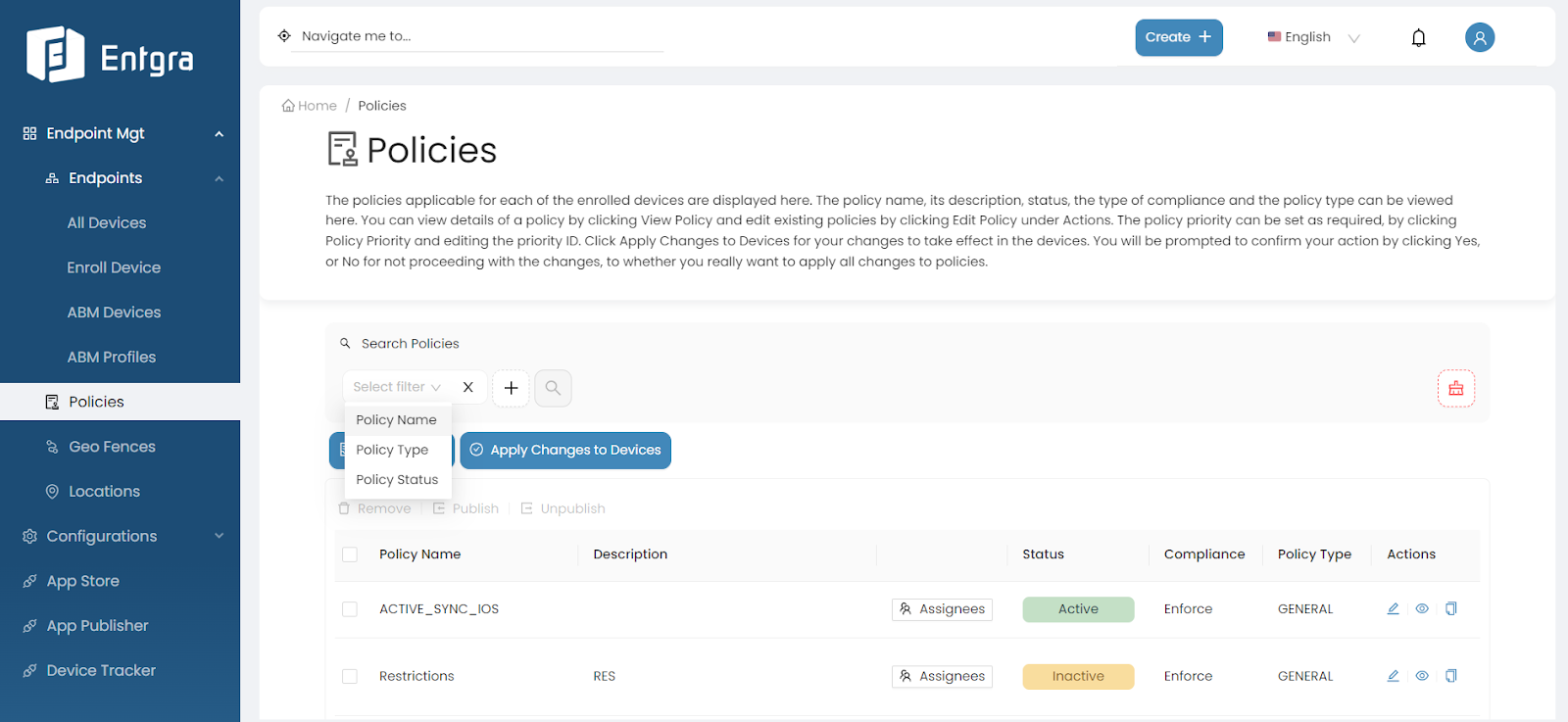
Tags Parameters Policy Name Search for policies by part of the policy name Policy Type Search for policies by policy types; General or Corrective Policy Status Search for policies by policy status; Active or Inactive
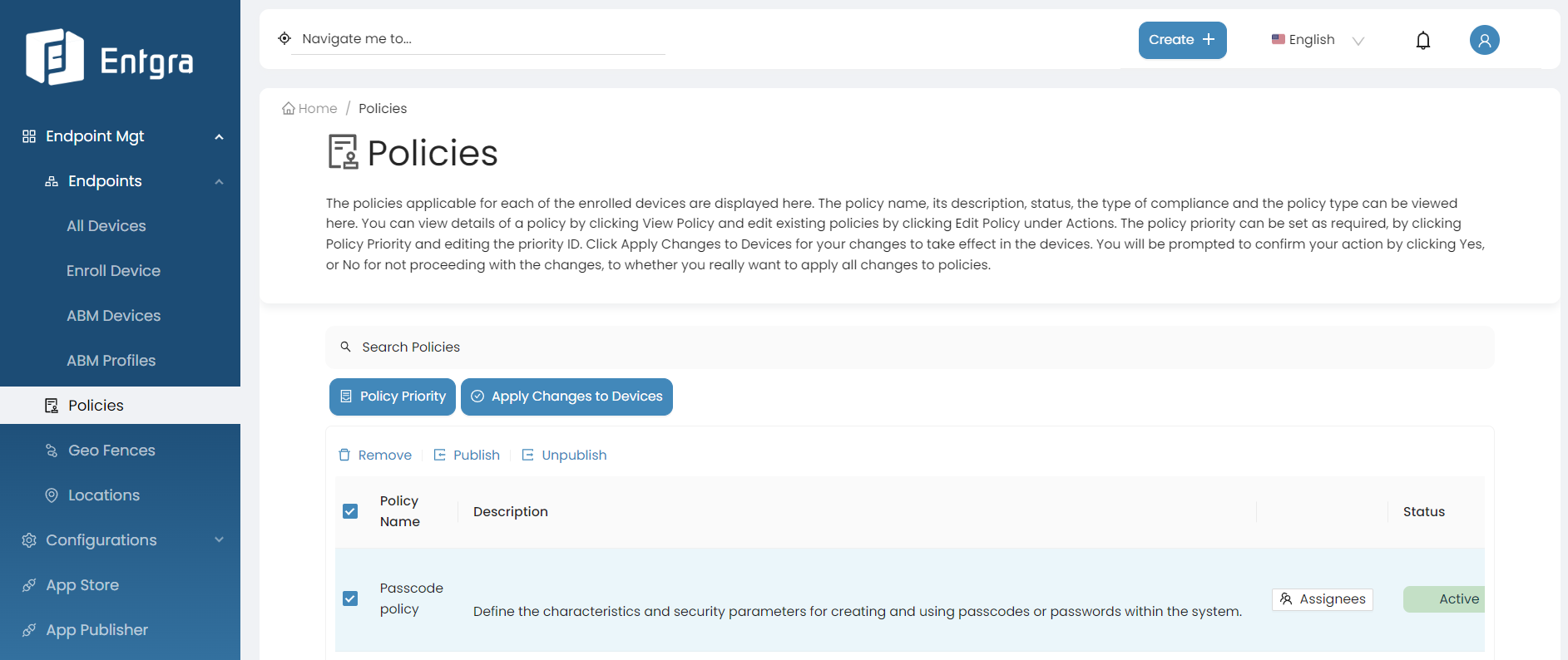
Publish Policies
-
Sign in to the Entgra UEM Server console.
-
Click Policies to get the list of the available policies.
-
Select the policy that you wish to publish which has not been published arleady.
-
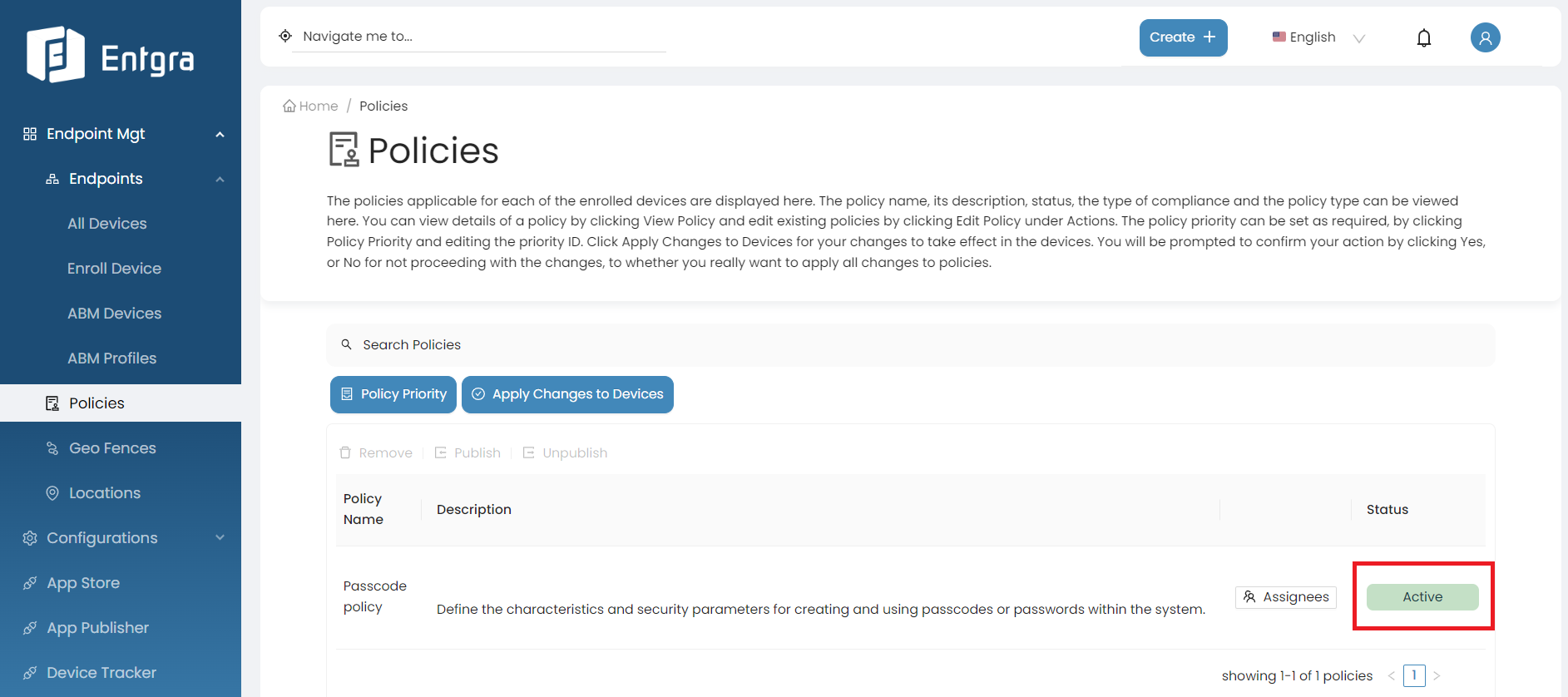
Click Publish.
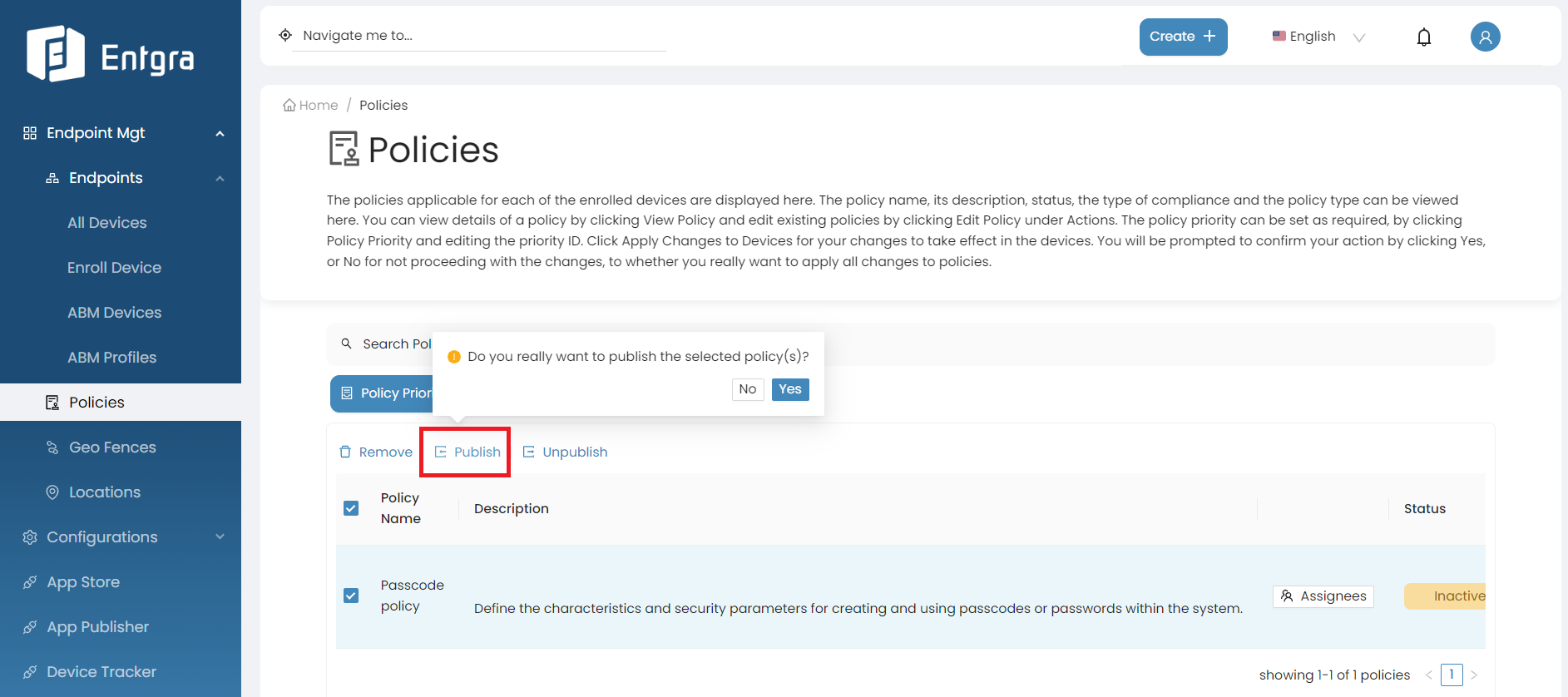
-
Click Yes to confirm publishing the policy.
-
Then click Apply Changes to Devices to apply the policy to the devices.
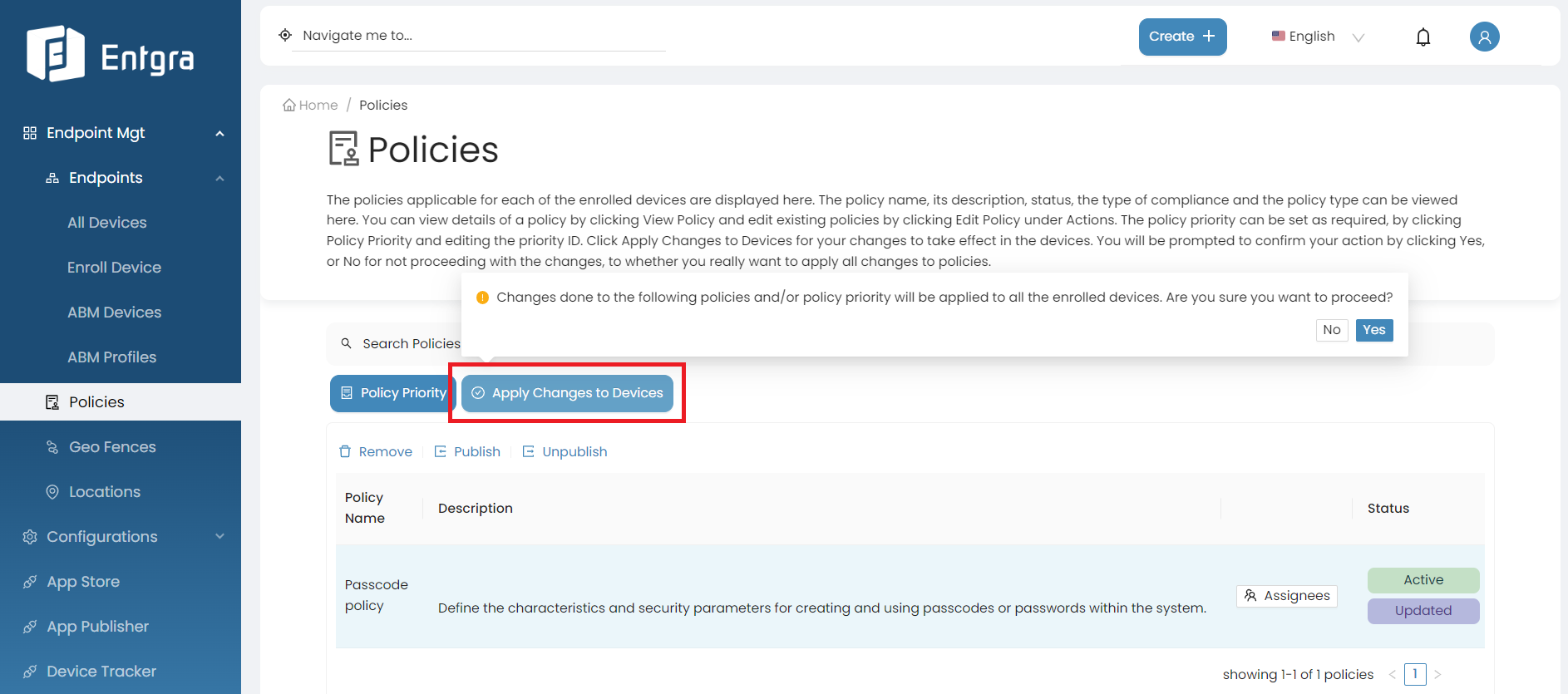
-
The selected policy has now been published and is in active state. Therefore, this policy will be applied on devices that are newly enrolled with Entgra UEM Server.
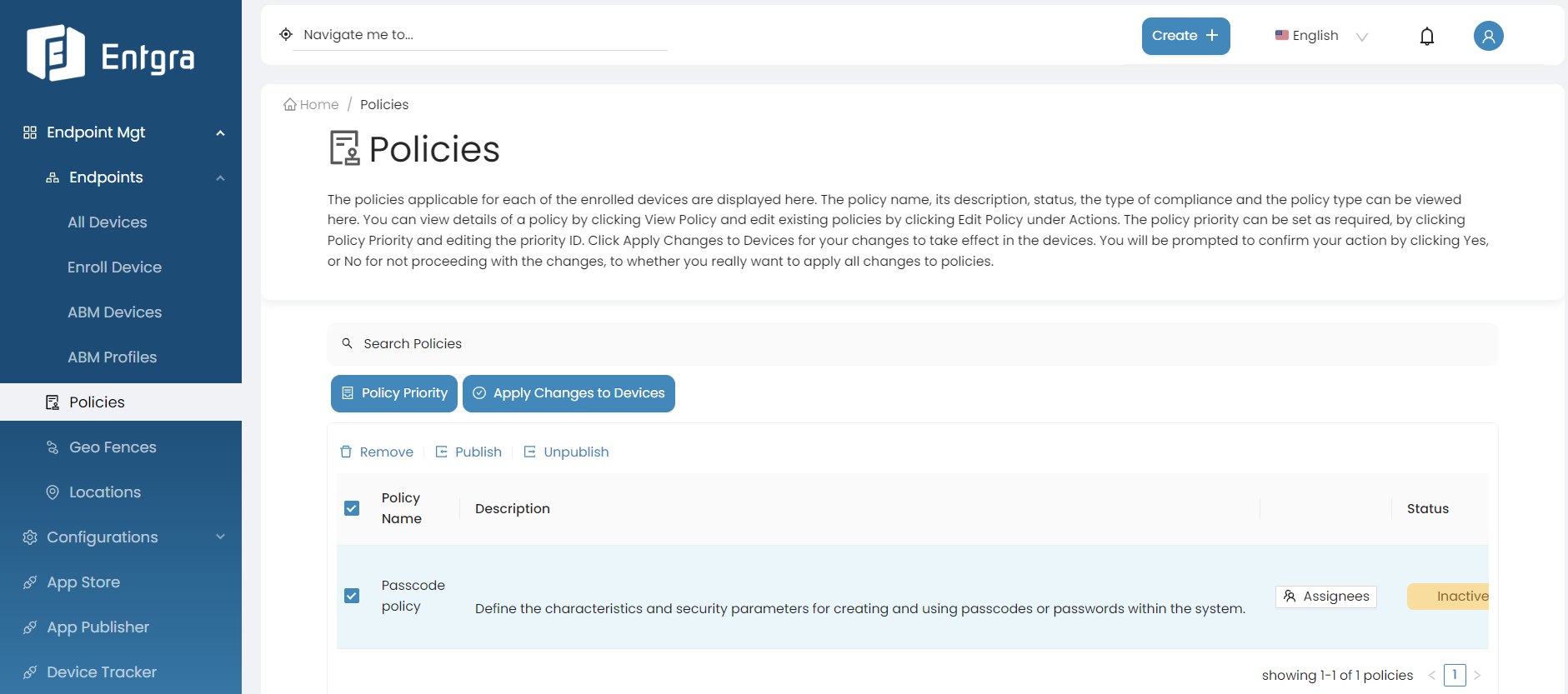
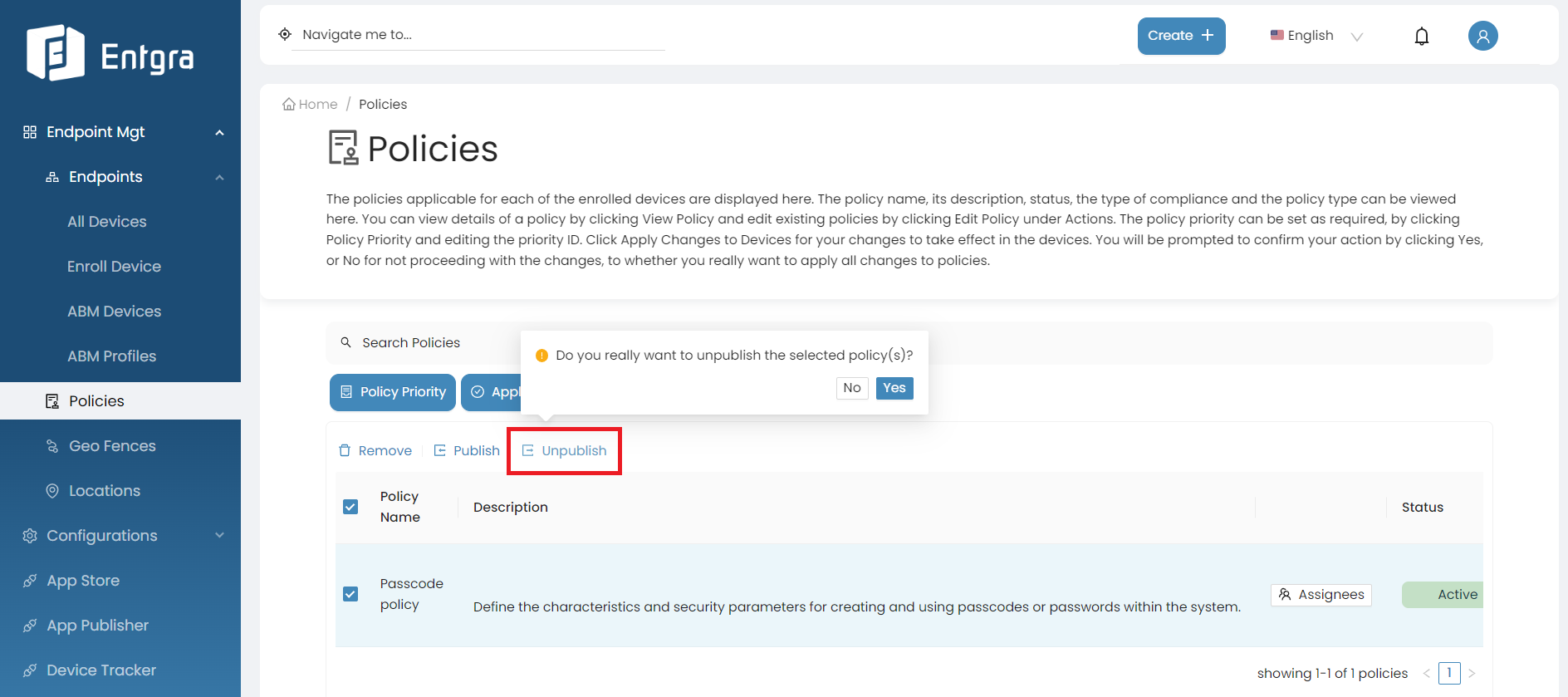
Unpublish Policies
-
Sign in to the Entgra UEM Server console.
-
Click Policies to get the list of the available policies.
-
Select the policy that you wish to unpublish from those that have already been published.
