Enrollment Guide
The Enrollment guide is split into four main sections, taking you through different types of enrollments available for Android, iOs, macOS and Windows devices.
Different device types support different ways of enrollment with the server depending on the features that are required to be supported. Different features supported by enrollment types are described in the features section.
Follow our Cloud Enrollment Guide for enrolling devices via Entgra Cloud.
Detailed explanations and procedures for enrollment are given under each of the following device categories:
Android Enrollment Configurations
This section guides you on how to enroll an Android device.
Android Platform Configurations
Multiple tenants can use Entgra IoTS. While maintaining tenant-based isolation, the Android configurations enable the tenants to customize the Android settings based on their own requirements.
PREREQUISITES
The server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Optionally, Basic Concepts of Android Device Management will be beneficial as well.
Follow the steps given below to configure the Android platform:
-
Click the menu icon.
-
Click CONFIGURATIONS.
-
Click PLATFORM CONFIGURATIONS.
-
Select Android Configurations.
There are 4 main configuration sections for Android:
-
General configurations
-
Policy configurations
-
COPE/Kiosk configurations
-
Android enterprise configurations
General Android Configurations
This section covers details about the preferred communication mechanisms used by Android device for server communication, user agreements and multiple other Android specific general configurations.
Android communication protocol:
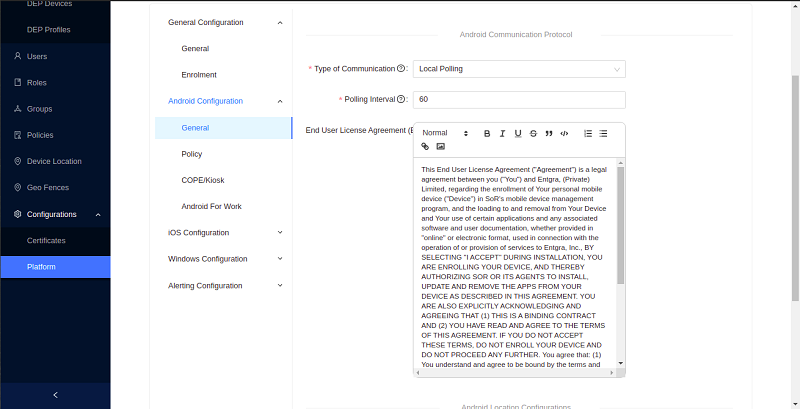
Type of Communication: Configures the preferred communication mechanisms used by Android device to server communication. There are 2 methods of communication available: Local Polling and FCM.
-
Local Polling - The device will contact the Entgra IoT server periodically. When Local poling is selected, a new field called polling interval is enabled. The agent will contact the server and try to fetch commands, based on the interval provided here (in seconds). Note that lowering this number will mean more network callls and high device battery usage. Note: Due to Android restrictions, the minimum frequency here is 60 seconds.
-
Firebase Cloud Messaging (FCM) - FCM will send a notification to the device when there are pending operations available for a specific device. If FCM has been selected as the notifier type, a new field called API key will be enabled where the server key of the FCM configuration needs to be provided. FCM is more network and barrery usage friendly and recommended over local polling. Also note that we do not send any sensitive data over FCM. FCM is mearly a wake up call to the agent and the agent will poll the server when it recieves such a wakeup to fetch the real commands. Note: From Android 4.4 (KitKat) onwards, the OS does not allow applications to trigger wake-up commands when the trigger period is set to less than a minute. Therefore, make sure to set the notifier frequency to 60 seconds or more.
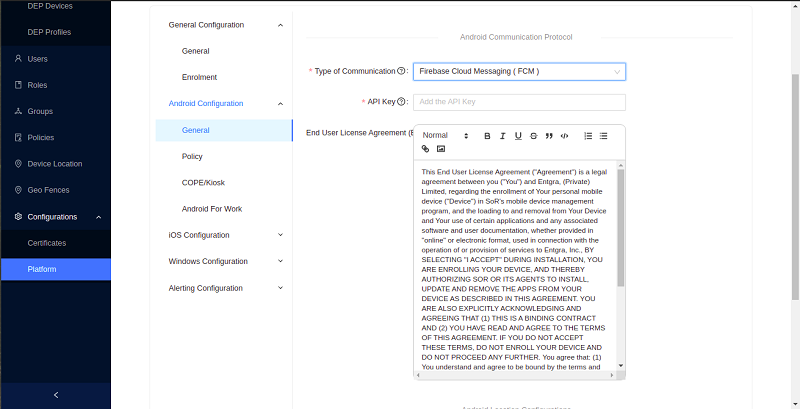
End User License Agreement (EULA) - This text will be shown to a user while enrolling via the agent. This can be used to show the end user agreement or any other information that the user must agree, in order to proceed with enrolment.
Enable Continuous Device Location Publishing - If this is ticked, the server will publish data from devices to the analytics component. Note that the analytics must be enabled and configured prior to enabling this configuration
Enable IoTS Firewall Service - If this is enabled, the agent will to look up the entgra firewall application and start the firewall service. Note this requires certain components which are only available to certain customers. Please contact Entgra for more details
Policy Configurations
The configurations below serve as prerequisites for enforcing certain policies:
| Field | Description |
|---|---|
| Allowing Application List | Set of comma separated package names. This is typically a set of system applications that are always allowed to run on devices. When a policy calculates the applications to be allowed-listed on a device, the list given here is always considered allowed. The reason for this is that certain OS level applications should not be disabled while allow-listing as those apps are critical to the operation of the device. |
| Force device renaming on enrollment | If this is selected, the agent will prompt the user to provide a name for the device at enrolment. The given name will be the name that appears on the endpoint management portal. If this is not selected, the device name provided by the system will be used. |
COPE Kiosk Provisioning Configurations
Fill the fields with required values and click Save to apply the changes to the device.