-
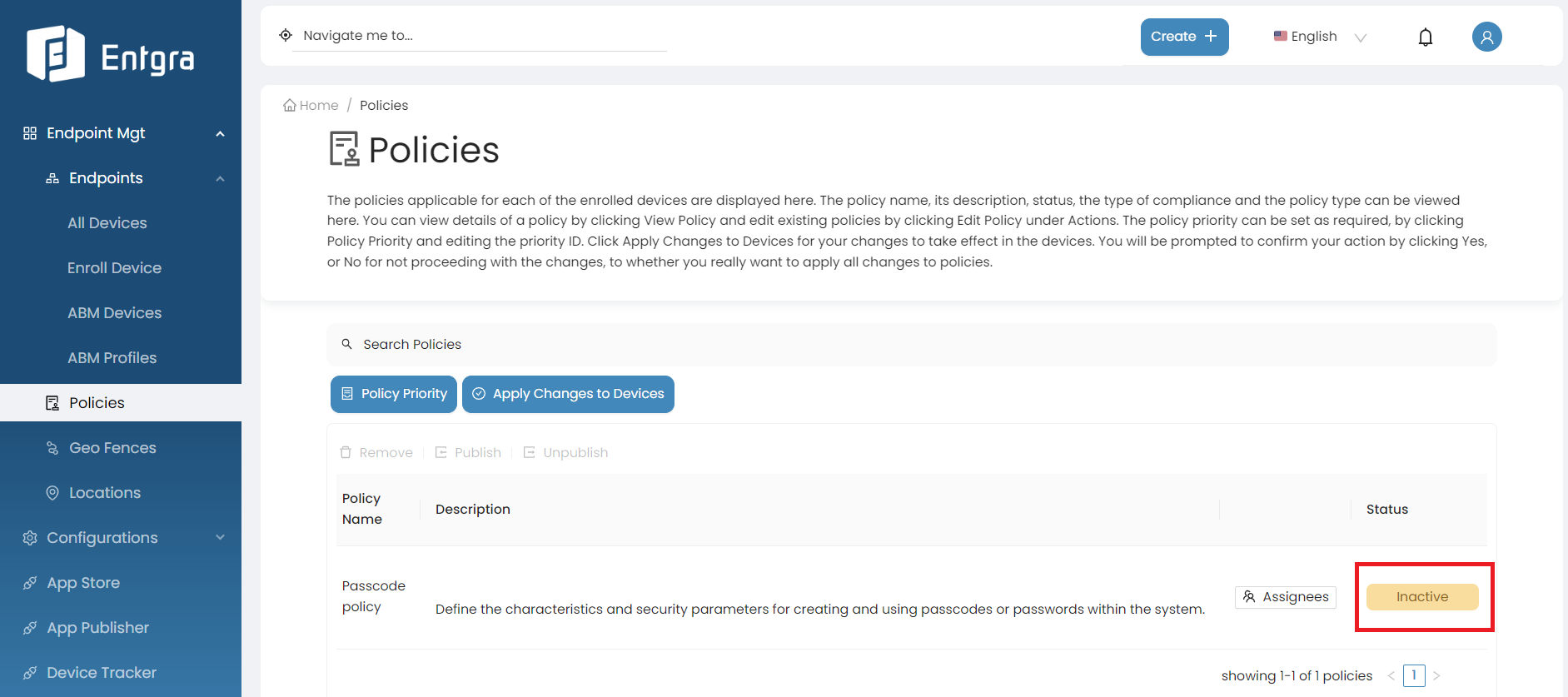
Click Unpublish and Yes to confirm unpublishing the policy.
-
Then click Apply Changes to Devices to apply the policy to the devices.
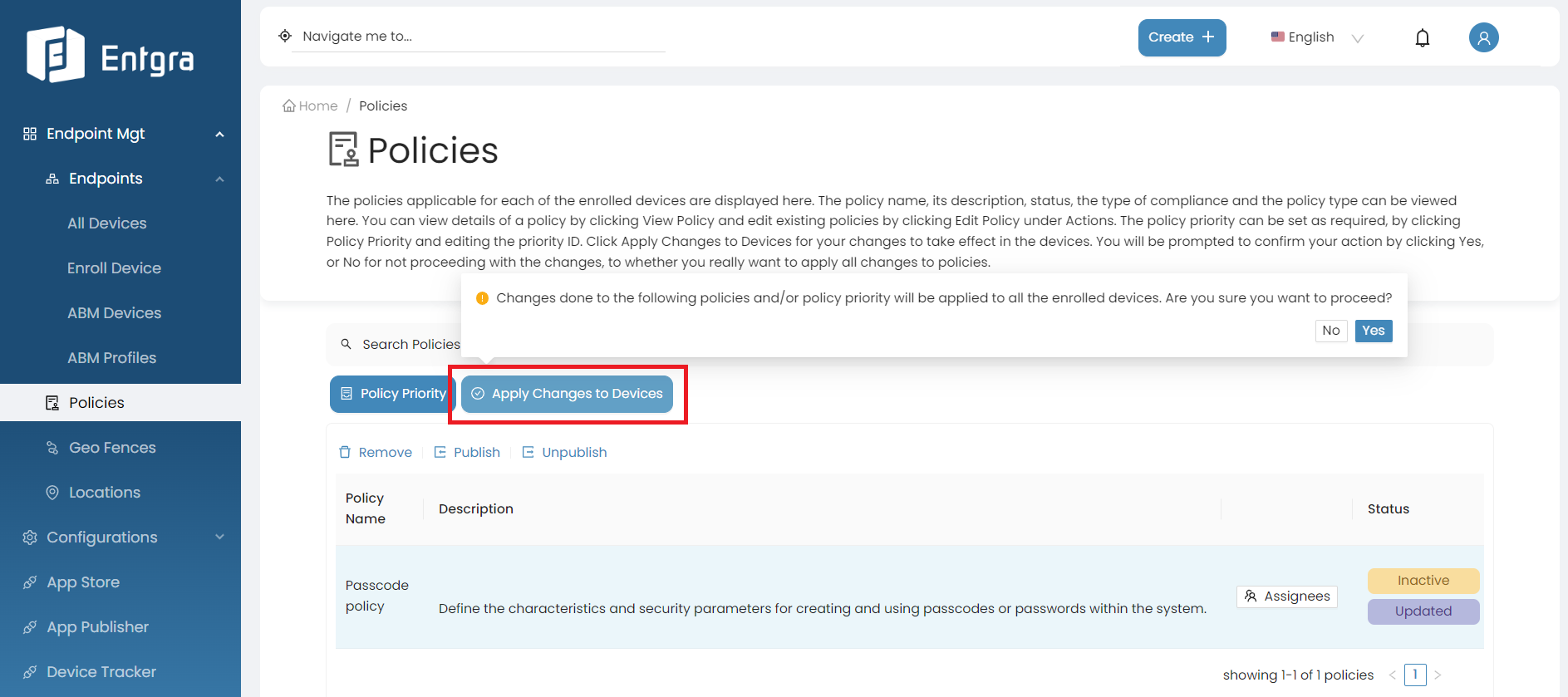
-
The selected policy has now been unpublished and is in inactive state. Therefore, this policy will not be applied on devices that are newly enrolled with Entgra UEM Server.
Verify Enforced Policies
Follow the setps below to verify a policy enforced on a device.
-
Click on your device to view the device details.
-
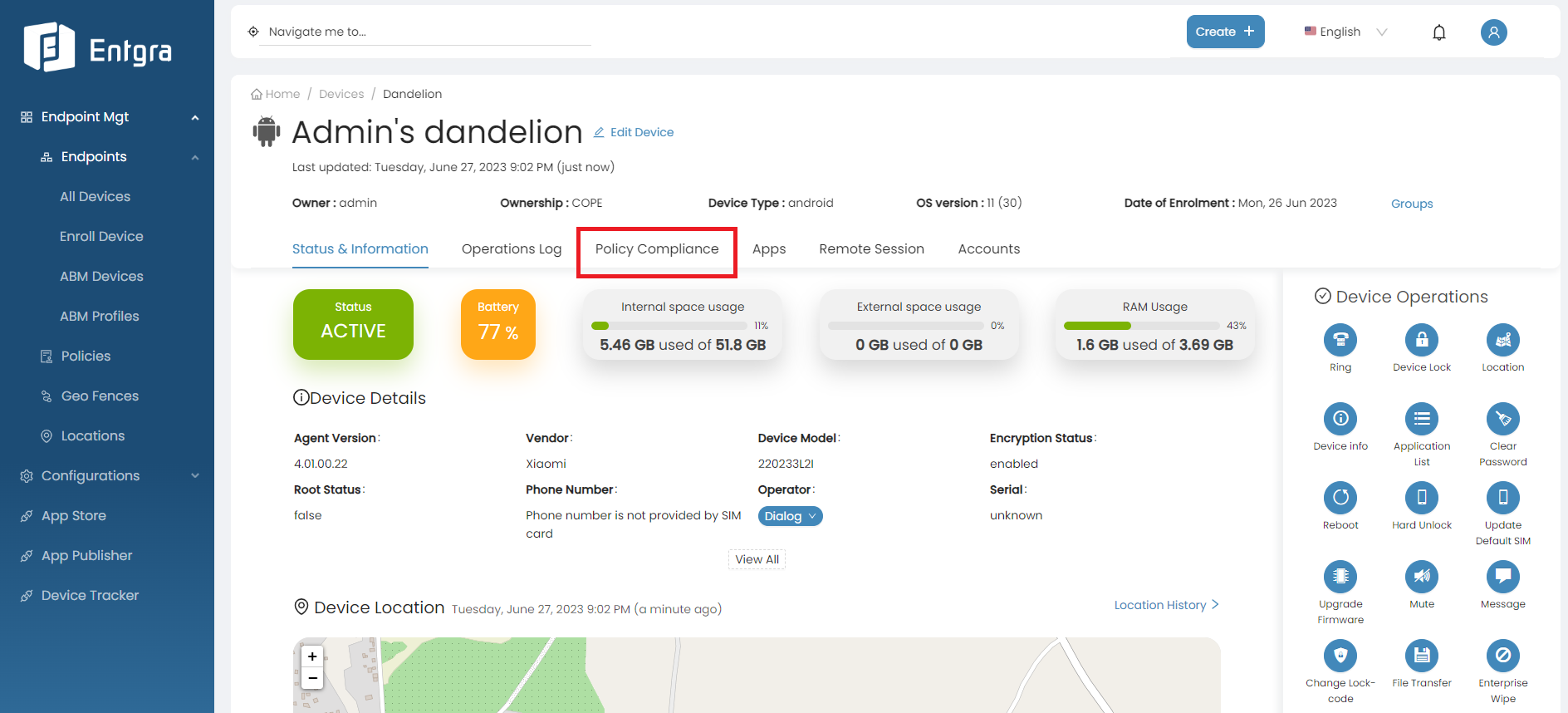
Click Policy Compliance.
-
You can see the policy that is currently applied to your device.
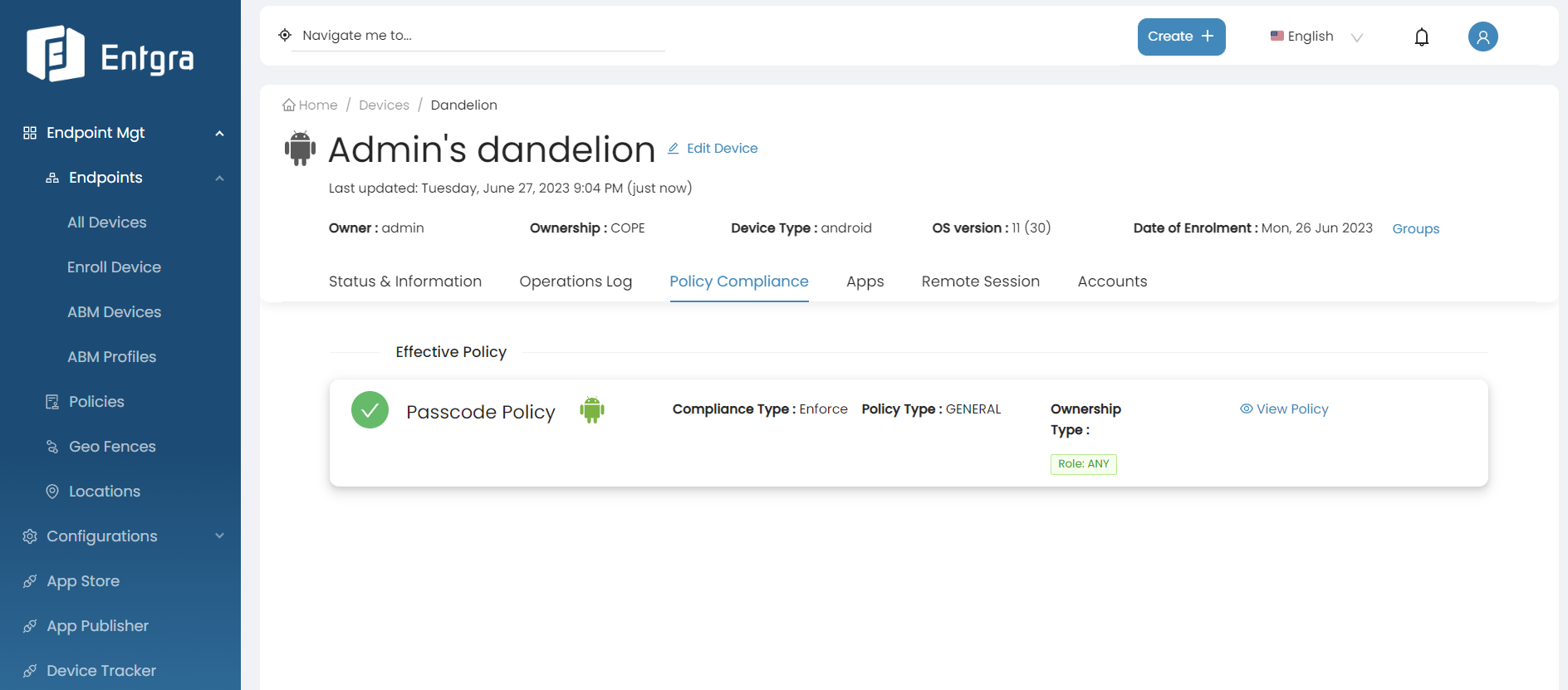
Manage Policy Priority Order
You can change the priority order of applied policies for them to be applied in that order in the devices that are registered with the Entgra UEM Server.
-
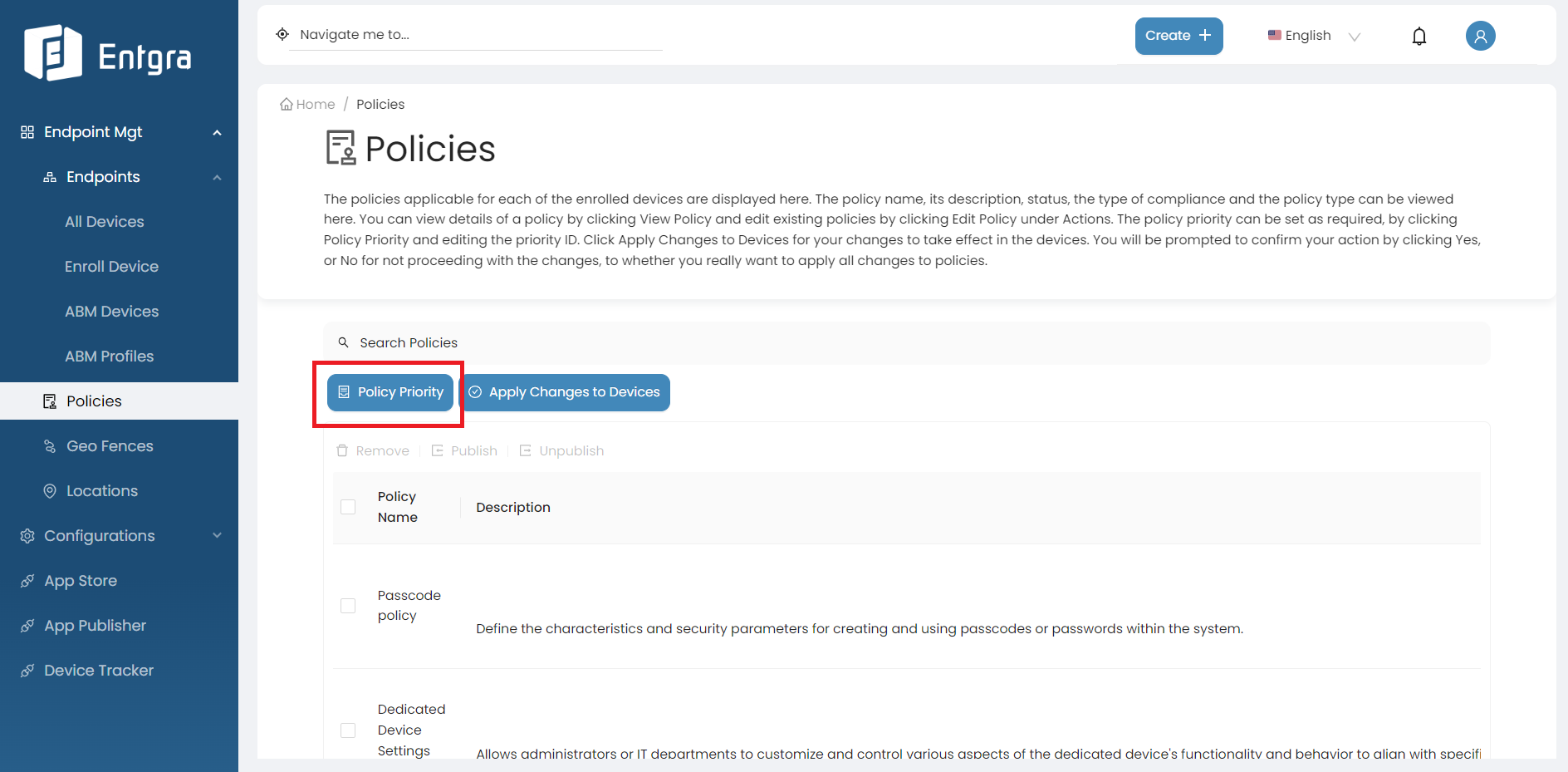
Click Policies to get the list of the available policies.
-
Click Policy Priority.
-
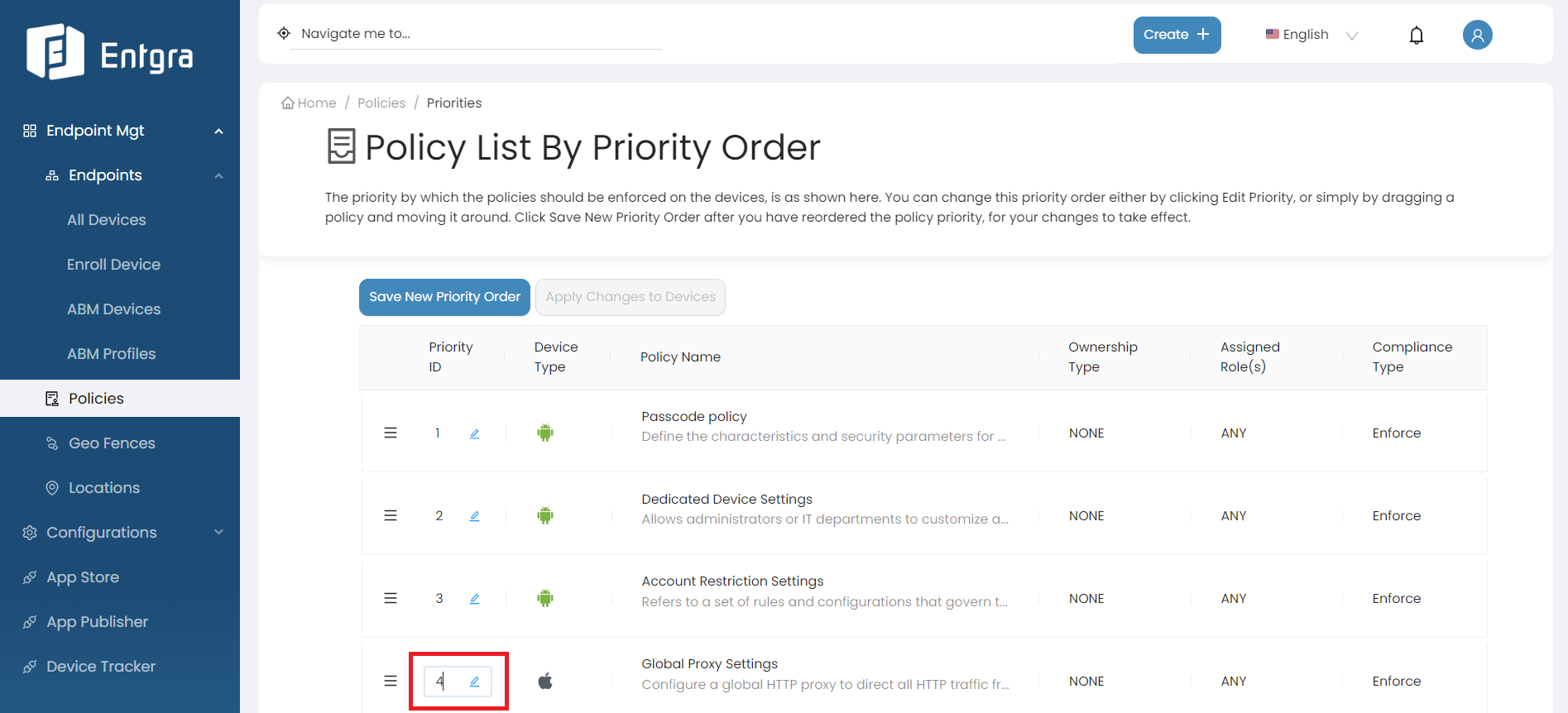
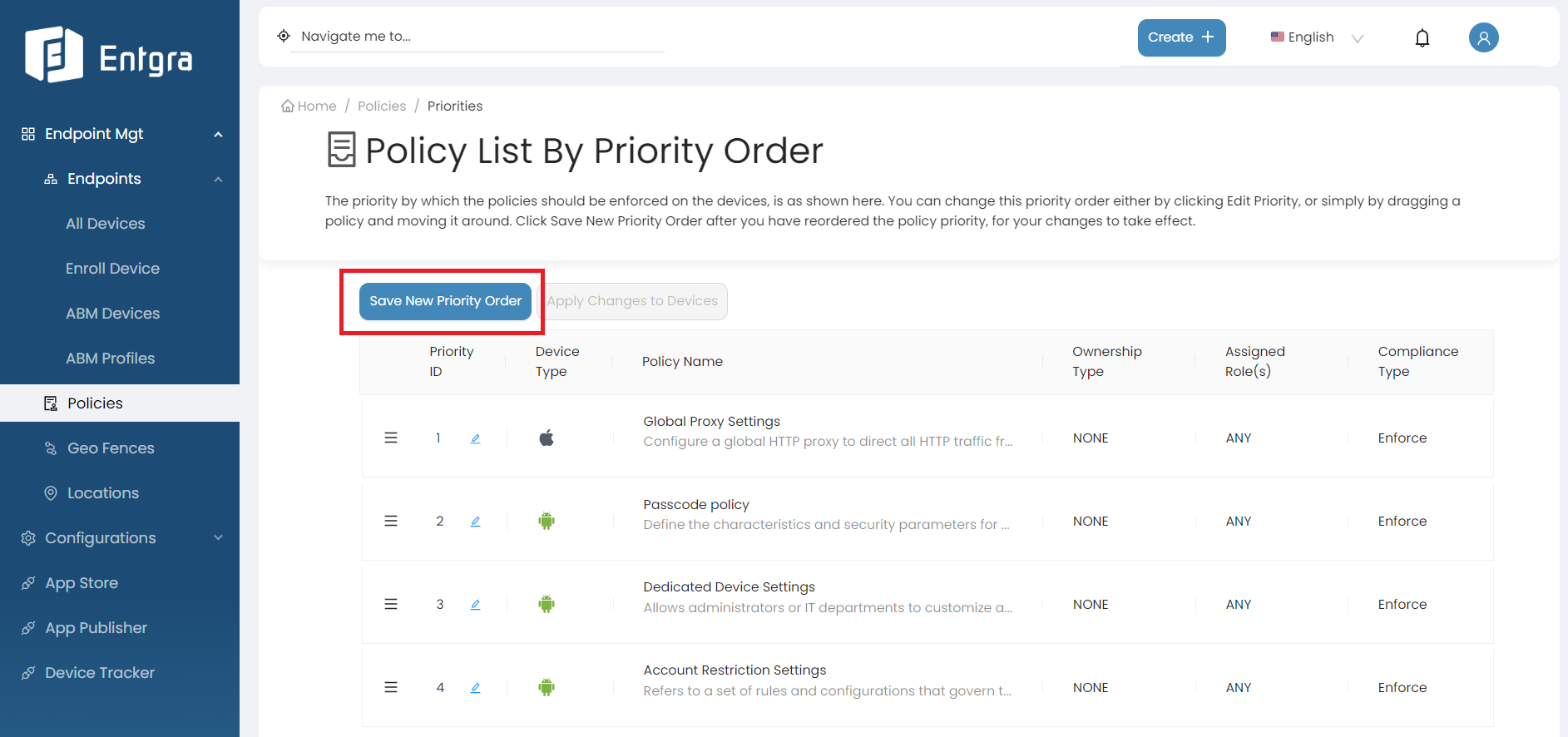
Manage Policy Priority
- Drag and drop the policies to prioritize the policies accordingly.
- Manage the policy priority order by defining the order using the edit box.
- As shown in the image below, if you want to apply Global Proxy Settings policy first to the devices you have to drag that policy to the top of the list or edit the priority id. Then Passcode Policy will be listed as the 2nd policy in the list.
-
Click Save New Priority Order to save the changes.
-
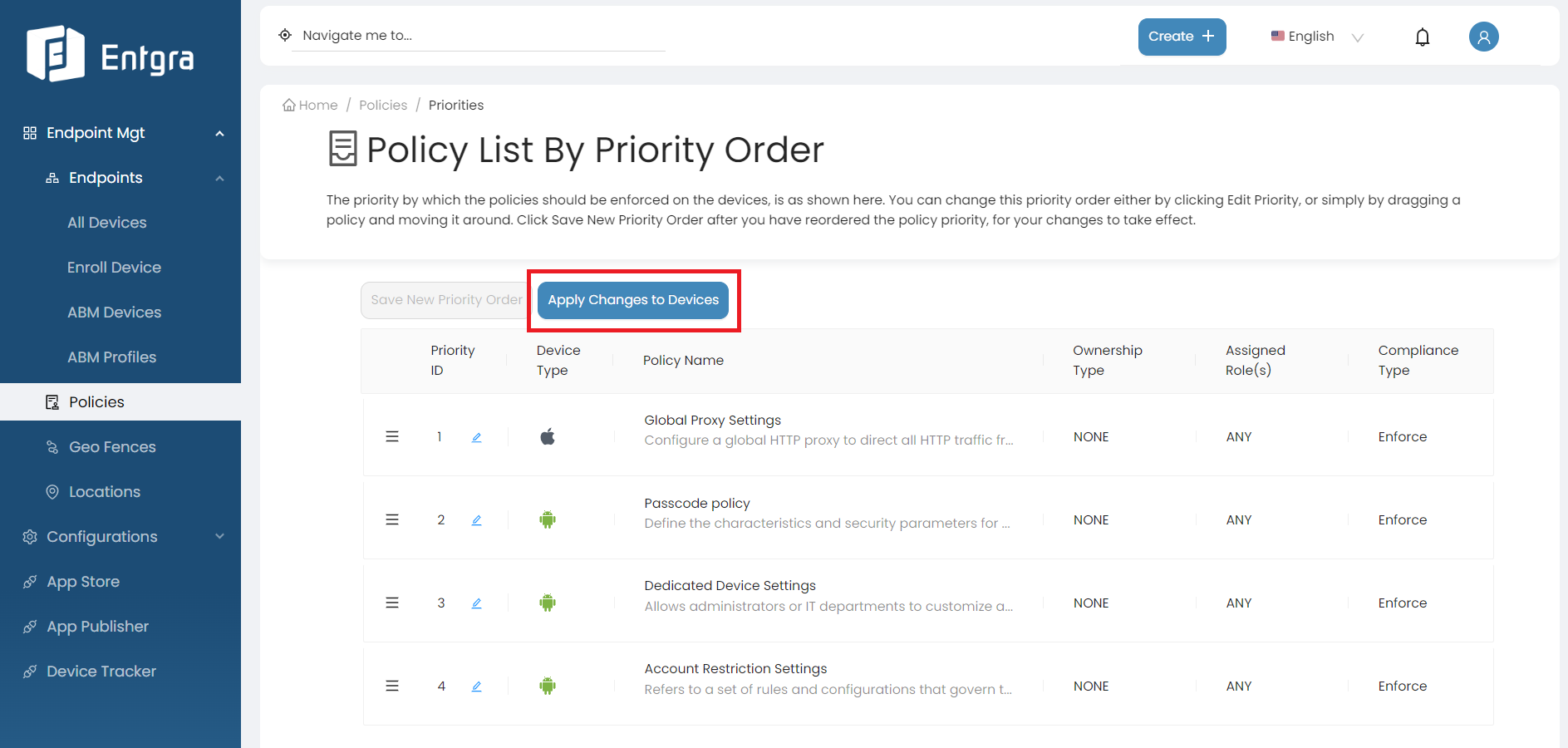
Click Apply Changes to Devices to push the changes to the existing devices.
Update Policies
-
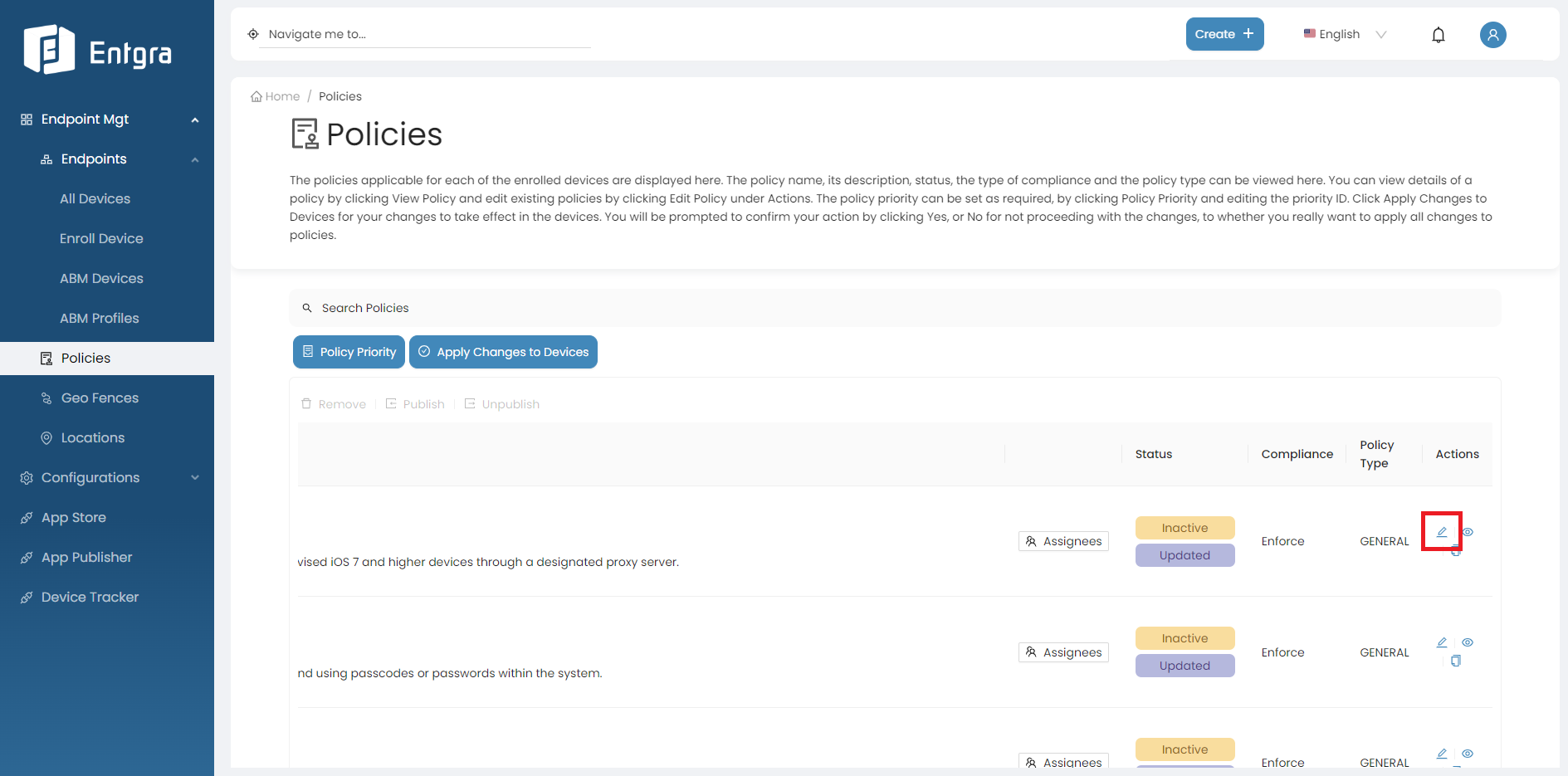
Click Policies to get the list of the available policies.
-
On the policy you wish to edit, click Edit.
-
Edit current profile and click Continue.
-
Select policy type and click Continue.
-
Edit assignment groups and click Continue.
-
Optionally, edit the policy name and description.
-
Click Save to save the configured profile or click Save & Publish to save and publish the configured profile as an active policy to the database.
Android Policies
Allowed Input Methods
The Allowed Input Methods policy lets administrators manage how keyboards and input methods are used on Android devices, reducing the risk of data leaks and keylogging.
Data Keys of Policy and Descriptions
Allowed type of inputs
With this feature, admins have the capability to select one of the following input types:
Allow any input method: All input methods are permitted by default, giving users full freedom to use any preferred keyboard.
Allow only system or default installed: Only trusted pre-installed or system-provided keyboards (like those from the device vendor or Google) are allowed. These keyboards are considered safe and cannot be blocked. Any non-system input method service that is currently enabled must be added to the list. Therefore, if the user has already enabled any input method, it cannot be disabled. System installed and user installed: In addition to the pre-installed and system-provided input methods, administrators can define a set of packages that are permitted as user-installed input methods.
Note: When configuring the Allowed Input Method policy, make sure to include the Entgra keyboard as an authorized input option.
User-installed package names
Administrators can specify a list of package names for input methods that must be allowed and any other user-installed packages will be disabled. System-installed keyboards are trusted by default and cannot be blocked. Default package names for system-installed keyboards do not need to be specified.

Passcode Policy
Enforce a configured Passcode Policy on Android devices. Once this profile is applied, the device owners will not be be able to modify password settings on their devices.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Allow simple value | Permits repeating, ascending and descending character sequences. |
| Allow alphanumeric value | The user must enter a password containing at least both numeric and alphabetic (or other symbol) characters. |
| Minimum passcode length | Set the required number of characters for the password. For example, you can require PIN or passwords to have at least six characters. |
| Minimum number of complex characters | Set the required number of letters, numericals digits, and special symbols that passwords must contain. Introduced in Android 3.0. |
| Maximum passcode age in days ( Should be in between 1-to-730 days or 0 for none ) | Designates the full email address for the account. If not present in the payload, the device prompts for this string during profile installation. |
| Passcode history ( Should be in between 1-to-50 passcodes or 0 for none ) | Number of consequent unique passcodes to be used before reuse |
| Maximum number of failed attempts before device lock | The maximum number of incorrect password entries allowed. If you fail to enter the correct password within the allowed number of attempts, the device will be locked. |
| Maximum number of failed attempts before device reset | Specifies how many times a user can enter the wrong password before the device wipes its data. The Device Administration API also allows administrators to remotely reset the device to factory defaults. This secures data in case the device is lost or stolen. |
| Time to auto lock seconds | Time it takes in seconds for the device to lock automatically when idle. |
Passcode Policy for Work Profile
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Enabled Work profile passcode | Enable a passcode for work profile |
| Allow simple value | Permits repeating, ascending and descending character sequences. |
| Allow alphanumeric value | The user must enter a password containing at least both numeric and alphabetic (or other symbol) characters. |
| Minimum passcode length | Set the required number of characters for the password. For example, you can require PIN or passwords to have at least six characters. |
| Minimum number of complex characters | Set the required number of letters, numericals digits, and special symbols that passwords must contain. Introduced in Android 3.0. |
| Maximum passcode age in days ( Should be in between 1-to-730 days or 0 for none ) | Designates the full email address for the account. If not present in the payload, the device prompts for this string during profile installation. |
| Passcode history ( Should be in between 1-to-50 passcodes or 0 for none ) | Number of consequent unique passcodes to be used before reuse |
| Maximum number of failed attempts before device lock | The maximum number of incorrect password entries allowed. If you fail to enter the correct password within the allowed number of attempts, the device will be locked. |
| Maximum number of failed attempts before device reset | Specifies how many times a user can enter the wrong password before the device wipes its data. The Device Administration API also allows administrators to remotely reset the device to factory defaults. This secures data in case the device is lost or stolen. |
| Time to auto lock seconds | Time it takes in seconds for the device to lock automatically when idle. |
Android Policy Restrictions
The Restrictions Policy for Android devices enables restricting specific settings on the device. Once the profile with these configurations is installed on the device, the user is unable to modify those settings on his/her device.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Allow use of camera | Selecting this feature enables the device to use camera. |
| Disable/Block Configuring VPN | This restriction blocks configuring VPN settings. To test this under Work Profile enrollment, download a free VPN app, for example “turbo VPN” from play store and try to create a VPN connection. The application will show an error. |
| Disable/Block Cross Profile Copy-Paste | This feature disables text copy-pasting between Enterprise profile and the regular profile. To test how this works, you can go to an app where you can type text. For example, in the Google Playstore’s search box. Type some text and copy it. Next, try pasting the copied text into another app on the phone which is not a part of the Enterprise profile container. The text will not be available. Remove the policy and retry. |
| Disable/Block Debugging | This feature blocks the ability to debug any application through the Android studio. |
| Disable Installing Apps | Disables installing apps from the Google Play Store. |
| Disable Installing from Unknown Sources | Install a browser such as chrome in the work profile and try to install an apk file from untrusted source such as (https://github.com/selendroid/selendroid/raw/master/selendroid-standalone/src/test/resources/selendroid-test-app.apk). This will be prevented by the OS. |
| Disable Modifying Accounts | Go to Settings -> Cloud and accounts -> accounts Under work, Add account will be disabled. Also if you go inside the existing Google account of the enterprise profile and click on the 3 dot menu on the top right corner, and the remove button will be disabled. |
| Disable Outgoing Beams | This is related to NFC beams. Install an NFC app that sends some information to another. for example NFC contacts application into the work profile and try to send NFC beam to another NFC enabled device. |
| Disable Location Sharing | This restriction disables turning on location sharing. Under settings -> location -> the work profile and regular profiles location control is available. |
| Disable Uninstalling Apps | This restriction disables turning on location sharing. Under settings -> location -> the work profile and regular profiles location control is available. |
| Disallow parent profile app linking | Allows apps in the parent profile to access or handle web links from the managed profile. |
| Disallow set wallpaper | Selecting this disables the abilty of the user to change the wallpaper. |
| Disallow set user icon | Selecting this, disables the user to change the user icon. |
| Disallow remove managed profile | If you try to remove the managed profile, it will not be enabled if this feature is selected. |
| Disallow bluetooth | Bluetooth function will be disallowed on the device. |
| Disallow bluetooth sharing | Sharing data using bluetooth will be disabled by this feature. Following set of restrictions require the device to be in device owner mode. Follow the documentation to get the device into device owner mode. |
| Ensure verifying apps | In settings, go to Google -> Work -> Security -> Verify apps -> Scan device for security threats is not configurable. |
| Enable auto timing | Search for automatic date and time in settings of the device and enabling/disabling this setting is controlled by this setting. |
| Disable screen capture | This will disable the ability to take screenshots by pressing the power key together with volume down. |
| Disable SMS | The user will not be allowed to send or receive SMS. |
| Disable Volume Adjust | This will disable the ability changing device volume. so the volume keys must not have an effect. |
| Disable Cell Broadcast | Disables cell broadcasting messages (message -> Settings -> Cell Broadcast). |
| Disable Configuring Bluetooth | This restriction will disable the Bluetooth settings in settings of the device. |
| Disable Configuring Mobile Networks | Under settings -> mobile networks -> mobile configurations menu disabling is achieved with this configuration. |
| Disable Configuring Tethering | This will disable the ability to configure mobile hotspots and tethering which is found in settings. |
| Disable Configuring WiFi | Disable the ability to configure wifi settings in device settings. |
| Disable Safe Boot | Disables the ability to safe boot a device to remove any apps installed. https://support.t-mobile.com/docs/DOC-34283 |
| Disable Outgoing Calls | The user is not allowed to make outgoing phone calls. Emergency calls are still permitted. |
| Disable Mounting Physical Media | The user is not allowed to mount physical external media. If you connect a pendrive to the device via the OTG cable, the device will not allow mounting the pendrive. |
| Disable Factory Reset | Disables the ability to factory reset the device. If you go to settings on the device, the factory reset will be disabled. |
| Disable Remove User / Disable Add User | Multiple user profile control. The users are not allowed to remove or add. This may not be available in some Android devices. |
| Disable Network Reset | This restriction will disable network resetting. To check, type “reset network settings” in the settings search bar and the reset settings will be disabled. |
| Disable USB File Transfer | This restriction disables file transfer via USB. |
| Disallow data roaming | This feature disables the ability to use data while roaming. |
| Enable device backup service | By selecting this you can enable the device backup service. |
| Disallow disable mobile data | By selecting this feature the user will not be able to disable mobile data on the device. |
| Disallow airplane mode | User is disallowed from enabling or disabling location. To test this restriction on the device, go to the location in the settings. There the use location turn on button will be disabled and the location accuracy part will be disabled. This restriction is applicable when the agent is the device owner and Android version 9.0 (Pie) or higher. |
| Disable Unmute Microphone | This restriction will disable the microphone. Check the device microphone by using a recording app. This restriction is applicable when the agent is the device owner and Android 6.0 Marshmallow onwards only. |
| Disallow config location | This restriction disables the user from configuring the location. |
| Disallow changing default SIM card | This restriction disables the user from changing the default SIM card. |
| Force uninstall applications is not allowed | When enabled, you cannot force uninstalling of the apps in the allowed-apps list, under the Global Configurations for All Apps -> App Availability to a User -> Only Allow listed Apps. |
Disable Creating Window
Apps running are not allowed to create following types of windows.
LayoutParams#TYPE_TOAST LayoutParams#TYPE_PHONE LayoutParams#TYPE_PRIORITY_PHONE LayoutParams#TYPE_SYSTEM_ALERT LayoutParams#TYPE_SYSTEM_ERROR LayoutParams#TYPE_SYSTEM_OVERLAY LayoutParams#TYPE_APPLICATION_OVERLAY
To test, have an application that creates a toast and for example in the VPN app, when the VPN is created a toast may be shown and this must be Disableed with this setting.
Disable/Block Configuring Credentials
This configuration blocks the user from being able to configure credentials in the security certificates. In order to test this under Work Profile enrollment, enforce this policy on the device. Then go to device settings.
- Search for certificates, and click View Security Certificates.
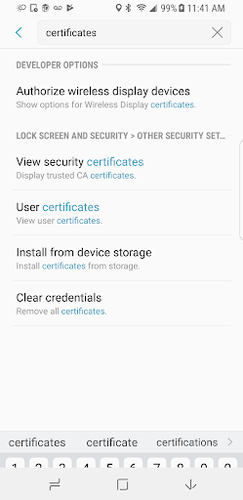
2. If you tap on certificates under personal, a pop-up will appear allowing you to turn off a certificate.
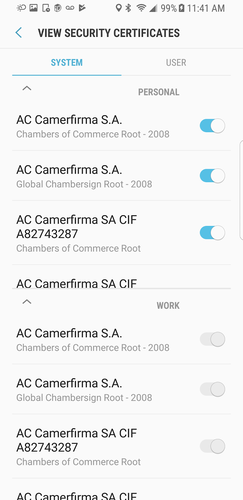
3. Since the policy is applied under Work Profile enrollment, the turn-off button is disabled/not visible.
Disable/Block Configuring App Control
Specifies if a user is blocked from modifying applications in Settings or launchers. The following actions will not be allowed for the user when this restriction is enforced:
-
Uninstalling Apps
-
Disabling Apps
-
Clearing App caches
-
Clearing App Data
-
Force Stopping Apps
-
Clearing App Defaults
After applying the policy, try to remove an installed app, for example the VPN client from the device, and it will not work.
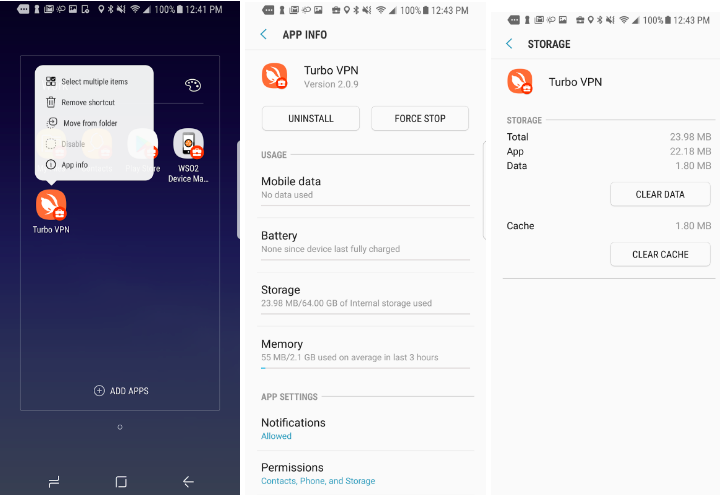
In the first image, uninstall is disabled, and the second image is from Settings -> Apps -> Installed App. Click Uninstall or Force Stop, or under application’s storage, click Clear Data or Clear Cache. The policy will prevent you from doing so.
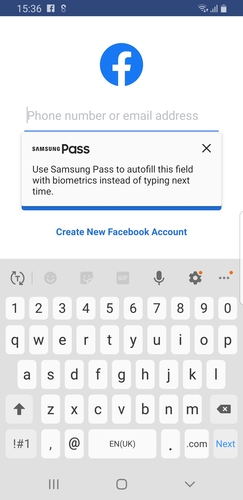
Disable Autofill
This restriction will disable autofill services.To check, install a application that needs to enter user credintials to log in. when entering the credintials, device autofill service will ask to save credincials to autofill service (samsung devices uses samsung pass as default).After when this restiriction active,this auto fill service will be disabled.
Disable status bar
This restriction will disable the device status bar.
Dedicated Device Settings
This policy can be used to configure the profile of dedicated devices, such as for use in kiosk mode.
Restrict Device Operation Time
The device will be operable only during the time period specified below.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Start Time | Start time for the device |
| End Time | Lockdown time for the device |
Device Global Configuration
Theme can be configured with the following options.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Allowed COSU(KIOSK) Applications | Specify an applications list to be displayed on the kiosk launcher. |
| Launcher background image | This is the image that will be displayed in kiosk background. [Should be a valid URL of jpg or jpeg or png] |
| Company logo to display | Company logo to display in the kiosk app drower. [Should be a valid URL ending with .jpg, .png, .jpeg] |
| Company name | Name of the company that has to appear on the agent. |
| Is single application mode | This configuration allows the user to enroll a single application on Kiosk mode task. If the user selects more apps it will get the top most applications. The selected initial app in the Enrollment Application Install policy config will be selected for single application mode. At least one application should be selected. If more than one application is selected, then the first selected application in the list will be installed in the single application mode. |
| Is application built for Kiosk | Enable if the lock task method is called in the application. |
| Is idle media enabled | This Configuration allows the user to display idle timeout video on the device. |
| Media to display while idle | Url of the media to display while the device is idle. (Should be a valid URL ending with .jpg, .png, .jpeg, .mp4, .3gp, .wmv, .mkv) |
| Idle graphic begin after(seconds) | Idle graphic begin after the defined seconds. |
| Keep display awake | Selecting this feature will keep the display on without a timeout. |
| Enable Device Info | When enabled, an info button will be available in kiosk mode to display the device information data of the device. |
| Enable Notification Panel | Enable notifications during LockTask mode, showing icons, heads-up notifications, and the expandable notification shade. |
| Is multi-user device | If Is multi-user device enabled, multi-user configuration can be done for one device. Which enables to registration of already installed applications for registered users. After the policy is applied these applications can only be executed by logging in as the registered user. Other than this common applications which are common to all the users also can be specified by this policy. |
| Is login needed for user switch | If this is enabled, the user should have valid user name and password to login to the device. |
| Primary User Apps | The Primary User is the user to whom the device is enrolled. The applications that are specified here will be available by default. These applications can be used by any user. Provide comma separated package name or web clip details for applications. eg: com.google.android.apps.maps, |
| Device display orientation | The display orientation of device can be set in a fixed mode. You can select either Auto, Portrait or Landscape. |
Application Restriction Settings
Application Restriction Settings allow administrators to control which apps are allowed or blocked on managed devices. This feature includes two main options: App Block Listing and App Allow Listing, both providing precise control over app access.
App Block Listing
App Block Listing allows administrators to specify applications that are not permitted on managed devices. This setting helps organizations restrict access to non-essential or high-risk applications.
Steps
- In Select a Type, choose Block List from the dropdown menu.
- Click Add under the Restricted Application List.
- In the table, use the dropdown on the left to select either App Name or Package Name.
- Enter the App Name or Package Name of the application you want to restrict.
- To block additional applications, click Add again and enter the details for each application.
- Click Continue and complete the policy setup as required.

App Allow Listing
App Allow Listing restricts device access to only the applications specified by the administrator. This approach is ideal for organizations with strict usage policies, ensuring that only approved applications are accessible.
Configuring the Restricted Application List
- App Allow Listing requires a specific platform configuration, where administrators define a list of application package names. This list should only include non-system applications and applications that are not critical for system functionalities.
- When the Application Restriction Settings policy calculates which applications should be allow-listed on a device, all applications in the list (except those included in the allow list) are always considered blocked. The reason for this is that certain OS-level applications should not be disabled while allow-listing as those apps are critical to the operation of the device.
Steps
- In the left-side navigation menu, select Platform under the Configurations section.
- Expand the Android Configuration section and click on Policy.
- In the Restricted Application List input field, enter a comma-separated list of application package names.

Creating the Allowed List
Steps
- In Select a Type, choose Allow List from the dropdown menu.
- Click Add under the Allowed Application List.
- In the table, use the dropdown on the left to select either App Name or Package Name.
- Enter the App Name or Package Name of the application you want to allow.
- To allow additional applications, click Add again and enter the details for each application.
- Click Continue and complete the policy setup as required.

Further explore this feature by referring to our comprehensive blog article
Account Restriction Settings
This policy enables users to specify the types of accounts that are permitted on the device and the number of accounts per type. Only the accounts indicated here will remain on the device, and others will be removed automatically.
To activate the policy, follow the steps below:
-
Go to Policies > Add Policy > and click Account Restriction Settings.
-
Set the toggle to ON to configure the permissable account types.
-
Click Add under Allow Account List, and add the accounts allowed on the device.
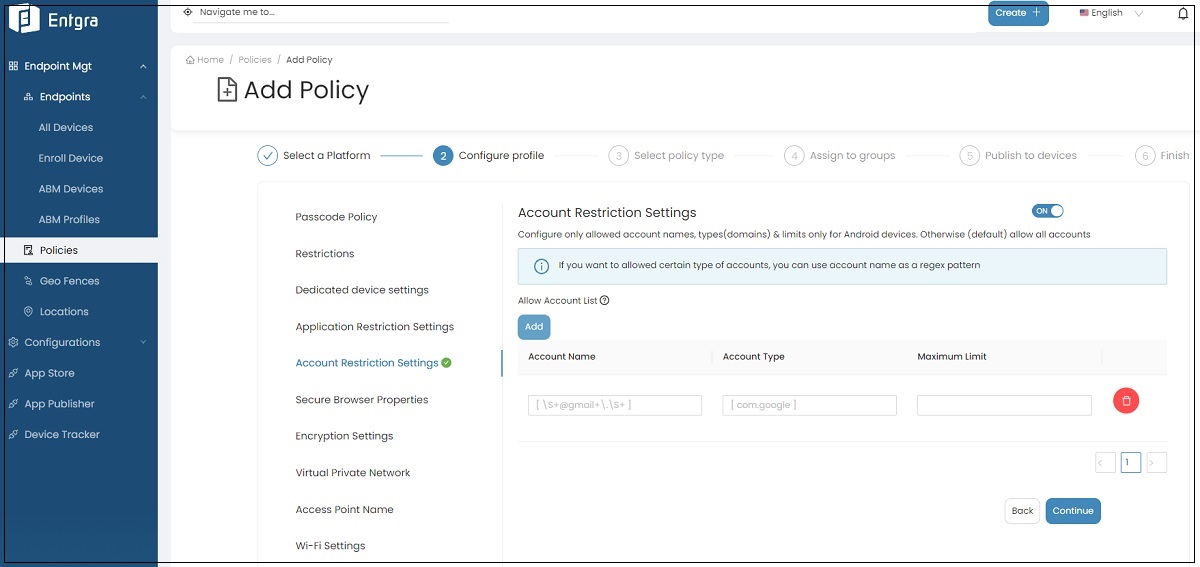
-
Configure the allowed account names, types (domains) and the maximum number of accounts allowed for the specified type.
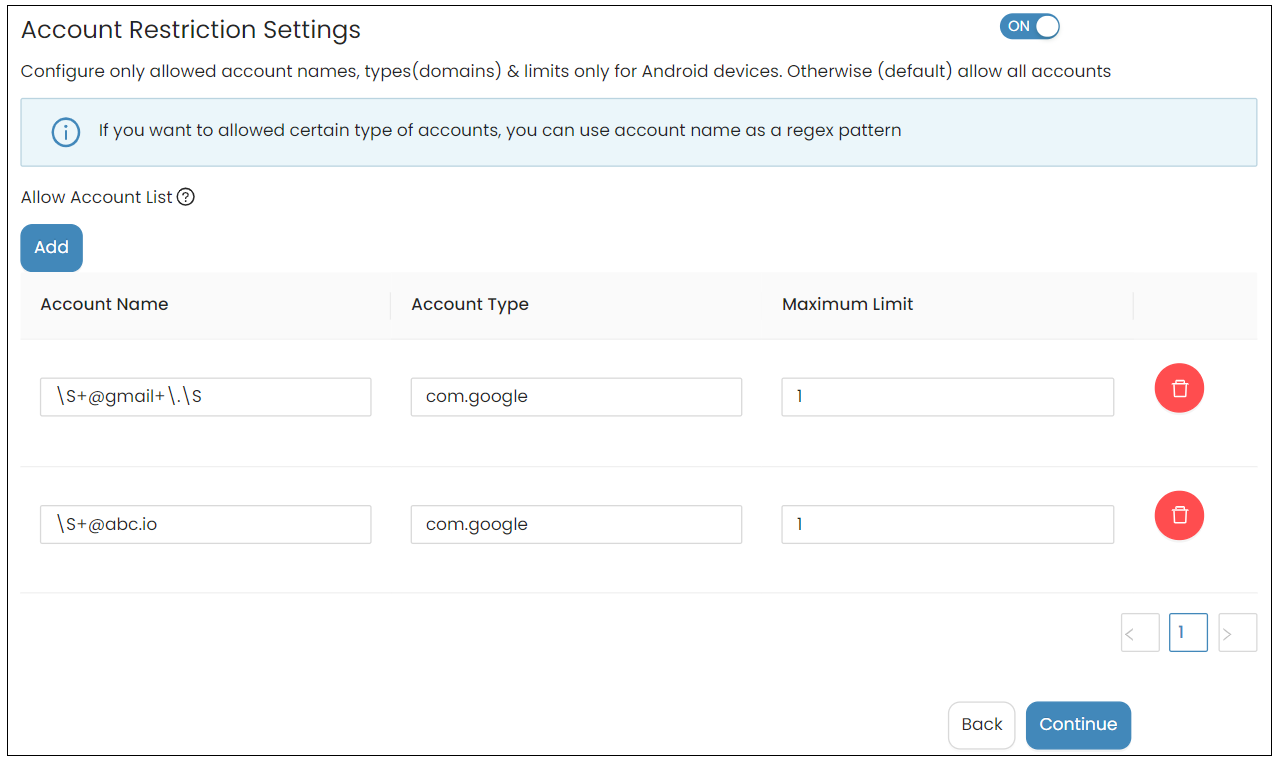
-
Click Continue when all configurations have been entered.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Account name | Name of the account. Full account name can be added, but if a similar pattern or type of accounts have to be specified, a regex pattern can be used. |
| Account type | Specifies the type of account. |
Limitations:
- Users must ensure that there are no conflicts when using multiple conditions for the same type of accounts with a regex pattern.
- This policy is only applicable for COPE devices.
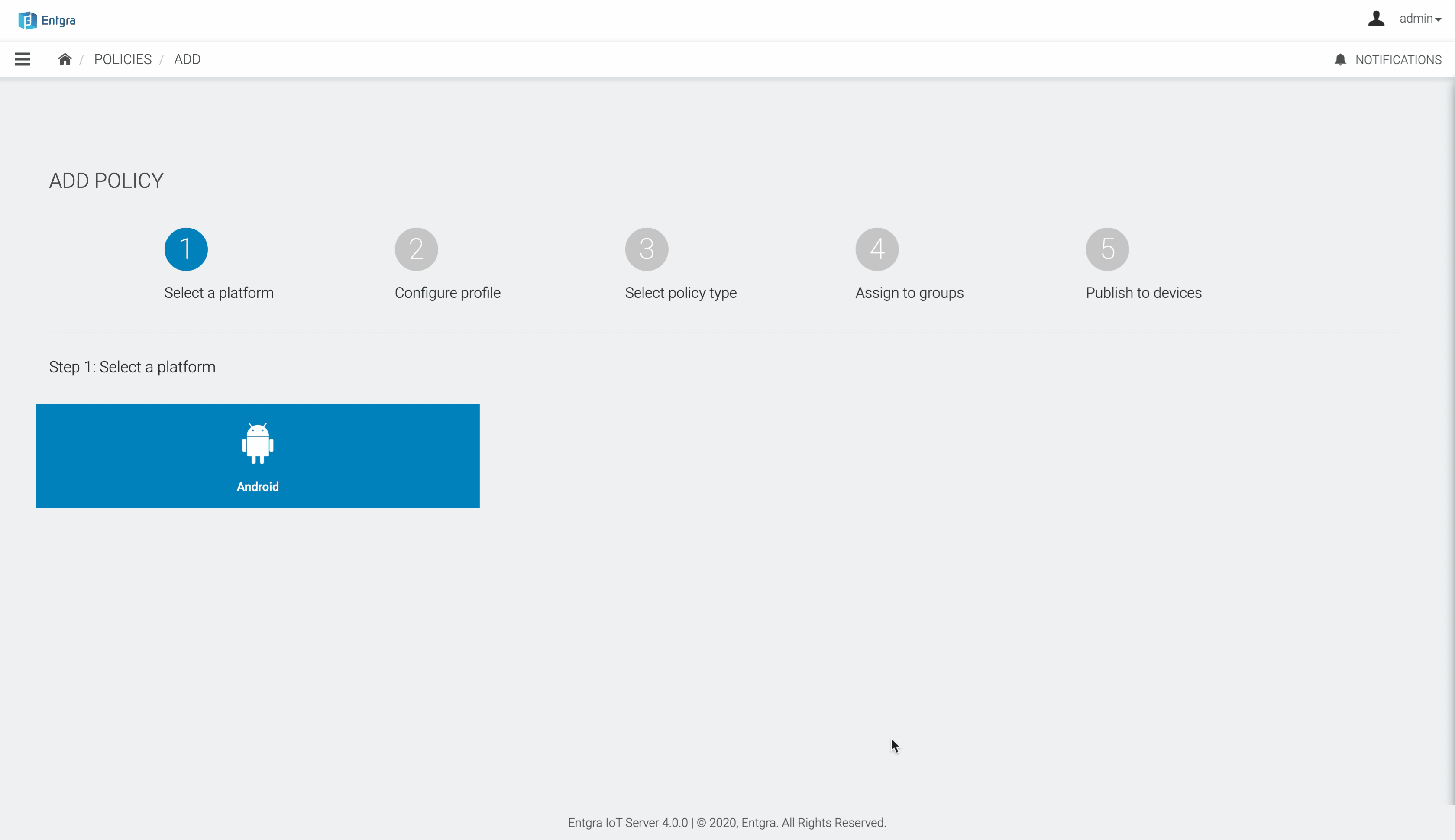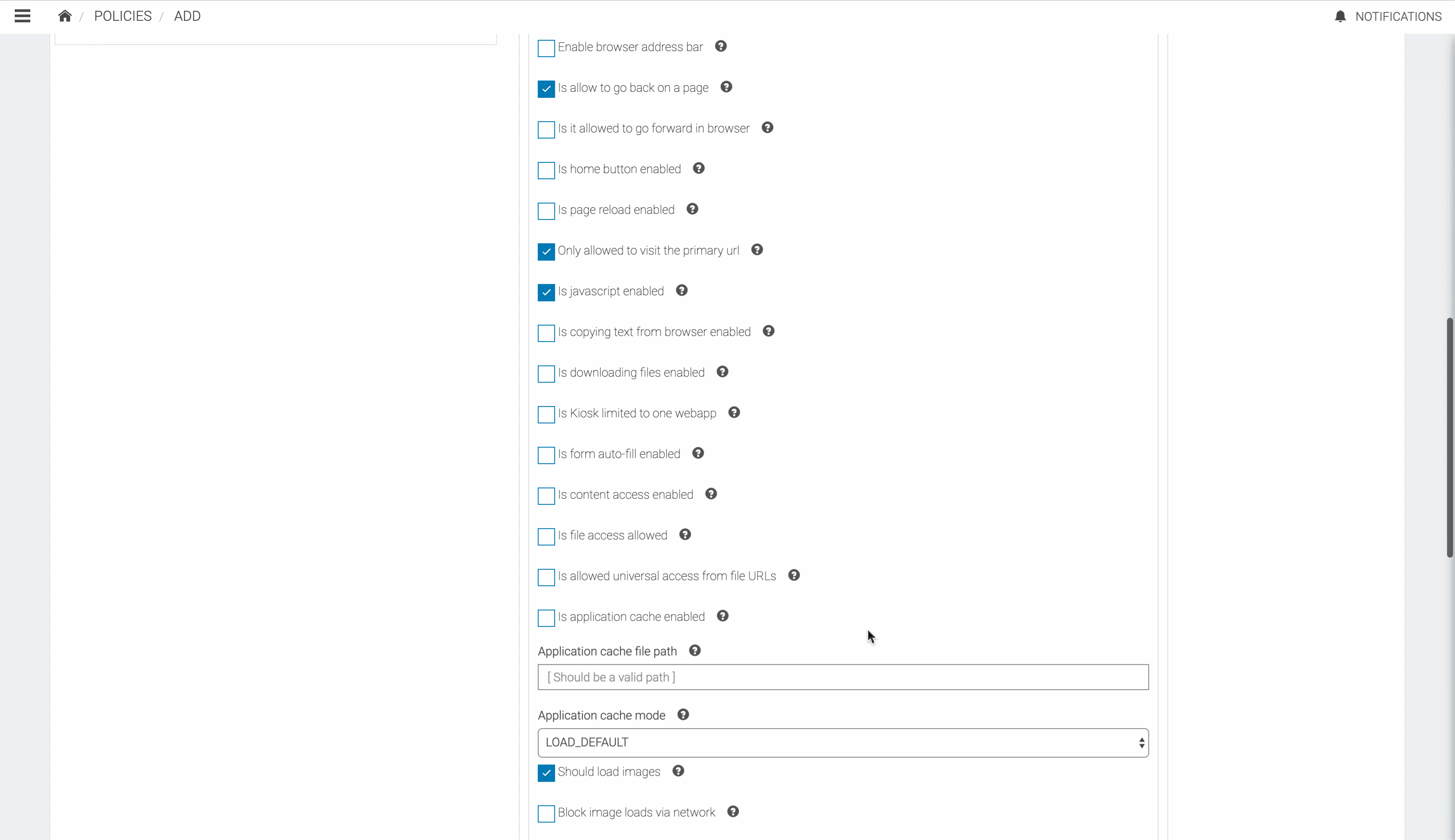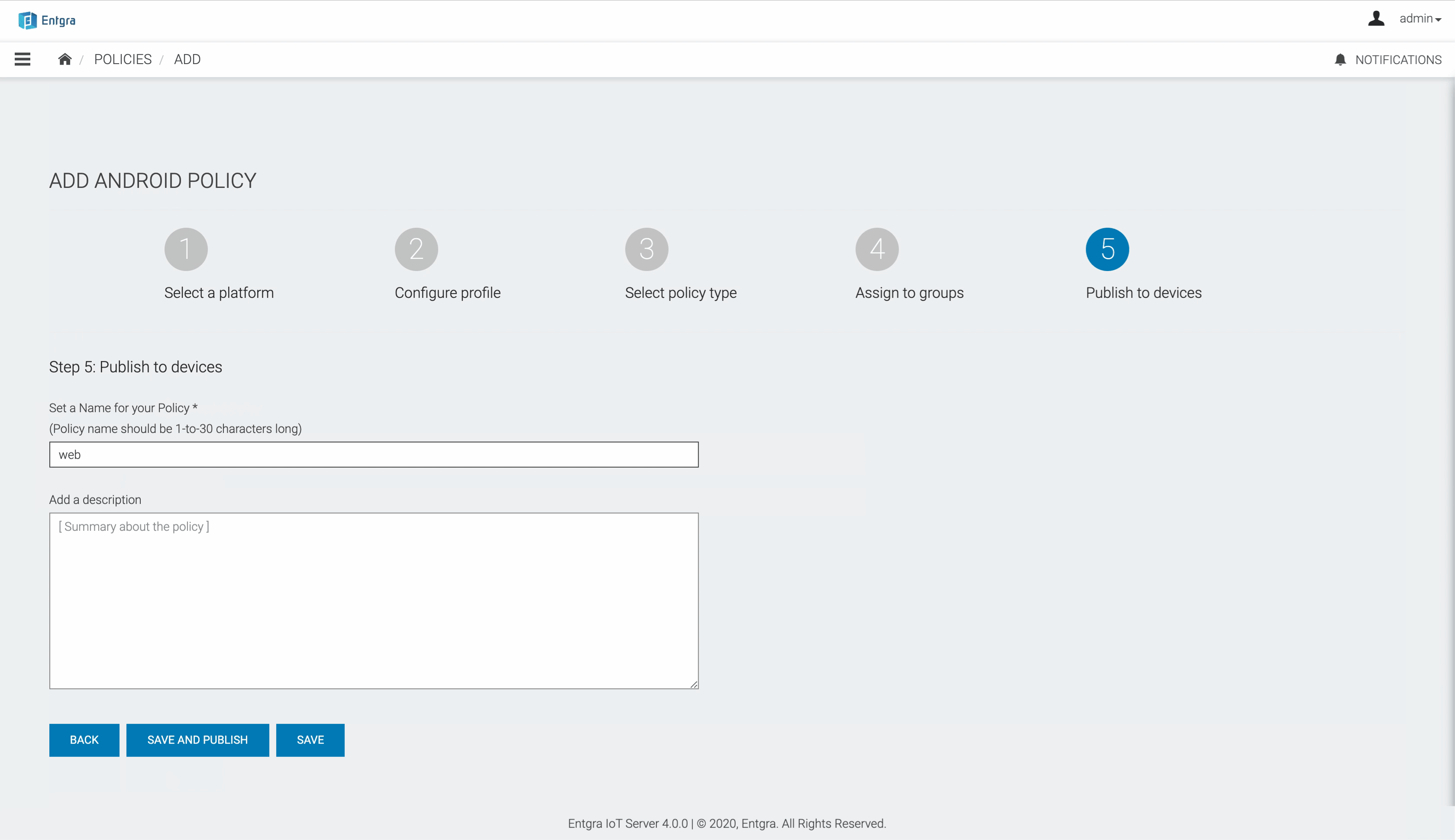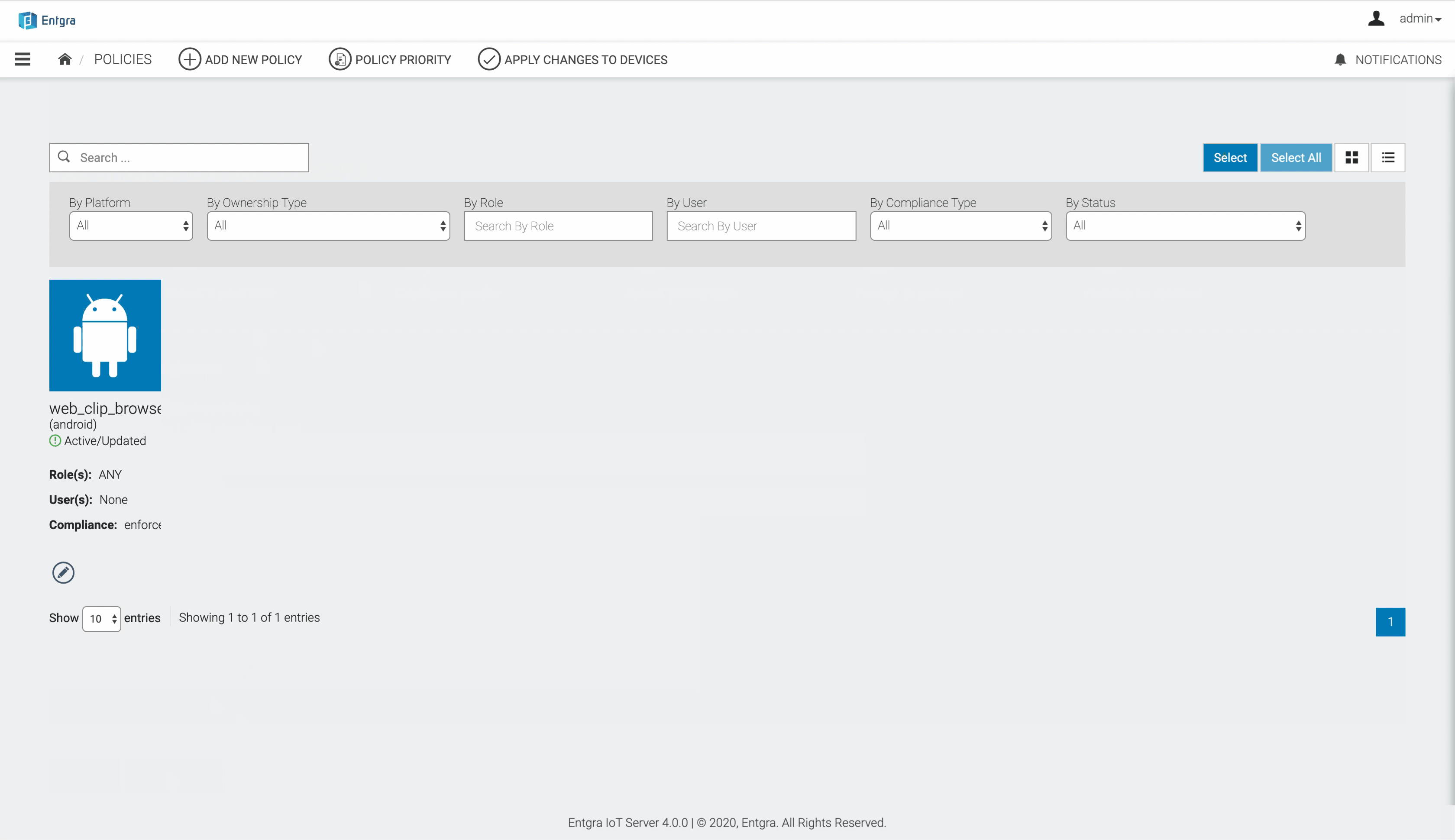
Secure Browser Properties
This is used to restrict properties of the web browser when using web views.
| Data Key | Description |
|---|---|
| Primary URL | Primary URL of the web view |
| Enable top control bar | Enables top control bar that displays all the controllers such as address bar, home button and forwards controllers. |
| Enable Browser Address Bar | Enables address bar of the browser. |
| Is allowed to go back on a page | Enables to go back on a page. |
| Is allowed to go forward on a page | Enables to go forward on a page. |
| Enables the home button on the browser. | |
| Is page reload enabled | Enables page reload. |
| Only allowed to visit the primary url | Disables visiting URLs other than the primary url. |
| Is javascript enabled | Enables loading of javascript from the browser. |
| Is copying text from browser enabled | Enables copying texts in the browser. |
| Is downloading files enabled | Enables downloading files from the browser. |
| Is Kiosk limited to one web app | Sets whether the device can access single or multiple web views. |
| Is form auto-fill enabled | Enables autofill for forms in the browser. |
| Is content access enabled | Enables content URL access within WebView. Content URL access allows WebView to load content from a content provider installed in the system. |
| Is file access enabled | Sets whether JavaScript running in the context of a file scheme URL should be allowed to access content from other file scheme URLs. |
| Is allowed universal access from file URLs | Sets whether JavaScript running in the context of a file scheme URL should be allowed to access content from any origin. |
| Is application cache enabled | Enables web view's application cache. |
| Application cache file path | Sets the path to the Application Caches files. In order for the Application Caches API to be enabled, this method must be called with a path to which the application can write. |
| Application cache mode | Overrides the way the cache is used. The way the cache is used is based on the navigation type. For a normal page load, the cache is checked and content is re-validated as needed. When navigating back, content is not re-validated, instead the content is just retrieved from the cache. This method allows the client to override this behavior by specifying one of LOAD_DEFAULT, LOAD_CACHE_ELSE_NETWORK, LOAD_NO_CACHE or LOAD_CACHE_ONLY. |
| Should load images | Sets whether the browser should load image resources (through network and cached). Note that this method controls loading of all images, including those embedded using the data URI scheme. |
| Block image loads via network | Sets whether the browser should not load image resources from the network (resources accessed via http and https URI schemes). |
| Block all resource loads from network | title="Sets whether the browser should not load any resources from the network." |
| Support zooming | Sets whether the browser should support zooming using its on-screen zoom controls and gestures. |
| Show on-screen zoom controllers | Sets whether the browser should support zooming using its on-screen zoom controls and gestures. |
| Text zoom percentage | Sets whether the browser should support zooming using its on-screen zoom controls and gestures. |
| Default font size | Sets whether the browser should support zooming using its on-screen zoom controls and gestures. |
| Default text encoding name | Sets the default text encoding name to use when decoding html pages (Should be a valid text encoding). |
| Is database storage API enabled | Sets whether the database storage API is enabled. |
| Is DOM storage API enabled | Sets whether the DOM storage API is enabled. |
| Is Geolocation enabled | Sets whether Geolocation API is enabled. |
| Can JavaScript open windows | Sets whether JavaScript can open windows automatically or not. This applies to the JavaScript function window.open(). |
| Does media playback require user consent | Sets whether the browser requires a user gesture to play media. If false, the browser can play media without user consent. |
| Is safe browsing enabled | Sets whether safe browsing is enabled. Safe browsing allows browser to protect against malware and phishing attacks by verifying the links. |
| Use wide view port | Sets whether the browser should enable support for the viewport HTML meta tag or use a wide viewport. When the value of the setting is false, the layout width is always set to the width of the browser control in device-independent (CSS) pixels. When the value is true and the page contains the viewport meta tag, the value of the width specified in the tag is used. If the page does not contain the tag or does not provide a width, then a wide viewport will be used. |
| Browser user agent string | Sets the WebView's user-agent string. (Should be a valid user agent string). |
| Allow list URLs | Only the URLs listed here will be allowed to be accessed by the browser. Set comma seperated URLs and only http(s) URLs are allowed. |
| Match domains only in allow list | If this feature is enforced only the URLs that matches the above allow list will be allowed to be accessed. if not any domain in the list will be allowed to be accessed. |
| Allow subdomain redirects | This is used to grant permission to subdomains of the allow-listed domains. |
Mixed content mode
Configures the browser's behavior when a secure origin attempts to load a resource from an insecure origin.
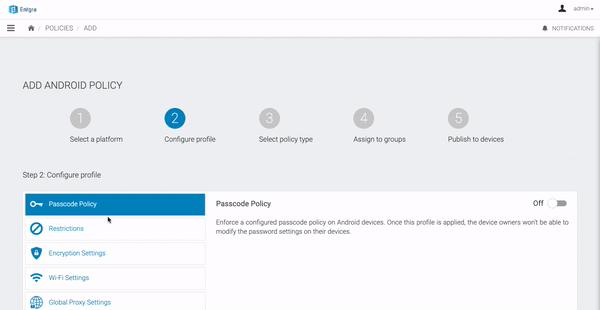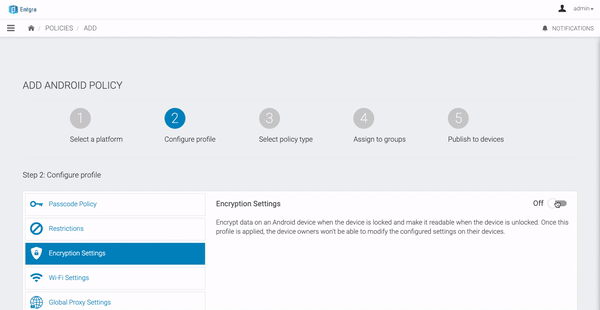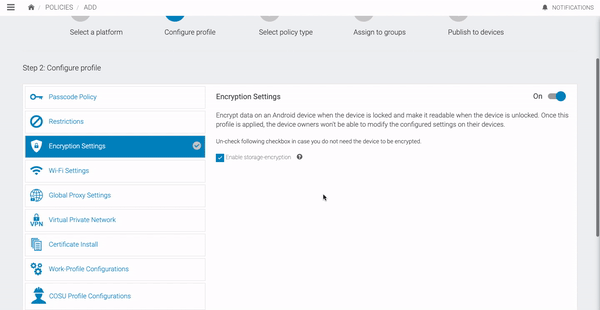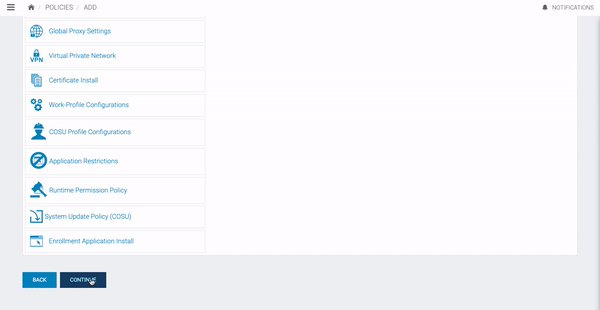
Encryption Settings
This configuration can be used to encrypt data on an Android device, when the device is locked and make it readable when the passcode is entered. Once this configuration profile is installed on a device, corresponding users will not be able to modify these settings on their devices.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Enable storage encryption | Encryption is the process of encoding all user data on an Android device using symmetric encryption keys. Having this checked would enable Storage-encryption in the device. |
Refer to Publish a Policy for instructions on how to publish a new policy in an Android device.
Virtual Private Network
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| VPN Settings | VPNs allow devices that are not physically on a network to securely access the network. Configure the OpenVPN settings on Android devices. In order to enable this, the device needs to have the OpenVPN for Android application installed. |
| OpenVPN Server Config | |
| Always On VPN Settings | Android can start a VPN service when the device boots and keep it running while the device is on. This feature is called always-on VPN and is available in Android 7.0 (API Level 24) or higher. Configure an always-on VPN connection through a specific VPN client application. |
| VPN Client Application Package Name | Package name of the VPN client application to be configured. |
Note: The configurations above are valid only when the agent is the work-profile owner or the device owner.
Access Point Name
This configurations can be used to configure APN (Access Point Name) on an Android device. This policy will support with the Android 9.0 onwards. This will not work with the below versions. And also Agent must be the device owner to activate this policy.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Name | Access point name. |
| Entry Name | String:The name to set for the APN This value may be null. Eg:Entgra |
| Proxy Address | String: the proxy address to set for the APN This value may be null.Eg: [192.168.8.1] |
| Proxy Port | int: the proxy port to set for the APN Eg:[ Target port 0-65535 ] |
| Username | String: the APN username to set for the APN This value may be null. |
| Password | String: the APN password to set for the APN This value may be null. |
| Server | String: the server set for the APN This value may be null. |
| MMSC | Uri: the MMSC Uri to set for the APN This value may be null. Eg:[ 192.168.8.1 ] |
| MMS Proxy Address | String: the MMS proxy address to set for the APN This value may be null.Eg:[ 192.168.8.1 ] |
| MMS Proxy Port | int: the MMS proxy port to set for the APN.Eg:[ Target port 0-65535 ] |
| MCC | int: the Mobile Country Code to set for the APN. Eg:413 |
| MNC | int: the Mobile Network Code to set for the APN. Eg:02 |
| Authentication Type | int: the authentication type to set for the APN Value. |
| APN Type | The APN type. |
| APN Protocol | APN protocol to be followed. |
| APN Roaming Protocol | APN protocol set for roaming. |
| Bearer | APN bearer. |
| APN Enable/Disable | Feature to enable and disable APN. |
| Mobile Virtual Network Operator Type | Virtual network operator for APN. |
| NONE | int: default Authentication Type for the APN. Constant Value: 0 (0x00000000) |
| PAP | int: Password Authentication Protocol for the APN. Constant Value: 1 (0x00000001) |
| CHAP | int: Authentication type for PAP or CHAP for the APN. Constant Value: 3 (0x00000003) |
| PAP_OR_CHAP | int: Challenge Handshake Authentication Protocol for the APN. Constant Value: 2 (0x00000002) |
| APN Type | int: Apn types are usage categories for an APN entry. One APN entry may support multiple APN types. |
| DEFAULT | int: APN type for default data traffic. Constant Value: 17 (0x00000011) |
| CBS | int: Carrier Branded Services for the APN. Constant Value: 128 (0x00000080) |
| DUN | int: Dial Up Networking bridge for the APN. Constant Value: 8 (0x00000008) |
| IMS | int: IP Multimedia Subsystem for the APN. Constant Value:64 (0x00000040) |
| MMS | int: Multimedia Messaging Service for the APN. Constant Value: 2 (0x00000002) |
| SUPL | int: APN type for SUPL assisted GPS. Constant Value: 4 (0x00000004) |
| IA | int: APN type for IA Initial Attach APN. Constant Value: 256 (0x00000100) |
| HIPRI | int: APN type for HiPri traffic. Constant Value: 16 (0x00000010) |
| FOTA | int: APN type for accessing the carrier's FOTA portal, used for over the air updates. Constant Value: 32 (0x00000020) |
| EMERGENCY | int: used for access to carrier services in an emergency call situation. Constant Value: 512 (0x00000200) |
| APN Protocol | int: Sets the protocol to use to connect to this APN |
| IPV4V6 | int: Virtual PDP type introduced to handle dual IP stack UE capability. Constant Value: 2 (0x00000002) |
| IP | int: Internet protocol. Constant Value: 0 (0x00000000) |
| IPV6 | int: Internet protocol, version 6. Constant Value: 1 (0x00000001) |
| PPP | int: Point to point protocol. Constant Value: 3 (0x00000003) |
| APN Roaming Protocol | int: Sets the protocol to use to connect to this APN when the device is roaming |
| IPV4V6 | int: Virtual PDP type introduced to handle dual IP stack UE capability. Constant Value: 2 (0x00000002) |
| IP | int: Internet protocol. Constant Value: 0 (0x00000000) |
| IPV6 | int: Internet protocol, version 6. Constant Value: 1 (0x00000001) |
| PPP | int: Point to point protocol. Constant Value: 3 (0x00000003) |
| APN Bearer | int: Sets Radio Technology (Network Type) info for this APN. |
| UNSPECIFIED | int: APN type for default data traffic. |
| LTE | int: Long Term Evolution is a standard in the communication of Mobile Phones used for data transfer. |
| HSPAP | int: Dial Up Networking bridge for the APN. Constant Value: 8 (0x00000008) |
| HSPA | int:High Speed Packet Access |
| HSUPA | int: High Speed Uplink Packet Access |
| HSDPA | int: High Speed Download/Upload Packet Access |
| UMTS | int: Universal Mobile Telecommunications System |
| EDGE | int: Enhanced Data for GSM Evolution |
| GPRS | int: General Packet Radio Service. Constant Value: 32 (0x00000020) |
| eHRPD | int: Evolved High-Rate Packet Data |
| EVDO_0 | int: Initial design of Evolution Data Optimized |
| EVDO_A | int: Several additions to the EVDO_0 |
| EVDO_B | int: Multi-carrier evolution of the EVDO_A specification |
| 1xRTT | int: Single carrier (1x) radio transmission technology |
| GSM | int: Global System for Mobile Communications |
| IWLAN | int: Industrial Wireless Local Area Network |
| APN Enable/Disable | boolean: the current status to set for this APN. |
| Mobile Virtual Network Operator Type | int: Sets the Mobile Virtual Network Operator match type for this APN. |
| SPN | int: MVNO type for service provider name. Constant Value: 0 (0x00000000) |
| GID | int: MVNO type for group identifier level 1. Constant Value: 2 (0x00000002) |
| ICCID | int: MVNO type for Integrated Circuit Card ID. Constant Value: 3 (0x00000003) |
| IMSI | int:MVNO type for International Mobile Subscriber Identity. Constant Value: 1 (0x00000001) |
WiFi Settings
These configurations can be used to configure WiFi access on an Android device. Once this configuration profile is installed on a device, corresponding users will not be able to modify these settings on their devices.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Service Set Identifier (SSID) | The network's SSID. Can either be a UTF-8 string or a string of hex digits, which are not enclosed in quotes (e.g., My Network, 01a243f405). |
| Security | Security type of the wireless network to be configured. 802.1x EAP works with Android 4.3 and above devices only. |
| WEP | WEP (Wired Equivalent Privacy) is a security algorithm for IEEE 802.11 wireless networks. |
| WPA/WPA 2 PSK | WiFi Protected Access (WPA), WiFi Protected Access II (WPA2) are the security protocols and security certification programs developed by the WiFi Alliance to secure wireless computer networks. |
| 802.1x EAP | |
| EAP Method | EAP is an authentication framework for providing the transport and usage of material and parameters generated by EAP methods . - PEAP : PEAP (Protected Extensible Authentication Protocol) is a version of EAP, the authentication protocol used in wireless networks and Point-to-Point connections. - TLS : EAP uses TLS public key certificate authentication mechanism within EAP to provide mutual authentication of client to server and server to client. - TTLS : The Tunneled TLS EAP method (EAP-TTLS) is very similar to EAP-PEAP in the way that it works and the features that it provides. The difference is that instead of encapsulating EAP messages within TLS, the TLS payload of EAP-TTLS messages consists of a sequence of attributes. - PWD : EAP-PWD is highly secure (the password is never transmitted, even in encrypted form), and does not require PKI certificates, and also requires only 3 authentication round-trips. - SIM : - AKA* : The AKA is defined in RFC 5448, and is used for non-3GPP access to a 3GPP core network. For example, via EVDO, WiFi, or WiMax. |
| Phase 2 Authentication | PAP : Password Authentication Protocol (PAP) is a password-based authentication protocol used by Point to Point Protocol (PPP) to validate users. - MCHAP : - MCHAPV2 : - GTC : Generic Token Card (GTC) carries a text challenge from the authentication server, and a reply generated by a security token. |
| Identity | Identity of the wireless network to be configured. |
| Anonymous Identity | Identity of the wireless network to be configured. |
| CA Certificate | CA Certificate for the wireless network. |
| Password | Password for the wireless network. |
| Enable force connect to WiFi | If this checkbox is ticked, the user will only be able to connect to the authorised WiFi networks with the SSIDs given above |
Refer to Publish Policy for instructions on how to publish a new policy in an Android device.
Wi-Fi Restrictions
This policy controls the Wi-Fi networks your device can connect to. Depending on the configuration, it will either prevent connections to networks on a specified denylist or allow connections only to networks on an allowlist.
Note
This policy is only supported on devices running Android 13.0 or higher.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Select policy type | 1. Allow list: When an allowlist is used, the device will only connect to networks that are included in the specified SSID list. All other networks will be disregarded. 2. Block list: When a denylist is used, the device will avoid connecting to any network that is included in the specified SSID list. All other networks remain available for connection. |
| WiFi SSID list | A comma-separated list of SSIDs that the device uses to determine network connection eligibility based on the selected SSID policy type. |
Certificate Install Settings
These configurations can be used to install certificate on an Android device.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Certificate name | The file name of the enclosed certificate. |
| Certificate file | The base64 representation of the payload with a line length of 52. |
| Certificate type | Certificate should be a DER-encoded X.509 SSL certificate in format of .crt or .cer |
Device Profile Policy
The configurations below can be applied to the devices the agent running on Android Enterprise.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Profile Name | Name of the Enterprise profile created by UEM Server Agent. |
| Enable System Apps | System applications that need to be enabled in the Enterprise profile. Should be exact package names seperated by commas. Ex: com.google.android.apps .maps, com.google.android.calculator. |
| Hide System Apps | System applications that need to be hidden in the Enterprise profile. Should be exact package names seperated by commas. Ex: com.google.android.apps .maps, com.google.android.calculator. |
| Unhide System Apps | System applications that need to be unhidden in the Enterprise profile. Should be exact package names seperated by commas. Ex: com.google.android.apps .maps, com.google.android.calculator. |
| Enable Google Play Store Apps | The applications that needs to be downloaded and installed from Google play store to the Enterprise profile. Should be exact package names seperated by commas. Ex: com.google.android.apps .maps, com.google.android.calculator. |
Runtime Permission Policy (Dedicated Device / Work Profile)
This configuration can be used to set a runtime permission policy to an Android Device.
Already granted or denied permissions are not affected by this policy. Permissions can be granted or revoked only for applications built with a Target SDK Version of Android Marshmallow or later.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Set default runtime permission | When an app requests a runtime permission, this enforces whether the user needs to prompted or the permission (PROMPT USER) either automatically granted (AUTO GRANT) or denied (AUTO DENY). |
| Set default runtime permission |
Set app-specific runtime permissions
Refer to_Add New Policy_ for instructions on how to add a new policy to an Android device.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Application | Eg: [ Android Pay ] |
| Package Name | Eg: [ com.google.android.pay ] |
| Permission Name | Eg: [ android.permission.NFC ] ] |
| Permission Name | * PROMPT USER, * AUTO GRANT, * AUTO DENY |
System Update Policy (Dedicated Devices)
Refer to_Add New Policy_ for instructions on how to add a new policy to an Android device.
This configuration can be used to set a passcode policy to an Android Device. Once this configuration profile is installed on a device, corresponding users will not be able to modify these settings on their devices.
| Data Keys | Descriptions |
|---|---|
| System Update | Type of the System Update to be set by the Device Owner: Automatic, Postpone, Window. |
| Start Time | Window start time for system update. (Only valid when Windows option is selected.) |
| End Time | Window end time for system update. (Only valid when Windows option is selected.) |
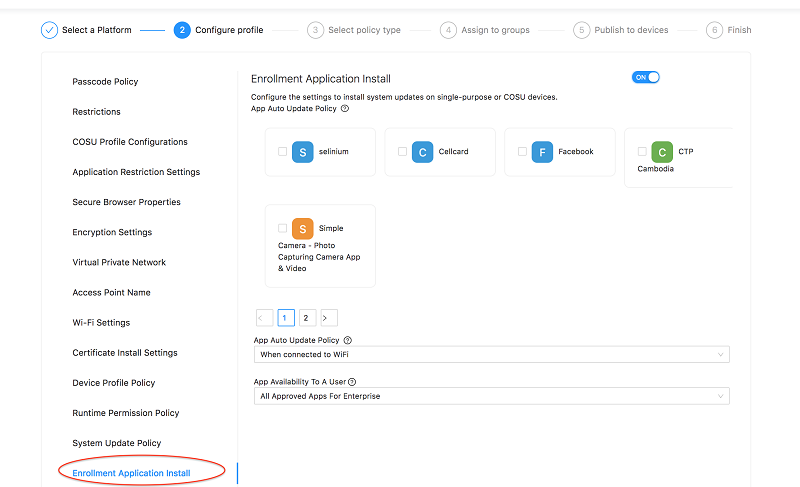
Enrollment Application Install
Enforce applications to be installed during Android device enrollment.
App Auto Update Policy
- When connected to WiFi
- Auto Update any time
- Ask user to Update
- Disable Auto Update
App availability to a user
- All Approved Apps for Enterprise
- All Apps from Playstores
- Only allow-listed Apps
Defining Permissible Apps Devices
When installing an app, it can be installed to the device groups, roles or users in the EMM server. At the same time, there are different properties such as whether to install the application while the device is plugged in to charging, whether to auto install app if the user tries to remove, etc. These properties need to be defined per user/group/role for better management. To achieve this, the process of defining the properties has been added to a policy.
-
Create new policy or edit an existing policy and go to Enrollment Application Install Policy.
-
Select the checkbox next to any app that you wish to make available to the assignees of this policy (devices in group/role/user).
-
Select the Add configurations checkbox and fill the form.
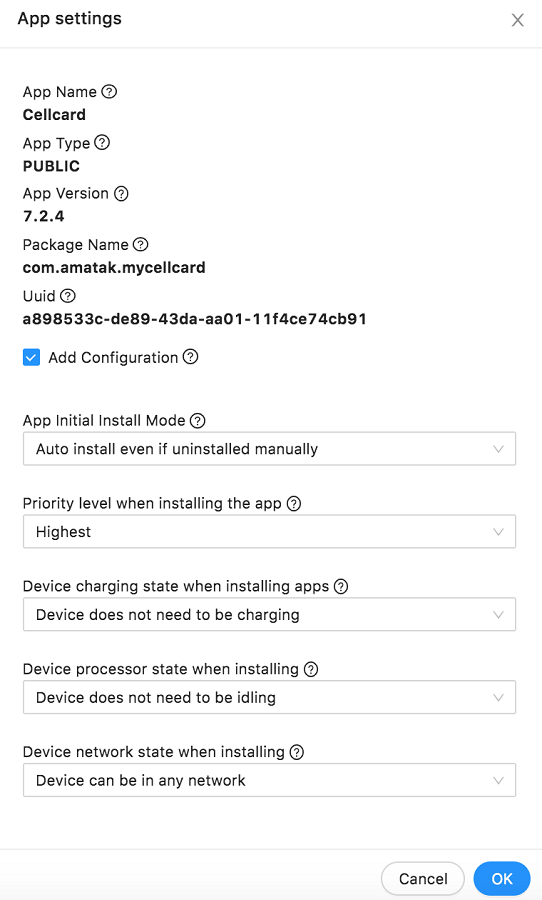
Per App Configuration Form Explanation
Per App Configuration Form Explanation
Input Field Dropdown Option Details App Initial Install Mode Auto install once only when enrolling Do not install automatically Auto install even if uninstalled manually Priority level when installing the app Highest to Lowest When there are multiple apps defined in the policy to be installed, the priority defined here will be used by playstore to determine which app to install first. Highest priority means the first to install. Device charging state when installing apps Device must be charging The app will not be installed until the device is connected to a charger Device does not need to be charging App will be installed regardless of the charging conditions of the device. However, please note on low power conditions, the device may behave based on the vendors preferences. Device processor state when installing Device does not need to be idling Install the application without considering the status of the device’s active state. i.e device does not need to be in the idle mode to start installation. Device must be idling Device network state when installing Device can be in any network App will be installed even if the device is on mobile data or even the network is marked metered. Device must be in an unmetered network Only install apps if the device is connected to WiFi Global Configurations for All Apps
Global Configurations for All Apps
There are 2 fields at the bottom of the Enrollment App Install policy which applies to all Android Enterprise enrolled devices that are configured via this policy. Given below is a description of those fields:
Input Field Dropdown Option Details App Auto Update Policy When connected to WiFi Any updates to applications in the device can begin only on WiFi Auto Update Anytime Any updates to applications in the device can begin at anytime Ask User To Update Any updates to applications in the device will only begin when the user agrees to update Disable Auto Update Disable updates to applications. Users need to go to the playstore and manually update applications. App Availability to a User All Approved Apps For Enterprise Any app that has been imported to the EMM server via the Import apps from Google playstore step is available for the user of the device to install manually. All Apps From Play store Users are free to instal any application from the playstore. Only Allow listed Apps User can only install apps that are specifically allowed by filling the Per app configuration form above and applied via a policy. -
Click OK save and apply the policy to required devices.
Display Message Configuration
This policy can be used to show the messages on the devices.To display the Lock screen message the device should have the device owner but the device owner does not need to display the long support message and the short support message.
Data Keys of Policy and Descriptions
| Data Keys | Description |
|---|---|
| Lock Screen Message | Lock screen message works only for the device owner. Once this message is applied, the device will display the device lock screen and the user cannot change it from the setting. |
| Setting App Support Message | Once this message is applied to devices, the message will be displayed to the user in the device administrator's settings screen. |
| Disabled Setting Support Message | Once this message is applied to devices the message will be displayed to the user in settings screens where functionality has been disabled by the admin.The message maximum length is 200 characters. |
App Usage Configuration
This policy allow to define restrictions of the network usage and the data usage limits of individual applications on your Android devices.
Prerequisites
Please ensure that the iots Firewall service is enabled under Android Firewall Configuration before enrolling the device.
Note
These restrictions will be applicable when the agent is the device owner, and for devices of Android version 9.0 (Pie) or higher.
Per App Network Usage Configuration
This policy allows for defining restrictions on network usage and data usage limits for individual apps. It notes that this policy is applicable only for COPE devices, and Entgra Firewall must be installed for the restrictions to be enforced.
Data Keys of Policy and Descriptions
| Data Keys | Description |
|---|---|
| Package Name | Package name of the application for which you want to set the data usage limit. |
| Allowed Data | Amount of data allocated to the specified application. |
| Unit | Unit of measurement for the allocated data amount, which can be either MB (megabytes) or GB (gigabytes). |
| Period | Specifies the duration during which the data usage limit is applicable. |
| Network | Specifies the type of network for which the data usage limit is enforced, which can be mobile data, WiFi, or both. |
| Enable Notifications | If enabled, notifications will be sent when the allocated data amount is exceeded. |
| Hide Applications | If enabled, the application will be automatically hidden from the device when the allocated data amount is exceeded. |
| Billing Date | Specifies the billing date in case a custom billing date is used. It must be a date in a month, for example, if the billing date is the 20th of every month, you should add "20". |
Block Apps from using Metered Connection
This policy enables the restriction of specific applications from accessing the internet when the device is connected to a network with metered or limited data usage.
Data Keys of Policy and Descriptions
| Data Keys | Description |
|---|---|
| Application Name | Name of the application that you want to block from using a metered connection. |
| Package Name | Package name of the relevant application. |
| Enable Notifications | If enabled, notifications will be sent when the specified app is blocked from using a metered connection. |
| Hide Applications | If enabled, the application will be automatically hidden from the device when it's blocked from using a metered connection. |
Screen Usage Configuration
This policy enables administrators to configure settings to manage the application's screen time. These settings include setting usage limits, defining allowable usage periods, and implementing restrictions to ensure the optimal use of the application.
Data Keys of Policy and Descriptions
| Data Keys | Description |
|---|---|
| Package Name | Package name of the relevant application. |
| Allowed Time | Amount of time allocated to use the specific application. |
| Unit | Unit of measurement for the allocated time, which can be either Minutes or Hours. |
| Period | Specifies the duration during which the screen usage restriction is applicable. |
| Enable Notifications | If enabled, sends notifications when the specified app is blocked after the allocated time constraints. |
Global Proxy Settings
This configuration can be used to set a network-independent global HTTP proxy on an Android device. Once the configuration profile is installed on a device, all the network traffic will be routed through the proxy server.
Note:
- This profile requires the agent application to be the device owner.
- The proxy is only a recommendation. Certain apps may ignore the proxy settings.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Proxy Configuration Type | The type of configuration. |
| Proxy Host | Host name/IP address of the proxy server. Eg:[ 192.168.8.1 ] |
| Proxy Port | Target port for the proxy server. Eg:[ Target port 0-65535 ] |
| Proxy Exclusion List | Add hostnames to this separated by commas to prevent them from routing through the proxy server. The hostname entries can be wildcards such as .example.com Eg:[ localhost, .example .com ] |
| Auto | |
| Proxy PAC File URL | URL for the proxy auto config PAC script Eg: [ http://exampleproxy.com/proxy.pac ] |
User Peripherals
Configure these settings to manage the applications in the show message.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Bluetooth Peripherals | The lists of apps the user allows or disallows will be in the allow list and/or the block list. Only the apps set by the user will be allowed. |
Enterprise Factory Reset Protection
Using Enterprise Factory Reset Protection, organizations can specify which Google Accounts can provision a device that has been factory reset. Consumer factory reset protection is designed to deter device theft.
Before allowing anyone to provision the device after unauthorized factory reset, the setup wizard requires the user to authenticate against any Google Accounts that were previously on the personal profile of the device.
This policy works only for Android 5.1 (Lolipop) or later versions and for devices provisioned as Device Owner.
Data Keys of Policy and Descriptions
Add Emails and Account IDs (Steps to obtain the Account ID)
To apply this policy to the device, email addresses and its account IDs should be given. Once the policy is applied on the device and after a hard reset, the device can be accessed only after providing any of the email address which was given in the policy.
How to get the get account ID to be used in the Policy?
- Sign in with the Gmail address
- Go to the Google GET People API https://developers.google.com/people/api/rest/v1/people/get
- Provide people/me for the resourceName
- Provide metadata for the personFields
- Click Execute
- Allow authorization access for the API
- Use the account ID returned in the response
Speed Limit Policy
When activated, this policy ensures that related corrective policies are applied if and when the set speed limit is exceeded on moving devices.
Using this policy, an administrator can define a speed limit on the device, which if exceeded, will result in subsequent corrective policies, such as disabling certain specific apps on the device, being applied.
Data Keys of Policy and Descriptions
| Data Key | Description |
|---|---|
| Set speed limit | If and when the set speed limit is exceeded on moving devices, you can set other corrective policies to be applied, such as disabling some apps on the device. |
Device Theme Policy
The device theme policy defines the device wallpaper settings and volume settings. It also sets the settings for locking screen wallpaper, system wallpaper and defines the system, media, alarm and calls volume levels. Note that alarm and call volume controllers may not work on some device models due to limitations of the Device vendor.
Data Keys of Policy and Descriptions
| Data Keys | Descriptions |
|---|---|
| Lock screen wallpaper URL | Give the URL of the image that you wish to configure as the wallpaper of the device lock screen. The image URL should be ending with .png, .jpg or .jpeg. |
| System wallpaper URL | Give the URL of the image that you wish to configure as the system wallpaper of the device. The image URL should be ending with .png, .jpg or .jpeg. |
| Music volume | This defines the media volume level of the device. Set the volume of audio streams for music. |
| System volume | This defines the notifications volume, ringing volume and DMFT volume. |
| Alarm volume | You can define the alarm volume of the device. This may not work on some device modules due to limitations from the device vendor. |
| Voice call volume | Able to define the volume of voice calls from here. This also may not work on some device modules due to limitations from the device vendor. |
Refer to Publish a Policy for instructions on how to publish a new policy on an Android device.
iOS & MacOS Policies
Passcode Policy
Refer to Add policy for instructions on how to add a policy to an iOS device.
The Passcode policy ensures better security by setting a passcode for the device which needs to be entered to unlock the device. The following configuration can be used to set up this policy in an iOS device. Once this configuration profile is installed on a device, corresponding users will not be able to modify these settings on their devices.
Data Keys of Policy and its Descriptions
Force Passcode
Determines whether the user is forced to set a PIN. Simply setting this value (and not others) forces the user to enter a passcode, without imposing a length or quality
Allow Simple Value
Determines whether a simple passcode is allowed. A simple passcode is defined as containing repeated characters, or increasing/decreasing characters (such as 123 or CBA). Setting this value to false is synonymous to setting minComplexChars to ”1”.
Allow Alphanumeric Value
Specifies whether the user must also enter alphabetic characters (”abcd”) along with numbers, or if numbers only are sufficient.
Minimum passcode length
Specifies the minimum overall length of the passcode.
Passcode history
When the user changes the passcode, it has to be unique within the last N entries in the history. Minimum value is 1, maximum value is 50. ( Should be in between 1-to-50 passcodes or none )
Auto Lock Time in minutes
Specifies the maximum number of minutes for which the device can be idle (without being unlocked by the user) before it gets locked by the system. Once this limit is reached, the device is locked and the passcode must be entered. The user can edit this setting, but the value cannot exceed the maxInactivity value.
Grace period in minutes for device lock
The maximum grace period, in minutes, to unlock without entering a passcode. Default is 0, that is no grace period, which requires entering a passcode immediately.
Maximum number of failed attempts
Allowed range [2...11]. Specifies the number of allowed failed attempts to enter the passcode at the deviceʼs lock screen. After six failed attempts, there is a time delay imposed before a passcode can be entered again. The delay increases with each attempt.Once this number is exceeded,on iOS the device is wiped.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Restrictions Policy
These configurations can be used to restrict apps, device features and media content available on an iOS device. Once this configuration profile is installed on a device, corresponding users will not be able to modify these settings on their devices.
Refer to Add policy for instructions on how to add a policy to an iOS device.
Data Keys of Policy and its Descriptions
Allow Siri
When false, disables Siri. Defaults to true.
Allow use of camera
Having this checked would enable Usage of phone camera in the device
Allow iCloud documents and data
[This key is deprecated on unsupervised devices.]
Having this checked would enable syncing iCloud documents and data in the device. This is deprecated on unsupervised devices Available in iOS 5.0 and later and in macOS 10.11and later.
Allow iCloud keychain
When false, disables iCloud keychain synchronization. Default is true. Available in iOS 7.0 and later and macOS 10 .12 and later.
Allow fingerprint for unlock
If false, prevents Touch ID from unlocking a device. Available in iOS 7 and later and in macOS 10.12.4 and later.
Allow in-app purchase
Having this checked would allow in-app purchase in the device.
Allow screenshots
If set to false, users canʼt save a screenshot of the display and are prevented from capturing a screen recording; it also prevents the Classroom app from observing remote screens.
Enable AutoFill
When false, Safari auto-fill is disabled. Defaults to true.
Allow voice dialing while device is locked
When false, disables voice dialing if the device is locked with a passcode. Default is true.
Force encrypting all backups
Having this checked would force encrypting all backups.
Allow managed apps to store data in iCloud
If set to false, prevents managed applications from using iCloud sync.
Allow Activity Continuation
If set to false, Activity Continuation will be disabled. Defaults to true.
Allow backup of enterprise books
If set to false, Enterprise books will not be backed up. Defaults to true
Allow enterprise books data sync
If set to false, Enterprise books notes and highlights will not be synced. Defaults to true.
Allow cloud photo library
If set to false, disables iCloud Photo Library. Any photos not fully downloaded from iCloud Photo Library to the device will be removed from local storage.
Allow remote screen observation
If set to false, remote screen observation by the Classroom app is disabled. Defaults to true. This key should be nested beneath allowScreenShot as a sub-restriction. If allowScreenShot is set to false, it also Available in iOS 9.3 and macOS 10.14.4 and later.
Allow adding Game Center friends
[This key is deprecated on unsupervised devices.]
When false, prohibits adding friends to Game Center. This key is deprecated on unsupervised devices.
Allow Siri to query user-generated content from web
Supervised only. When false, prevents Siri from querying user-generated content from the web. Available in iOS 7 and later.
Allow video conferencing
[This key is deprecated on unsupervised devices.]
When false, disables video conferencing. This key is deprecated on unsupervised devices
Allow Safari
[This key is deprecated on unsupervised devices.]
When false, the Safari web browser application is disabled and its icon removed from the Home screen. This also prevents users from opening web clips. This key is deprecated on unsupervised devices.
Allow multiplayer gaming
[This key is deprecated on unsupervised devices.]
When false, prohibits multiplayer gaming. This key is deprecated on unsupervised devices.
Allow use of iTunes Store
When false, the iTunes Music Store is disabled and its icon is removed from the Home screen. Users cannot preview, purchase, or download content. This key is deprecated on unsupervised devices.
Following are DEP(Supervised) only
Force Delayed Software Updates
If set to true, delays user visibility of Software Updates. Defaults to false. On macOS, seed build updates will be allowed, without delay. Available in iOS 11.3 and macOS 10.13
Allow Erase All Content And Settings
If set to false, disables the “Erase All Content And Settings” option in the Reset UI.
Allow Spotlight Internet results
If set to false, Spotlight will not return Internet search results. Available in iOS and in macOS 10.11 and later.
Enforced Software Update Delay
This restriction allows the admin to set how many days a software update on the device will be delayed. With this restriction in place, the user will not see a software update until the specified number of days after the software update release date. The max is 90 days and the default value is 30. Available in iOS 11.3 and macOS 10.13.4
Force Classroom Automatically Join Classes
If set to true, automatically give permission to the teacherʼs requests without prompting the student. Defaults to false Available only in iOS 11.0 and macOS 10 .14.4 and later
Force Classroom Request Permission To Leave Classes
If set to true, a student enrolled in an unmanaged course via Classroom will request permission from the teacher when attempting to leave the course. Defaults to false. Available only in iOS 11.3 and macOS 10.14.4 and later.
Force Classroom Unprompted App And Device Lock
If set to true, allow the teacher to lock apps or the device without prompting the student. Defaults to false Available only in iOS 11.0 and macOS 10.14.4 and later.
Force Classroom Unprompted Screen Observation
If set to true, and ScreenObservationPermissionModificationAllowed is also true in the Education payload, a student enrolled in a managed course via the Classroom app will automatically give permission to that courseʼs teacherʼs requests to observe the studentʼs screen without prompting the student. Defaults to false. Available only in iOS 11.0 and macOS 10.14.4 and later.
Allow Password Auto Fill
If set to false, users will not be able to use the AutoFill Passwords feature on iOS and will not be prompted to use a saved password in Safari or in apps. If set to false, Automatic Strong Passwords will also be disabled and strong passwords will not be suggested to users. Defaults to true. Available only in iOS 12.0 and macOS 10 .14 and later.
Allow Password Proximity Requests
If set to false, a userʼs device will not request passwords from nearby devices. Defaults to true. Available only in iOS 12.0 and macOS 10.14
Allow Password Sharing
If set to false, users can not share their passwords with the Airdrop Passwords feature. Defaults to true. Available only in iOS 12.0 and macOS 10.14 and later.
Allow definition lookup
If set to false, disables definition lookup. Defaults to true. Available in iOS 8.1.3 and later and in macOS 10.11.2 and later
Allow music service
If set to false, Music service is disabled and Music app reverts to classic mode. Defaults to true. Available in iOS 9.3 and later and macOS 10.12 and later
Restrictions on iOS device
Allow Siri while device is locked
When false, the user is unable to use Siri when the device is locked. Defaults to true. This restriction is ignored if the device does not have a passcode set.
Allow removing apps
[This key is deprecated on unsupervised devices .]
When false, disables removal of apps from iOS device. This key is deprecated on unsupervised devices.
Allow iCloud backup
When false, disables backing up the device to iCloud.
Allow diagnostic submission
When false, this prevents the device from automatically submitting diagnostic reports to Apple. Defaults to true. Available only in iOS 6.0 and later.
Allow explicit content
[This key is deprecated on unsupervised devices .]
When false, explicit music or video content purchased from the iTunes Store is hidden. Explicit content is marked as such by content providers, such as record labels, when sold through the iTunes Store. This key is deprecated on unsupervised devices. Available in iOS and in tvOS 11.3 and later
Allow global background fetch when roaming
When false, disables global background fetch activity when an iOS phone is roaming.
Show Notifications Center in lock screen
If set to false, the Notifications history view on the lock screen is disabled and users canʼt view past notifications. Though, when the device is locked, the user will still be able to view notifications when they arrive. Available only in iOS 7.0 and later.
Show Today view in lock screen
If set to false, the Today view in Notification Center on the lock screen is disabled. Available only in iOS 7.0 and later.
Allow documents from managed sources in unmanaged destinations
If false, documents in managed apps and accounts only open in other managed apps and accounts. Default is true. Available only in iOS 7.0 and later
Allow documents from unmanaged sources in managed destinations
If set to false, documents in unmanaged apps and accounts will only open in other unmanaged apps and accounts. Default is true. Available only in iOS 7.0 and later.
Show Passbook notifications in lock screen
If set to false, Passbook notifications will not be shown on the lock screen.This will default to true. Available in iOS 6.0 and later.
Allow Photo Stream
When false, disables Photo Stream. Available in iOS 5.0 and later.
Force Fraud warning
When true, Safari fraud warning is enabled. Defaults to false Available in iOS 4.0 and later.
Enable Javascript
When false, Safari will not execute JavaScript. Defaults to true. Available in iOS 4.0 and later.
Enable Pop-ups
When false, Safari will not allow pop-up tabs. Defaults to true. Available in iOS 4.0 and later.
Accept cookies
Determines conditions under which the device will accept cookies. The user facing settings changed in iOS 11, though the possible values remain the same:
• 0: Prevent Cross-Site Tracking and Block All Cookies are enabled and the user canʼt disable either setting.
• 1 or 1.5: Prevent Cross-Site Tracking is enabled and the user canʼt disable it. Block All Cookies is not enabled, though the user can enable it.
• 2: Prevent Cross-Site Tracking is enabled and Block All Cookies is not enabled. The user can toggle either setting. (Default)
These are the allowed values and settings in iOS 10 and earlier:
• 0: Never
• 1: Allow from current website only
• 1.5: Allow from websites visited (Available in iOS 8.0 and later); enter ’ 1.5’
• 2: Always (Default)
In iOS 10 and earlier, users can always pick an option that is more restrictive than the payload policy, but not a less restrictive policy. For example, with a payload value of 1.5, a user could switch to Never, but not Always Allow.
Allow Shared Photo Stream
If set to false, Shared Photo Stream will be disabled.This will default to true. Available in iOS 6.0 and later.
Allow untrusted TLS prompt
When false, automatically rejects untrusted HTTPS certificates without prompting the user. Available in iOS 5.0 and later.
Require iTunes store password for all purchases
When true, forces user to enter their iTunes password for each transaction Available in iOS 5.0 and later.
Limit ad tracking
If true, limits ad tracking. Default is false Available only in iOS 7.0 and later
Force a pairing password for Airplay outgoing requests
If set to true, forces all devices receiving AirPlay requests from this device to use a pairing password. Default is false. Available only in iOS 7.1 and later.
Force air drop unmanaged
If set to true, causes AirDrop to be considered an unmanaged drop target. Defaults to false. Available in iOS 9.0 and later.
Force watch wrist detection
If set to true, a paired Apple Watch will be forced to use Wrist Detection. Defaults to false. Available in iOS 8.2 and later.
Allow over-the-air PKI updates
If false, over-the-air PKI updates are disabled. Setting this restriction to false does not disable CRL and OCSP checks. Default is true. Available only in iOS 7.0 and later.
Ratings region
This 2-letter key is used by profile tools to display the proper ratings for given region. It is not recognized or reported by the client. Possible values:
• au: Australia
• ca: Canada
• fr: France
• de: Germany
• ie: Ireland
• jp: Japan
• nz: New Zealand
• gb: United Kingdom
• us: United States
Available in iOS and tvOS 11.3 and later
Allow content ratings
(Having this checked would allow to set the maximum allowed ratings)
Allowed content ratings for movies
This value defines the maximum level of movie content that is allowed on the device. Possible values (with the US description of the rating level): • 1000: All • 500: NC-17 • 400: R • 300: PG-13 • 200: PG • 100: G • 0: None Available only in iOS and tvOS 11.3 and later
Allowed content ratings for TV shows
This value defines the maximum level of TV content that is allowed on the device. Possible values (with the US description of the rating level): • 1000: All • 600: TV-MA • 500: TV-14 • 400: TV-PG • 300: TV-G • 200: TV-Y7 • 100: TV-Y • 0: None Available only in iOS and tvOS 11.3 and later.
Allowed content ratings for apps
This value defines the maximum level of app content that is allowed on the device. Possible values (with the US description of the rating level): • 1000: All • 600: 17+ • 300: 12+ • 200: 9+ • 100: 4+ • 0: None Available only in iOS 5 and tvOS 11.3 and later.
Allow enterprise app trust
If set to false removes the Trust Enterprise Developer button in Settings->General->Profiles & Endpoint Management, preventing apps from being provisioned by universal provisioning profiles. This restriction applies to free developer accounts but it does not apply to enterprise app developers who are trusted because their apps were pushed via MDM, nor does it revoke previously granted trust. Defaults to true. Available in iOS 9.0 and later.
Show Control Center in lock screen
If false, prevents Control Center from appearing on the Lock screen. Available in iOS 7 and later.
Read unmanaged apps from managed contact accounts.
If set to true, unmanaged apps can read from managed contacts accounts. Defaults to false. if allowOpenFromManagedToUnmanaged is true, this restriction has no effect. A payload that sets this to true must be installed via MDM. Available only in iOS 12.0 and later
Following are DEP(Supervised) only
Allow user prompted profile installation
If set to false, the user is prohibitedfrom installing configuration profiles and certificates interactively. This will default to true. Available in iOS 6.0 and later
Allow Chat
When false, disables the use of iMessage with supervised devices. If the device supports text messaging, the user can still send and receive text messages Available in iOS 6.0 and later.
Allow Cellular Plan Modification
If set to false, users canʼt change any settings related to their cellular plan. Defaults to true Available in iOS 11.0 and later.
Allow USB Restricted Mode
If set to false, device will always be able to connect to USB accessories while locked. Defaults to true. Available only in iOS 11.4.1 and later
Allow ESIM Modification
If set to false, the user may not remove or add a cellular plan to the eSIM on the device. Defaults to true Available only in iOS 12.1 and later.
Modify Personal Hotspot Modification
If set to false, the user may not modify the personal hotspot setting. Defaults to true. Available only in iOS 12.2 and later.
Automatically set Date and Time
If set to true, the Date & Time “Set Automatically” feature is turned on and canʼt be turned off by the user. Defaults to false.
Note: The deviceʼs time zone will only be updated when the device can determine its location (cellular connection or wifi with location services enabled).
Available only in iOS 12.0
Allow modifying account settings
If set to false, account modification is disabled. Available only in iOS 7.0 and later.
Allow modifying cellular data app settings
- f set to false, changes to cellular data usage for apps are disabled.
- Available only in iOS 7.0 and later.
Allow Siri to query user-generated content from web
When false, prevents Siri from querying user-generated content from the web. Available in iOS 7 and later.
Enable iBookStore
If set to false, Apple Books will be disabled. This will default to true. Available in iOS 6.0 and later.
Enable iBookStore Erotica
If set to false, the user will not be able to download media from Apple Books that has been tagged as erotica. This will default to true. Available in iOS and in tvOS 11.3 and later.
Allow Find My Friends modification
If set to false, changes to Find My Friends are disabled. Available only in iOS 7.0 and later.
Allow use of Game Center
When false, Game Center is disabled and its icon is removed from the Home screen. Default is true. Available only in iOS 6.0 and later.
Allow Host Pairing
If set to false, host pairing is disabled with the exception of the supervision host. If no supervision host certificate has been configured, all pairing is disabled. Host pairing lets the administrator control which devices an iOS 7 device can pair with. Available only in iOS 7.0 and later.
Allow Enable Restrictions option
If set to false, disables the ”Enable Restrictions” option in the Restrictions UI in Settings. Default is true. On iOS 12 or later, if set to false disables the ”Enable ScreenTime” option in the ScreenTime UI in Settings and disables ScreenTime if already enabled. Available in iOS 8.0 and later.
Allow News
If set to false, disables News. Defaults to true Available in iOS 9 .0 and later.
Allow use of Podcasts
If set to false, disables podcasts. Defaults to true. Available in iOS 8.0 and later.
Allow keyboard auto-correction
If set to false, disables keyboard auto-correction. Defaults to true . Available in iOS 8.1.3 and later
Allow keyboard spell-check
If set to false, disables keyboard spell-check. Defaults to true. Available in iOS 8.1.3 and later.
Allow UI app installation
When false, the App Store is disabled and its icon is removed from the Home screen. However, users may continue to use Host apps (iTunes, Configurator) to install or update their apps. Defaults to true. In iOS 10 and later, MDM commands can override this restriction. Available in iOS 9 .0 and later
Allow keyboard shortcuts
If set to false, keyboard shortcuts cannot be used. Defaults to true. Available in iOS 9.0 and later.
Allow passcode modification
If set to false, prevents the device passcode from being added, changed, or removed. Defaults to true. This restriction is ignored by shared iPads . Available in iOS 9.0 and later.
Allow device name modification
If set to false, prevents device name from being changed. Defaults to true. Available in iOS 9.0
Allow wallpaper modification
If set to false, prevents wallpaper from being changed. Defaults to true . Available in iOS 9.0 and later.
Allow automatic app downloads
If set to false, prevents automatic downloading of apps purchased on other devices. Does not affect updates to existing apps. Defaults to true. Available in iOS 9.0 and later.
Allow radio service
If set to false, Apple Music Radio is disabled. Defaults to true. Available in iOS 9.3 and later.
Deny-listed app bundle IDs(comma separated)
If present, prevents bundle IDs listed in the array from being shown or launchable. Include the value com.apple.webapp to deny-list all webclips. Available in iOS 9.3 and later.
Allow-listed app bundle IDs(comma separated)
If present, allows only bundle IDs listed in the array from being shown or launchable. Include the value com.apple.webapp to allow-list all webclips. Available in iOS 9.3 and later
Allow diagnostic bluetooth modification
If set to false, prevents modification of Bluetooth settings. Defaults to true. Available in iOS 10.0 and later.
Allow dictation
If set to false, disallows dictation input. Defaults to true. Available only in iOS 10.3 and later
Force WiFi allow-listing (Warning, wrong configuration could break communication)
If set to true, the device can join Wi-Fi networks only if they were set up through a configuration profile. Defaults to false. Available only in iOS 10.3 and later.
Allow air print
If set to false, disallow AirPrint. Defaults to true. Available in iOS 11.0 and later.
Allow air print credentials storage
If set to false, disallows keychain storage of username and password for Airprint. Defaults to true. Available in iOS 11.0 and later.
Force air print trusted TLS requirement
If set to true, requires trusted certificates for TLS printing communication. Defaults to false. Available in iOS 11.0 and later.
Allow air print iBeacon discovery
If set to false, disables iBeacon discovery of AirPrint printers. This prevents spurious AirPrint Bluetooth beacons from phishing for network traffic. Defaults to true. Available in iOS 11.0 and later.
Allow system app removal
If set to false, disables the removal of system apps from the device. Defaults to true. Available only in iOS 11.0 and later.
Allow VPN creation
If set to false, disallow the creation of VPN configurations. Defaults to true. Available only in iOS 11.0 and later.
Allow proximity setup to new device
If set to false, disables the prompt to setup new devices that are nearby . Defaults to true. Available only in iOS 11.0 and later.
Allow installing apps
When false, the App Store is disabled and its icon is removed from the Home screen. Users are unable to install or update their applications. This key is deprecated on unsupervised devices. MDM commands can override this restriction. Available only in iOS 10 and later
Allow AirDrop
If set to false, AirDrop is disabled. Available only in iOS 7.0 and later.
Permitted Applications in Autonomous Single App Mode
If present, allows apps identified by the bundle IDs listed in the array to autonomously enter Single App Mode. Available only in iOS 7.0 and later. Application Bundle ID:
Allow diagnostic submission modification
When false, this prevents the device from automatically submitting diagnostic reports to Apple. Defaults to true. Available only in iOS 6.0 and later.
Allow diagnostic submission modification
If set to false, the diagnostic submission and app analytics settings in the Diagnostics & Usage pane in Settings cannot be modified. Defaults to true . Available in iOS 9.3.2 and later
Allow notifications modification
If set to false, notification settings cannot be modified. Defaults to true. Available in iOS 9.3 and later.
Allow predictive keyboard
If set to false, disables predictive keyboards. Defaults to true. Available in iOS 8.1.3 and later.
Force Authentication Before Auto Fill
If set to true, the user will have to authenticate before passwords or credit card information can be autofilled in Safari and Apps. If this restriction is not enforced, the user can toggle this feature in settings. Only supported on devices with FaceID or TouchID. Defaults to true. Available only in iOS 11.0 and later
Restrictions on mac OS device
Allow macOS iCloud Bookmark sync
When false, disallows macOS iCloud Bookmark sync. Available in macOS 10 .12 and later.
Allow macOS Mail iCloud services
When false, disallows macOS Mail iCloud services. Available in macOS 10 .12 and later
Allow macOS Mail iCloud Calender services
When false, disallows macOS iCloud Calendar services. Available in macOS 10.12 and later.
Allow macOS Mail iCloud Reminder services
When false, disallows iCloud Reminder services. Available in macOS 10 .12 and later.
Allow macOS Mail iCloud Address Book services
(Available in macOS 10.12 and later.)
Allow macOS Mail iCloud Notes services
When false, disallows macOS iCloud Notes services. Available in macOS 10.12 and later.
Allow content caching
When false, this disallows content caching. Defaults to true. Available only in macOS 10.13 and later.
Allow iTunes application file sharing
When false, iTunes application file sharing services are disabled. Available in macOS 10.13 and later.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Global Proxy Settings
Refer to Add policy for instructions on how to add a policy to an iOS device.
Configure a global HTTP proxy to direct all HTTP traffic from Supervised iOS 7 and higher devices through a designated proxy server. Once this configuration profile is installed on a device, all the network traffic will be routed through the proxy server
This policy is only applicable for the devices enrolled in supervised mode.
Data Keys of Policy and its Descriptions
Proxy Configuration Type
If you choose manual proxy type, you need the proxy server address including its port and optionally a username and password into the proxy server. If you choose auto proxy type, you can enter a proxy autoconfiguration (PAC) URL.
Proxy Host
The proxy serverʼs network address.(Host name/IP address of the proxy server.)
Proxy Port
The proxy serverʼs port
Username
The username used to authenticate to the proxy server.
Password
The password used to authenticate to the proxy server
Allow Captive Login
When checked, Allows the device to bypass the proxy server to display the login page for captive networks.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
AirPlay Settings
Refer to Add policy for instructions on how to add a policy to an iOS device.
This configuration can be used to define settings for connecting to AirPlay destinations. Once this configuration profile is installed on an iOS device, corresponding users will not be able to modify these settings on their devices.
Data Keys of Policy and its Descriptions
AirPlay Credentials
(If present, sets passwords for known AirPlay destinations.)
Device Name
The name of the AirPlay destination (used on iOS).
Password
The password for the AirPlay destination.
AirPlay Destinations Allow-list
(Supervised only. If present, only AirPlay destinations present in this list are available to the device.)
Destination
The Device ID of the AirPlay destination, in the format xx:xx:xx:xx:xx:xx. This field is not case sensitive.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Manage Domains
Refer to Add policy for instructions on how to add a policy to an iOS device.
This payload defines web domains that are under an enterprise’s management.
Data Keys of Policy and its Descriptions
Unmarked Email Domains
(Any email address that does not have a suffix that matches one of the unmarked email domains specified by the key EmailDomains will be considered out-of-domain and will be highlighted as such in the Mail app.)
Email Domains
An array of strings. An email address lacking a suffix that matches any of these strings will be considered out-of-domain.
Managed Safari Web Domains
(Supervised only. If present, only AirPlay destinations present in this list are available to the device.)
Managed Safari Web Domains
An array of URL strings. URLs matching the patterns listed here will be considered managed.
Refer to Publish policy for instructions on how to publish an applied policy in an iOS device.
LDAP Settings
This configuration can be used to define settings for connecting to LDAP servers. Once this configuration profile is installed on an iOS device, corresponding users will not be able to modify these settings on their devices.
Refer to Add policy for instructions on how to add a policy to an iOS device.
| Data Keys of Policy | Descriptions |
|---|---|
| Account Description | Display name of the account |
| Account Hostname | LDAP Host name or IP address |
| Use Secure Socket Layer(SSL) | Having this checked, would enable Secure Socket Layer communication. |
| Account Username | User name for this LDAP account |
| Account Password | Password for this LDAP account |
| Search Settings | Search settings for this LDAP account. Can have many of these for one account. Should have at least one for the account to be useful. |
| Description | Description of this search setting |
| Search Base | Conceptually, the path to the node where a search should start. For example: ou=people,o=example corp |
| Scope | Defines what recursion to use in the search. Can be one of the following 3 values: LDAPSearchSettingScopeBase: Just the immediate node pointed to by SearchBase. LDAPSearchSettingScopeOneLevel: The node plus its immediate children. LDAPSearchSettingScopeSubtree: The node plus all children, regardless of depth. |
Refer to Publish policy for instructions on how to publish an applied policy in an iOS device.
ActiveSync Configurations
Refer to Add policy for instructions on how to add a policy to an iOS device.
This configuration can be used to provision ActiveSync Configurations for iOS devices.
Data Keys of Policy and its Descriptions
Email Address
Specifies the full email address for the account. If not present in the payload, the device prompts for this string during profile installation.
Exchange Server Hostname
Specifies the Exchange server host name (or IP address).
Use Secure Socket Layer(SSL)
Specifies whether the Exchange server uses SSL for authentication.
Account Username
This string specifies the user name for this Exchange account. Required in non-interactive installations (like MDM on iOS).
Account Password
The password of the account. Use only with encrypted profiles.
Use OAuth
Specifies whether the connection should use OAuth for authentication. If enabled, a password should not be specified. This defaults to false. Availability: Available only in iOS 12.0 and later.
Available in iOS only
ActiveSync Certificate file
For accounts that allow authentication via certificate, a .p12 identity certificate in NSData blob format
Certificate Name
Specifies the name or description of the certificate
Certificate Password
The password necessary for the p12 identity certificate. Used with mandatory encryption of profiles.
Prevent Move
If set to true, messages may not be moved out of this email account into another account. Also prevents forwarding or replying from a different account than the message was originated from. Availability: Available in iOS 5.0 and later.
Prevent App Sheet
If set to true, this account will not be available for sending mail in any app other than the Apple Mail app. Availability: Available in iOS 5.0 and later
Payload Certificate UUID
UUID of the certificate payload to use for the identity credential. If this field is present, the Certificate field is not used. Availability: Available in iOS 5.0 and later
SMIME Enabled
If true, this account supports S/MIME. As of iOS 10.0, this key is ignored. Availability: Available only in iOS 5.0 through 9.3.3.
SMIME Signing Enabled
If set to true, S/MIME signing is enabled for this account. Availability: Available only in iOS 10.3 and later
SMIME Signing Certificate UUID
The PayloadUUID of the identity certificate used to sign messages sent from this account. Availability: Available only in iOS 5.0 and later.
SMIME Encryption Enabled
If set to true, S/MIME encryption is on by default for this account. Availability: Available only in iOS 10.3 and later. As of iOS 12.0, this key is deprecated. It is recommended to use SMIMEEncryptByDefault instead.
SMIME Encryption Certificate UUID
The PayloadUUID of the identity certificate used to decrypt messages sent to this account. The public certificate is attached to outgoing mail to allow encrypted mail to be sent to this user. When the user sends encrypted mail, the public certificate is used to encrypt the copy of the mail in their Sent mailbox. Availability: Available only in iOS 5.0 and later.
SMIME Enable PerMessage Switch
The password necessary for the p12 identity certificate. Used with mandatory encryption of profiles.
SMIME Signing User Overrideable
T If set to true, the user can toggle S/MIME signing on or off in Settings. Availability: Available only in iOS 12.0 and later.
SMIME Signing Certificate UUID UserOverrideable
If set to true, the user can select the signing identity. Availability: Available only in iOS 12.0 and later.
SMIME Encrypt By Default
If set to true, S/MIME encryption is enabled by default. If SMIMEEnableEncryptionPerMessageSwitch is false, this default cannot be changed by the user. Availability: Available only in iOS 12.0 and later.
SMIME Encrypt By Default User Overrideable
If set to true, the user can toggle the encryption by default setting. Availability: Available only in iOS 12.0 and later.
SMIME Encryption Certificate UUID User Overrideable
If set to true, the user can select the S/MIME encryption identity and encryption is enabled. Availability: Available only in iOS 12.0 and later.
SMIME Enable Encryption Per-Message Switch
If set to true, displays the per-message encryption switch in the Mail Compose UI. Availability: Available only in iOS 12.0 and later
Allow Mail drop
If true, this account is allowed to use Mail Drop. The default is false. Availability: Available only in macOS 10.12 and later.
Disable Mail Recents Syncing
If true, this account is excluded from address Recents syncing. Availability: Available only in iOS 6.0 and later.
Mail Number Of PastDays To Sync
The number of days since synchronization.
Bundle ID of Default Application Handling Audio Calls
The communication service handler rules for this account. The CommunicationServiceRules dictionary currently contains only a DefaultServiceHandlers key; its value is a dictionary which contains an AudioCall key whose value is a string containing the bundle identifier for the default application that handles audio calls made to contacts from this account.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Calendar
Refer to Add policy for instructions on how to add a policy to an iOS device.
This configuration can be used to define settings for connecting to CalDAV servers. Once this configuration profile is installed on an iOS device, corresponding users will not be able to modify these settings on their devices.
Data Keys of Policy and its Descriptions
Account Description
Display name of the account. Eg: Company CalDAV Account
Account Hostname
CalDAV Host name or IP address
Use Secure Socket Layer(SSL)
Having this checked, would enable Secure Socket Layer communication with CalDAV server.
Account Port
CalDAV account Host Port number
Principal URL
Principal URL for the CalDAV account
Account Username
CalDAV account user name
Account Password
CalDAV account password
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Calendar Subscriptions
Refer to Add policy for instructions on how to add a policy to an iOS device.
This configuration can be used to define settings for calendar subscriptions. Once this configuration profile is installed on an iOS device, corresponding users will not be able to modify these settings on their devices.
Data Keys of Policy and its Descriptions
Description
Description of the account.
Account Hostname URL
The server address.
Use Secure Socket Layer (SSL)
Having this checked, would enable Secure Socket Layer communication.
Username
The userʼs login name.
Password
The userʼs password.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Cellular Network Settings
Refer to Add policy for instructions on how to add a policy to an iOS device.
These configurations can be used to specify Cellular Network Settings on an iOS device. Cellular settings cannot be installed if an APN setting is already installed and upon successful installation, corresponding users will not be able to modify these settings on their devices.
(This feature is supported only on iOS 7.0 and later.)
Data Keys of Policy and its Descriptions
Cellular Configuration Name
The Access Point Name.
Authentication Type
Must contain either CHAP or PAP. Defaults to PAP.
Username
A user name used for authentication.
Password
A password used for authentication.
APN Configurations
APN
The Access Point Name.
Auth.Type
Must contain either CHAP or PAP. Defaults to PAP.
Username
A user name used for authentication.
Password
A password used for authentication.
Proxy
The proxy serverʼs network address.
Port
The proxy serverʼs port.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Network Usage Rules
Refer to Add policy for instructions on how to add a policy to an iOS device.
Network Usage Rules allow enterprises to specify how managed apps use networks, such as cellular data networks.
These rules only apply to managed apps.
Data Keys of Policy and its Descriptions
Allow cellular data when roaming
(Common to all rule configuration types)
If set to false, matching managed apps will not be allowed to use cellular data when roaming.
Allow Cellular Data
(Common to all rule configuration types)
If set to false, matching managed apps will not be allowed to use cellular data at any time.
Applly to specified managed apps
(Set network usage rules to specific applications)
Application Identifier Match
A list of managed app identifiers, as strings, that must follow the associated rules. If this key is missing, the rules will apply to all managed apps on the device Each string in the Application Identifier Match may either be an exact app identifier match, [e.g . com.mycompany.myapp] or it may specify a prefix match for the Bundle ID by using the * wildcard character. The wildcard character, if used, must appear after a period character (.), and may only appear once, at the end of the string [e.g. com .mycompany ..]*
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Certificate Install
This configurations can be used to install certificate on an iOS device.
Please note that * sign represents required fields of data.
Refer to Add policy for instructions on how to add a policy to an iOS device.
Data Keys of Policy and its Descriptions
Certificate name
The file name of the enclosed certificate.
Certificate file
The base64 representation of the payload with a line length of 52.
Certificate Password
For PKCS#12 certificates, contains the password to the identity.
Certificate type
The Payload Type of a certificate payload must be one of the following:
| Payload type | Container format | Certificate type |
|---|---|---|
| com.apple.security.root | PKCS#1(.cer) | Alias for com.apple.security.pkcs1. |
| com.apple.security.pkcs1 | PKCS#1(.cer) | DER-encoded certificate without private key. May contain root certificates. |
| com.apple.security.pem | PKCS#1(.cer) | PEM-encoded certificate without private key. May contain root certificates |
| com.apple.security.pkcs12 | PKCS#12(.p12) | Password-protected identity certificate. Only one certificate may be included. |
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Font Install
Refer to Add policy for instructions on how to add a policy to an iOS device.
This configurations can be used to add an additional font to an iOS device.
Please note that * sign represents required fields of data.
Data Keys of Policy and its Descriptions
Font name
The user-visible name for the font. This field is replaced by the actual name of the font after installation.
Font file
The contents of the font file.
Each payload must contain exactly one font file in TrueType (.ttf) or OpenType ( .otf) format. Collection formats (.ttc or .otc) are not supported.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
App Lock (Kiosk)
Refer to Add policy for instructions on how to add a policy to an iOS device.
This configuration can be used to enforce the iOS device to a single application i.e to make a device act as a Kiosk.
This configuration will be applied only on Supervised devices having iOS 7.0 and later.
Data Keys of Policy and its Descriptions
Identifier
The bundle identifier of the application.
Options
Disable touch
If true, the touch screen is disabled.
Disable Device Rotation
If true, device rotation sensing is disabled
Disable volume buttons
If true, the volume buttons are disabled.
Disable ringer switch
If true, the ringer switch is disabled.
Disable sleep wake button
If true, the sleep/wake button is disabled.
Disable auto lock
If true, the device will not automatically go to sleep after an idle period.
Enable voice over
If true, VoiceOver is turned on.
Enable zoom
If true, Zoom is turned on.
Enable invert colors
If true, Invert Colors is turned on.
Enable assistive touch
If true, AssistiveTouch is turned on.
Enable speak selection
If true, Speak Selection is turned on.
Enable mono audio
If true, Mono Audio is turned on.
User Enabled Options
Voice over
If true, allow VoiceOver adjustment.
Zoom
If true, allow Zoom adjustment.
Invert colors
If true, allow Invert Colors adjustment.
Assisstive touch
If true, allow AssistiveTouch adjustment.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
App Store Restriction
Refer to Add policy for instructions on how to add a policy to an iOS device.
These configurations can be used to restrict the app store on a mac-os device. Once this configuration profile is installed on a device, corresponding users will not be able to access the app store of the device.
This configuration will be applied only on macOS devices.
Data Keys of Policy and its Descriptions
Restrict App Installation.
Restrict app installations to admin users.
Available on macOS 10.9 and later.
Restrict app installations to software updates only.
Restrict app installations to software updates only.
Available on macOS 10.10 and later
Disable App Adoption by users.
Disable App Adoption by users.
Available on macOS 10.10 and later
Disable software update notifications
Disable software update notifications.
Available on macOS 10.10 and later.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Login Window Preference
Refer to Add policy for instructions on how to add a policy to an iOS device.
This payload creates managed preferences on all versions of macOS for system and device profiles. Multiple Login window payloads may be installed together. This configuration will be applied only on macOS devices.
This configuration will be applied only on macOS devices.
Data Keys of Policy and its Descriptions
Restrict App Installation.
Restrict app installations to admin users.
Available on macOS 10.9 and later.
Restrict app installations to software updates only.
Restrict app installations to software updates only.
Available on macOS 10.10 and later
Disable App Adoption by users.
Disable App Adoption by users.
Available on macOS 10.10 and later
Disable software update notifications
Disable software update notifications.
Available on macOS 10.10 and later.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Firewall Policy
Refer to Add policy for instructions on how to add a policy to an iOS device.
A Firewall policy manages the Application Firewall settings that are accessible in the Security Preferences pane. This policy is available in macOS 10.12 and later.
This configuration will be applied only on macOS devices.
The ”Automatically allow downloaded signed software” and ”Automatically allow built-in software” options are not supported, but both will be forced ON when this payload is present.
Data Keys of Policy and its Descriptions
Enable Firewall
Whether the firewall should be enabled or not.
Block all incoming connections
Corresponds to the “Block all incoming connections” option. When it is enabled incoming new connections are blocked
Enable stealth mode.
Corresponds to “Enable stealth mode.” When stealth mode is turned on, your Mac does not respond to “ping” requests and does not answer connection attempts from a closed TCP or UDP network.
Applications
The list of applications. Each dictionary contains these keys:
Bundle ID
Identifies the application. It should be a string value.
Allowed
Specifies whether or not incoming connections are allowed
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Wi-Fi Settings Policy
Refer to Add policy for instructions on how to add a policy to an iOS device.
| Data Keys of Policy | Description |
|---|---|
| Service Set Identifier (SSID) | SSID of the Wi-Fi network to be used. In iOS 7.0 and later, this is optional if a DomainName value is provided. |
| Domain Name | This field can be provided instead of SSID_STR. Available in iOS 7.0 and later.( For Wi-Fi Hotspot 2.0 negotiation ) |
| Hidden Network | Besides SSID, the device uses information such as broadcast type and encryption type to differentiate a network. By default (false), it is assumed that all configured networks are open or broadcast. To specify a hidden network, must be true. |
| Hot Spot | If true, the network is treated as a hotspot. Available in iOS 7.0 and later. |
| Enable Service Provider Roaming | If true, allows connection to roaming service providers. Defaults to false. Available in iOS 7.0 and later. |
| Auto Join | If true, the network is auto-joined. If false, the user has to tap the network name to join it. Available in iOS 5.0 and later. |
| Displayed Operator Name | The operator name to display when connected to this network. Used only with Wi-Fi Hotspot 2.0 access points. Available in iOS 7.0 and later. |
| Proxy Setup | Valid values are None, Manual, and Auto. Available in iOS 5.0 and later. If the ProxyType field is set to Manual, the following fields must also be provided |
| Encryption Security Type | Refer to the notes below for details on this. |
| Roaming Consortium OIs | Roaming Consortium Organization Identifiers used for Wi-Fi Hotspot 2.0negotiation. Requires 6 or 10 hexadecimal characters. Available in iOS 7.0 and later. |
| Network Access Identifier ( NAI ) Realm Names | List of Network Access Identifier Real names used for Wi-Fi Hotspot 2.0 negotiation. Available in iOS 7.0 and later. |
| Mobile Country Code ( MCC ) / Mobile Network Code ( MNC ) Configuration | List of Mobile Country Code (MCC)/Mobile Network Code (MNC) pairs used for Wi-Fi Hotspot 2.0 negotiation. Each string must contain exactly six digits. Available in iOS 7.0 and later. |
Email Settings
Refer to Add policy for instructions on how to add a policy to an iOS device.
These configurations can be used to define settings for connecting to your POP or IMAP email accounts. Once this configuration profile is installed on an iOS device, corresponding users will not be able to modify these settings on their devices.
| Data Keys of Policy | Description |
|---|---|
| Account Description | A user-visible description of the email account, shown in the Mail and Settings applications. |
| Account Type | Defines the protocol to be used for that account. |
| Path Prefix | The path prefix for the IMAP mail server |
| Email Account Name | The full user name for the account. This is the user name in sent messages, etc. |
| Email Address | Designates the full email address for the account. If not present in the payload, the device prompts for this string during profile installation. |
| Prevent move | If true, messages may not be moved out of this email account into another account. Also prevents forwarding or replying from a different account than the message was originated from. Availability: Available only in iOS 5.0 and later. |
| Prevent App Sheet | If true, this account is not available for sending mail in any app other than the Apple Mail app. Availability: Available only in iOS 5.0 and later |
| Enable S/MIME | If true, this account supports S/MIME. As of iOS 10.0, this key is ignored. Availability: Available only in iOS 5.0 through iOS 9.3.3. |
| S/MIME Signing Certificate UUID | The Payload UUID of the identity certificate used to sign messages sent from this account. Availability: Available only in iOS 5.0 and later |
| Enable Per-message Signing and Encryption Switch | If set to true, display the per-message encryption switch in the Mail Compose UI. Availability: Available only in iOS 12.0 and later |
| Allow Recent Address Syncing | If true, this account is excluded from address Recents syncing. This defaults to false Availability: Available only in iOS 6.0 and later. |
| Incoming | Mail Settings |
|---|---|
| Mail Server Hostname | Designates the incoming mail server host name (or IP address). |
| Use Secure Socket Layer(SSL) | Designates whether the incoming mail server uses SSL for authentication. |
| Mail Server Port | Designates the incoming mail server port number. If no port number is specified, the default port for a given protocol is used. |
| Authentication Type | Designates the authentication scheme for incoming mail. Allowed values are EmailAuthPassword, EmailAuthCRAMMD5, EmailAuthNTLM, EmailAuthHTTPMD5, and EmailAuthNone. |
| Username | Designates the user name for the email account, usually the same as the email address up to the @ character. If not present in the payload, and the account is set up to require authentication for incoming email, the device will prompt for this string during profile installation. |
| Password | Password for the Incoming Mail Server. Use only with encrypted profiles. |
| Outgoing | Mail Settings |
|---|---|
| Mail Server Hostname | Designates the outgoing mail server host name (or IP address). |
| Use Server Socket Layer(SSL) | Default false. Designates whether the outgoing mail server uses SSL for authentication. |
| Mail Server Port | Designates the outgoing mail server port number. If no port number is specified, ports 25, 587 and 465 are used, in this order. |
| Authentication Type | Designates the authentication scheme for outgoing mail. Allowed values are EmailAuthPassword, EmailAuthCRAMMD5, EmailAuthNTLM, EmailAuthHTTPMD5, and EmailAuthNone. |
| Username | Designates the user name for the email account, usually the same as the email address up to the @ character. If not present in the payload, and the account is set up to require authentication for outgoing email, the device prompts for this string during profile installation |
| Password | Password for the Outgoing Mail Server. Use only with encrypted profiles. |
Data Keys of Policy and its Descriptions
Account Description
A user-visible description of the email account, shown in the Mail and Settings applications.
Account Type
Defines the protocol to be used for that account.
Path Prefix
The path prefix for the IMAP mail server
Email Account Name
The full user name for the account. This is the user name in sent messages, etc.
Email Address
Designates the full email address for the account. If not present in the payload, the device prompts for this string during profile installation.
Prevent move
If true, messages may not be moved out of this email account into another account. Also prevents forwarding or replying from a different account than the message was originated from.
Availability: Available only in iOS 5.0 and later.
Prevent App Sheet
If true, this account is not available for sending mail in any app other than the Apple Mail app. Availability: Available only in iOS 5.0 and later
Enable S/MIME
If true, this account supports S/MIME. As of iOS 10.0, this key is ignored. Availability: Available only in iOS 5.0 through iOS 9.3.3.
S/MIME Signing Certificate UUID
The PayloadUUID of the identity certificate used to sign messages sent from this account. Availability: Available only in iOS 5.0 and later
Enable Per-message Signing and Encryption Switch
If set to true, display the per-message encryption switch in the Mail Compose UI. Availability: Available only in iOS 12.0 and later
Allow Recent Address Syncing
If true, this account is excluded from address Recents syncing. This defaults to false. Availability: Available only in iOS 6.0 and later.
Incomming Mail Settings
Mail Server Hostname
Designates the incoming mail server host name (or IP address).
Use Secure Socket Layer(SSL)
Designates whether the incoming mail server uses SSL for authentication.
Mail Server Port
Designates the incoming mail server port number. If no port number is specified, the default port for a given protocol is used.
Authentication Type
Designates the authentication scheme for incoming mail. Allowed values are EmailAuthPassword, EmailAuthCRAMMD5, EmailAuthNTLM, EmailAuthHTTPMD5, and EmailAuthNone.
Username
Designates the user name for the email account, usually the same as the email address up to the @ character. If not present in the payload, and the account is set up to require authentication for incoming email, the device will prompt for this string during profile installation.
Password
Password for the Incoming Mail Server. Use only with encrypted profiles.
Outgoing Mail Settings
Mail Server Hostname
Designates the outgoing mail server host name (or IP address).
Use Server Socket Layer(SSL)
Default false. Designates whether the outgoing mail server uses SSL for authentication.
Mail Server Port
Designates the outgoing mail server port number. If no port number is specified, ports 25, 587 and 465 are used, in this order.
Authentication Type
Designates the authentication scheme for outgoing mail. Allowed values are EmailAuthPassword, EmailAuthCRAMMD5, EmailAuthNTLM, EmailAuthHTTPMD5, and EmailAuthNone.
Username
Designates the user name for the email account, usually the same as the email address up to the @ character. If not present in the payload, and the account is set up to require authentication for outgoing email, the device prompts for this string during profile installation
Password
Password for the Outgoing Mail Server. Use only with encrypted profiles.
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
VPN (Virtual Private Network) Settings
Refer to Add policy for instructions on how to add a policy to an iOS device.
This configurations can be used to configure VPN settings on an iOS device. Once this configuration profile is installed on a device, corresponding users will not be able to modify these settings on their devices.
Please note that * sign represents required fields of data.
Data Keys of Policy and its Descriptions
Connection Name
Description of the VPN connection displayed on the device.
Override Primary
Specifies whether to send all traffic through the VPN interface. If true, all network traffic is sent over VPN.
On-demand Enabled
Check if the VPN connection should be brought up on demand, else leave un-checked.
VPN Type
Determines the settings available in the payload for this type of VPN connection. It can have one of the following values: * L2TP
-
PPTP
-
IPSec (Cisco)
-
IKEv2 (see IKEv2 Dictionary Keys)
-
AlwaysOn (see AlwaysOn Dictionary Keys)
-
VPN (solution uses a VPN plugin or NetworkExtension, so the VPNSubType key is required (see below)).
NOTE Refer to Publish policy for instructions on how to publish an applied policy in an >iOS device.
Windows Policies
Entgra UEM offers comprehensive policy management capabilities for Windows devices, empowering administrators to enforce security, configuration, and compliance standards across their organization. Administrators can leverage two distinct types of policies:
General Policies
- General Policies encompass a broader range of settings beyond registry-based configurations, allowing administrators to define policies that cover device management, application management, security controls, and user experience enhancements.
- By offering a wider scope of policy options, General Policies enable administrators to address diverse management requirements and tailor configurations to specific use cases or user groups within their organization.
The following is a list of General Policies available in Entgra UEM:
- App Locker Policy
- Application Management Policy
- Assigned Access Settings
- Background Intelligent Transfer Service
- BitLocker Settings
- Bluetooth
- Defender
- Encryption Settings
- Firewall Settings
- Messaging
- Passcode Policy
- Restrictions
- Setting App Policy
- Update Settings
- Wi-Fi Settings
App Locker Policy
Using this Windows App Locker policy, it is possible to block apps that need to be restricted from the users.
| Data Key | Policy Description |
|---|---|
| Application ID | The ID of the application that is to be added to the policy. |
| Application Name | The name of the application that is to be added to the policy. |
| Type | The application type. |
| Description | A brief description about the application. Optionally, this can be left blank. |
| User or Group SID | |
| Publisher Name | Full name of the application. |
| Product Name | The product name is the first part of the PackageFullName followed by the version number. In the Windows Camera example, the ProductName is Microsoft.WindowsCamera. |
| Binary Name | Indicates the app name with the extension. |
| High Section | Defines the highest version number that should be trusted. |
| Low Section | Defines the lowest version number that should be trusted. |
| Enforcement Mode | |
| Action | Action is to whether allow the app or deny the app usage. |
Application Management Policy
This configuration can be used to set a application management policy to a Windows Device.
| Data Key | Policy Description |
|---|---|
| Allow All Trusted Apps | Specifies whether non Microsoft Store apps are allowed |
| Allow App Store Auto Update | Windows app store auto update default value is enabled |
| Allow Developer Unlock | Specifies whether developer unlock is allowed. |
| Allow Game DVR | Specifies whether DVR and broadcasting are allowed. |
| Allow Shared User App Data | With this policy, you can configure Windows 10 to share application data among multiple users on the system and with other instances of that app. |
| MSI Allow User Control Over Install | If you enable this policy setting, some of the security features of Windows Installer are bypassed. It permits installations to complete that otherwise would be halted due to a security violation. |
| MSI Always Install With Elevated Privileges | If you enable this policy setting, privileges are extended to all programs. These privileges are reserved for programs that have been assigned to the user (offered on the desktop), assigned to the computer (installed automatically), or made available in Add or Remove Programs in Control Panel. |
| Restrict App Data To System Volume | Specifies whether application data is restricted to the system drive. |
| Restrict App To System Volume | Specifies whether the installation of applications is restricted to the system drive. |
Assigned Access Settings
This policy is used to set the device to run in kiosk mode. Once this has been executed, the next user log-in that is associated with the kiosk mode puts the device into the kiosk mode running the application specified in the policy configuration.
It is important to keep in mind if there is a single user when the policy is being applied, there is no way to access the settings and manually sync and revoke the policy. The UEM server sends requests every minute and if there are any pending revoked policies it will sync at that time. Alternatively, the device could be manually synced using another user account and the changes will be applied. A computer restart is required for the policy enforcement and revokes to take effect.
| Data Key | Policy Description |
|---|---|
| Account name | The account name will be used to find the target user. The account name includes the domain name (the domain is optional if the user name is unique across the system) and the user name. |
| Application AUMID | The application AUMID is the identifier for Universal Apps (UWP) installed from the Windows Store. Steps to finding the AUMID can be found here. |
Background Intelligent Transfer Service (BITS)
Background Intelligent Transfer Service (BITS) transfers files in the background using idle network bandwidth. If this service is disabled, then any applications that depend on BITS, will be unable to automatically download programs and other information.
| Data Key | Policy Description |
|---|---|
| Bandwidth Throttling End Time | This policy specifies the bandwidth throttling end time that BITS uses for background transfers. |
| Bandwidth Throttling Start Time | This policy specifies the bandwidth throttling start time that BITS uses for background transfers. |
| Bandwidth Throttling Transfer Rate | This policy specifies the bandwidth throttling transfer rate in kilobits per second (Kbps) that BITS uses for background transfers. |
| Costed Network Behavior Background Priority | This policy setting defines the default behavior that the BITS uses for background transfers when the system is connected to a costed network (3G, etc.). |
| Costed Network Behavior Foreground Priority | This policy setting defines the default behavior that the foreground BITS uses for foreground transfers when the system is connected to a costed network (3G, etc.). |
| Job Inactivity Timeout | This policy setting specifies the number of days a pending BITS job can remain inactive before the job is considered abandoned. |
BitLocker Settings
This policy can be used to encrypt storage devices of a Windows using the BitLocker encryption tool. It can be used on devices which are containing TPM and not. This can be used to encrypt different drive types:
- System drives (Operating system drive)
- Fixed data drives (Non-operating system disk partitions of the device)
- Removable storage devices (Portable hard drives, USB flash drives)
The BitLocker decryption key can be generated and stored in the following ways:
-
Devices containing TPM
- Use only TPM and store the decryption key in TPM
- TPM + USB key
- TPM + PIN
- TPM + USB key + PIN
-
Devices not containing TPM
- Using a USB key
- Using a PIN
| Data Key | Policy Description |
|---|---|
| Require device encryption | Allowing the administrator to require encryption that needs to be turned on by using BitLocker\Device Encryption. |
| Require storage card encryption | |
| Removable devices require encryption | This setting is a direct mapping to the BitLocker Group Policy "Deny write access to removable drives not protected by BitLocker" |
| Enable non-TPM key | This is used to allow BitLocker without a compatible TPM. A password or a USB drive is required for start-up in this mode. |
| Enable TPM startup PIN and key | Used to configure the TPM startup PIN and TPM startup key. |
| Enable TPM startup | Used to configure the TPM startup. |
| System drives enhanced PIN | Allowing users to configure whether or not enhanced startup PINs are used with BitLocker. |
| Disable standard user to change system drive PIN | Disallow changing PIN of system drives by non-admin users. |
| TPM minimum startup PIN length | PIN length can be set to a minimum character count. |
| Allow certificate-based data recovery agent | Allow users to configure a certificate-based data recovery agent. |
| Enable recovery password | Prompt users to enter a recovery password. |
| Save Bitlocker recovery information to Archive Directory Domain Services | Save the recovery key to Active Directory. |
| Save recovery key to Archive Directory Domain Services | Disable encryption until the Recovery key is stored in an Active Directory server. |
Bluetooth
Windows bluetooth configuration policy allow to define setting of windows bluetooth app and its scanning parameters
| Data Key | Policy Description |
|---|---|
| Disable Bluetooth | Having this checked would disable bluetooth control in the device |
| Allow bluetooth advertisements | Allows or disallows Windows Bluetooth Advertisements functionality |
| Allow bluetooth discoverable mode | Allows or disallows Windows Bluetooth discoverable mode functionality |
| Allow bluetooth pairings with other devices | Allows or disallows Windows Bluetooth pairing functionality |
| Allow users on managed devices to use Swift Pair and other proximity based scenarios | Allows or disallows users on managed devices to use Swift Pair and other proximity based scenarios functionality |
Defender
Various Windows Defender actions can be configured throughout the enterprise using the Windows Defender Configuration Service Provider.
| Data Key | Policy Description |
|---|---|
| Allow archive scanning | Windows Defender will scan the contents of compressed (archive) files when a scan is scheduled or when the user starts the scanning process manually. |
| Allow behavior monitoring | This policy setting allows you to configure behavior monitoring. When you enable this setting behavior monitoring will be enabled. |
| Allow cloud protection | Standard real-time protection is improved by this cloud protection, also known as Microsoft Advanced Protection Service (MAPS) |
| Allow IOAV protection | This policy setting specifies whether Windows Defender IOAVP Protection is permitted or not. |
| Allow on access protection | Allowing or disallowing Windows Defender On Access Protection functionality. |
| Allow real-time monitoring | Specifies whether Windows Defender real-time monitoring is allowed or not. |
| Allow scanning network files | Specifies whether Windows Defender real-time monitoring is allowed or not. |
| Allow script scanning | Specifies whether the Windows Defender Script Scanning feature is allowed or not. |
| Allow user UI access | Gives or denies users access to the Windows Defender user interfaces. |
| CPU load for scan(%) | Represents the average CPU load factor for the Windows Defender scan (in percent). |
| Check for signatures before scan | You can choose whether a check for new virus and spyware definitions will take place before performing a scan using this policy setting. This parameter only affects manually started scans from the user interface; it has no impact on scheduled scans. |
| Cloud block level | The level of vigilance used by Microsoft Defender Antivirus while blocking and scanning suspicious files is determined by this policy parameter. |
| Cloud extended timeout | A suspect file can be blocked by Microsoft Defender Antivirus for up to 50 seconds using this capability, and it can also be checked for safety in the cloud. |
| Controlled folder access allowed applications | Incorporated in Windows 10, build 1709. This policy option enables the controlled folder access capability for user-specified applications. To give many folders, use the |
| Controlled folder access protected folders | The regulated folder access feature can now include user-specified folder locations thanks to this policy option. Use the |
| Days to retain cleaned malware | Duration for which the software keeps records of malware that has been detected and cleaned from the system |
| Disable catchup full scan | You can configure catch-up scans for scheduled rapid scans using this policy parameter. A scan that is started because a regularly planned scan wasn't performed is known as a catch-up scan. Because the computer was shut down at the appointed time, these planned scans are frequently missed. |
| Disable catchup quick scan | You can configure catch-up scans for scheduled rapid scans using this policy parameter. A scan that is started because a regularly planned scan wasn't performed is known as a catch-up scan. Because the computer was shut down at the appointed time, these planned scans are frequently missed. |
| Enable controlled folder access | Enable or disable controlled folder access for untrusted applications. You can choose to disable, audit, or enable attempts by untrusted apps. |
| Enable network protection | Users and apps will be prevented from connecting to risky sites if you enable this policy's Block mode option. Users and applications won't have their connections to risky sites barred if you enable this policy using the Audit option. In the Windows Defender Security Center, Block mode and Audit activities will still be visible. Users and apps won't be prevented from connecting to risky domains if you disable. |
| Excluded extensions | Enables a scanning administrator to provide a list of file types and extensions to ignore. There must be a ' |
| Excluded paths | Enables a scan's administrator to define a list of directory paths to skip. There must be a ' |
| Excluded processes | Allows an administrator to define a list of files that should be ignored while performing a scan on them. There must be a ' |
| PUA protection status | Establishes the threshold for detecting potentially harmful applications (PUAs). When potentially unwanted software is downloading or tries to install itself on your computer, Windows Defender notifies you. |
| Real-time scan direction | Determines which file sets should be watched. This option can be utilized to keep tabs on particular files even if AllowOnAccessProtection is not permitted. |
Scan Schedule
| Data Key | Policy Description |
|---|---|
| Scan type | Selects whether to perform a quick scan or full scan |
| Scan time | Selects the time of day that the Windows Defender quick scan should run. |
Signature Update configs and feedback from device
| Data Key | Policy Description |
|---|---|
| Security intelligence location | This policy setting allows you to define the security intelligence location for VDI-configured computers |
| Signature update fallback order | You can choose the sequence in which various definition update sources should be notified using this policy setting. This setting's value must be a pipe-separated list of all the definition update sources, listed sequentially. |
| Signature update file shares sources | You can configure UNC file sharing sources for downloading definition updates using this policy setting. The order in which sources are contacted will be followed. A pipe-separated string listing the definition update sources should be used as the value of this setting. |
| Submit samples consent | Checks for the user consent level in Windows Defender to send data. |
Default action for thereat
| Data Key | Policy Description |
|---|---|
| Severity levels | Allows an administrator to specify any valid threat severity levels and the corresponding default action ID to take. |
Encryption Settings
This configuration can be used to encrypt data on a Windows device when the device is locked and make it readable when the passcode is entered.
| Data Key | Policy Description |
|---|---|
| Enable store encryption | Encryption is the process of encoding all user data on a Windows device using symmetric encryption keys. Having this checked would enable Storage-encryption in the device. |
Firewall Settings
Firewall settings can be used to configure the Windows Defender Firewall global settings, per profile settings, and the desired set of custom rules to be enforced on the device
| Data Key | Policy Description |
|---|---|
| Stateful File Transfer Protocol | Allows the firewall to perform stateful File Transfer Protocol (FTP) filtering to allow secondary connections |
| Security Association Idle Time | This value configures the security association idle time, in seconds |
| Pre Shared Key Encoding | Specifies the preshared key (PSK) encoding that is used |
| IPSec Exemptions | IPSec exemptions allow specific traffic that may be needed by the system |
| Certificate Revocation List Verification | This value specifies how certificate revocation list (CRL) verification is enforced |
| Key Modules Ignore Unsupported Authentication Suites | When this option is on, keying modules MUST ignore only the authentication suites that they don’t support |
| Packet Queue | This value specifies how scaling for the software on the receive side is enabled for both the encrypted receive and clear text forward path for the IPsec tunnel gateway scenario |
Messaging
Configure Messaging settings on Windows devices
| Data Key | Policy Description |
|---|---|
| Allow Message sync | Allow or disallow Message sync |
Passcode Policy
This policy can be used to enforce a configured password on Windows devices.
| Data Key | Policy Description |
|---|---|
| Allow simple value | Allows a sequence of repeating, ascending and descending characters for the password |
| Require alphanumeric value | This indicates that the password must contain both letters and numbers |
| Minimum passcode length | Determines the least number of characters that can make up a password for a user account |
| Minimum number of complex characters | Determines how many complex characters or non-alphanumeric characters could be included in the applying passcode |
| Maximum passcode age in days | Determines the period of time (in days) that a password can be used before the system requires the user to change it. |
| Passcode history | Determines the number of unique new passwords that must be associated with a user account before an old password can be reused |
| Maximum number of failed attempts before device reset | This specifies how many times a user can enter the wrong password before all the data of the device gets wiped. |
Restrictions
Restrictions policies are those that can be applied on a device restricting or controlling the use of certain specific device features.
The following restriction policies are applicable on a Windows device.
| Data Key | Policy Description |
|---|---|
| Disable Camera | This restriction disables the camera on the device. |
| Disable Location | Selecting this undermines the location service for the device. |
| Disable Storage Card | When enables, the device is restricted from accessing the SD card slot. |
| Disable Device Reset | This is used for disabling the device resetting remotely. |
| Disable OneDrive sync | This will disable sync files with OneDrive. |
| Disable manual root certificate install | This restriction would disable manual root certificate installation in the device. |
| Disable Bluetooth | Disabling Bluetooth control in the device. |
| Disable cellular data | Disabling mobile data roaming on the device. Applicable only for mobile devices. |
| Disable data roaming | This restriction will disable the cellular data roaming on the device. Applicable only for mobile devices. |
| Disable connected devices | When enables, users are not allowed to connect with other devices. |
| Disable Disable connect with PC | Users are not allowed to connect with other devices after disabling this. |
| Disable connected devices | Disallowing connection with a PC of the device. |
| Disable NFC | This will disable Near Field Communications (NFC) and transfer data between devices using NFC technology. |
| Disable USB connection | This restriction will disable the USB drivers connection through USB ports. This only works for mobile devices. |
| Disable VPN configurations | By using this user can restrict the VPN configuration settings in the device. Applicable only for mobile devices. |
| Disable VPN roaming | This policy restriction will disable VPN roaming in the device. Applicable only for mobile devices. |
| Disable date time | This would disable date and time configurations in the device. |
| Disable non Microsoft accounts | This could be used to block users from switching to Microsoft accounts. |
| Disable private windows in the browser | Users will be restricted from using private browsing on the devices. |
| Disable indexing of removable drivers | This is used to search results containing files from removable devices. |
| Disable language settings | Users are not allowed to disable the language settings on the device. |
| Disable Disable region settings | Users are not allowed to disable the region settings on the device. |
| Disable Cortana | Once applied, Cortana gets disabled. |
Setting App Policy
Setting app controlling policy.
| Data Key | Policy Description |
|---|---|
| Allow auto play | Allows the user to change Auto Play settings. |
| Allows Data Sense | Allows the user to change Data Sense settings. (Supported bellow Windows 10, version 2004) |
| Allow date time | Allows the user to change date and time settings. |
| Allow editing device name | This policy disables edit device name option on Settings. |
| Allow changing device language | Allows the user to change the language settings. |
| Allow online help tips | Enables or disables the Settings app's ability to retrieve online help and tips. Settings won't contact Microsoft content services to retrieve advice and assistance content if they are disabled. |
| Allow power sleep | Allows the user to change power and sleep settings. |
| Allow region changes | Allows the user to change the region settings. |
| Allow sign-in options | Allows the user to change sign in options. |
| Allow VPN | Allows the user to change VPN settings. |
| Allow workplace | Allows user to change workplace settings. |
| Allow the user to change account settings | Allows user to change account settings. |
| Enables IT administrators to change the taskbar clock and calendar flyout's default setting to display additional calendars in addition to the locale's default calendar. | Configure additional taskbar calenders |
| Control settings section visibility | The policy string, which will either start with the string showonly: or hide:, will indicate the mode. Pages are recognized by a truncated URI that is the URI minus the 'ms-settings:' prefix, which is the URI as it was previously published. Please refer https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-settings#settings-allowworkplace |
Update Settings
Configure update settings on Windows devices.
| Data Key | Policy Description |
|---|---|
| Active hours end | This is used to manage a range of active hours where update reboots are not scheduled. This value sets the end time. There is a 12-hour maximum from start time. |
| Active hours maximum range | Allows admin to specify the max active hours range. This value sets the max number of active hours from start time. Supported values are 8-18. |
| Active hours start | Used to manage a range of hours where update reboots are not scheduled. This value sets the start time. There is a 12-hour maximum from end time. |
| Allow automatic updates | Enables admin to manage automatic update behavior to scan, download, and install updates. |
| Allow automatic updates over metered connections | This is an option to download updates automatically over metered connections. This policy is accessible through the Update setting in the user interface or Group Policy. |
| Allow automatic updates signed by non-microsoft entities | This allows admin to manage whether Automatic Updates accept updates signed by entities other than Microsoft when the update is found at the Update Service URL location. |
| Allow update service | Specifies whether the device could use Microsoft Update, Windows Server Update Services (WSUS), or Microsoft Store. |
| Auto restart deadline in days | Specifies the deadline in days before automatically executing a scheduled restart outside of active hours. The deadline can be set between 2 and 30 days from the time the restart is scheduled. |
| Auto restart deadline in days for feature updates | For Feature Updates, this specifies the deadline in days before automatically executing a scheduled restart outside of active hours. The deadline can be set between 2 and 30 days from the time the restart is scheduled. |
| Notification schedule | This allows admin to specify the period for auto restart reminder notifications. |
| Auto restart notification dismissal | This allows admin to specify the method by which the auto restart required notification is dismissed. |
Wi-Fi Settings
This policy is helped to configure Wi-Fi settings on Windows devices. The users will not be able to modify the settings on their device after the policy applied.
| Data Key | Policy Description |
|---|---|
| Service Set Identifier (SSID) | The identification of the configured Wi-Fi connection. |
| Security | The security type of the configured Wi-Fi connection. |
| Password | Password of the Wi-Fi connection that the device is connected to. |
Group Policies (ADMX)
- Group Policies in Entgra UEM provide administrators with a familiar interface and functionality akin to traditional Group Policy management in Active Directory environments. Leveraging Administrative Template (ADMX) files, administrators can define registry-based policy settings that govern various aspects of device behavior and configuration.
- Administrators can import ADMX templates, configure policy settings, and enforce them across managed Windows devices, ensuring consistent compliance with organizational standards.
- Refer to Microsoft Windows - Understanding ADMX policies for a comprehensive understanding on Windows Group Policy support.
- The following is a list of available Group Policies in Entgra UEM:
Group Policies (ADMX)
- ActiveX Installer Service
- Add or Remove Programs
- App Privacy
- App runtime
- App-V
- Application Compatibility
- Application Diagnostics
- Appx
- Attachment Manager
- Auditing
- AutoPlay Policies
- Background Intelligent Transfer Service
- Camera
- Cloud Content
- Component Object Model
- Connect
- Control Panel
- ControlAltDelete
- Control Panel 2
- Credential User Interface
- Credentials SSP
- DECOM
- DNS Client
- Delivery Optimization
- Desktop Window Manager
- Device Guard
- Device Installation
- Device and Driver Compatibility
- Device Software Setup
- Digital Locker
- Digital Rights 2
- Disk Diagnostic
- Disk Non-Volatile Cache
- Disk Quotas
- Display
- Distributed File System
- Distributed Link Tracking
- Drive Encryption
- Early Launch Antimalware
- Edge UI
- Encrypted Files
- Enhanced Storage Access
- Event Forwarding
- Event Logging
- Event Viewer
- Event Logs
- Fault Tolerant Heap
- File Classification Infrastructure
- File Explorer
- File Recovery
- File History
- File Revocation
- File Share Shadow Copy
- File Sys
- Find My Device
- Folder Redirection
- Frame Panes
- Game DVR
- Group Policy
- Handwriting
- Hotspot Authentication
- Instant Search
- Internet Communication Management
- Internet Explorer
- Internet Information Services
- KDC
- Kerberos
- Kernel DMA Protection
- Lanman Workstation
- Lanman Server
- Leak Diagnostics
- Link Layer Topology
- Location and Sensors
- MMC Snap Ins
- MSI File Recovery
- Maintenance Scheduler
- Management Console
- Media Player
- Messaging
- Microsoft Defender Antivirus
- Microsoft Defender Application Guard
- Microsoft Defender Exploit Guard
- Microsoft Edge - Advanced Browser Management Support for Windows
- Microsoft Input Method Editor
- Microsoft Support Diagnostic Tool
- Microsoft User Experience Virtualization
- Microsoft Account
- Mobile PC Mobility Center
- Mobile PC Presentation Settings
- Multitasking
- Net Logon
- Network Connections
- Network Connectivity Status Indicator
- Network Connectivity Assistant
- Network Isolation
- Network Provider
- Network Sharing
- News and interests
- Notifications
- OOBE
- OS Policy
- Offline Files
- OneDrive
- Online Assistance
- Performance Diagnostics
- Performance Perftrack
- Personalization
- Policies Content Windows Branch Cache
- Portable Operating System
- Power Management
- Previous Versions
- Printing
- Programs
- Push To Install
- Quality of Service
- Regional and Language Options
- Reliability
- Remote Assistance
- Remote Procedure Call
- Removable Storage Access
- Resource Exhaustion Diagnostics
- SNMP
- SSL Configuration Settings
- Scheduled Diagnostics
- Scripted Diagnostics
- Scripts
- Search
- Secondary Authentication Factor
- Security Center
- Server Manager
- Service Control Manager Settings
- Servicing
- Shared Folders
- Shutdown Resolver
- Smart Card
- Software Protection Platform
- Sound Recorder
- Speech
- Start Menu and Taskbar
- Storage Health
- Storage Sense
- Store
- Sync your settings
- System Restore
- TCPIP Settings
- Tablet PC Pen Training
- Tablet PC Shell
- Tablet PC Input Panel
- Taskbar
- Telemetry
- Tenant Restrictions
- Terminal Server
- Terminal Server
- Text Input
- Thumbnails
- Toggle user control over Insider builds
- Touch Input
- Trusted Platform Module Services
- User Profiles
- WinMaps
- Windows Calendar
- Windows Color System
- Windows Defender SmartScreen
- Windows Diagnostics
- Windows Feedback
- Windows Ink Workspace
- Windows Installer
- Windows Logon Options
- Windows Mobile Broadband Service
- Windows PowerShell
- Windows Remote Management
- Windows Security
- Windows iSCSI
- Windows Connect Now
- Windows Connection Manager
- Windows Desktop
- Windows Error Reporting
- Windows Explorer 2
- Windows Help
- Windows Initialization
- Windows Logon
- Windows Logon 2
- Windows Remote Shell
- Windows Time Service
- Windows Tools
- Windows Update
- WlanSvc
- Work Folders
- Refer to https://admx.help/ for more details about admx policies.
Edge Browser Policies
Implement browser restrictions using Microsoft Edge policies to configure how Microsoft Edge runs within your organization. Organizations can use the Entgra UEM ADMX Edge policy feature to set up settings for Microsoft Edge on Windows. Policies can also be configured via the registry. These configurations can be assigned or deployed to Windows devices within your organization.
Note
For more information about available Edge browser policies, please refer to the official documentation at Configure Microsoft Edge policy settings on Windows devices.
Supported Windows OS Versions
- Windows 11
- Windows 10 with the following minimum system requirements:
Supported Browser Versions
Microsoft Edge version 77 and newer (For Microsoft Edge version 45 and earlier, refer to the Microsoft Edge Browser device restrictions documentation).
Refer to Add New Policy section for instructions on how to add a policy to a Windows device.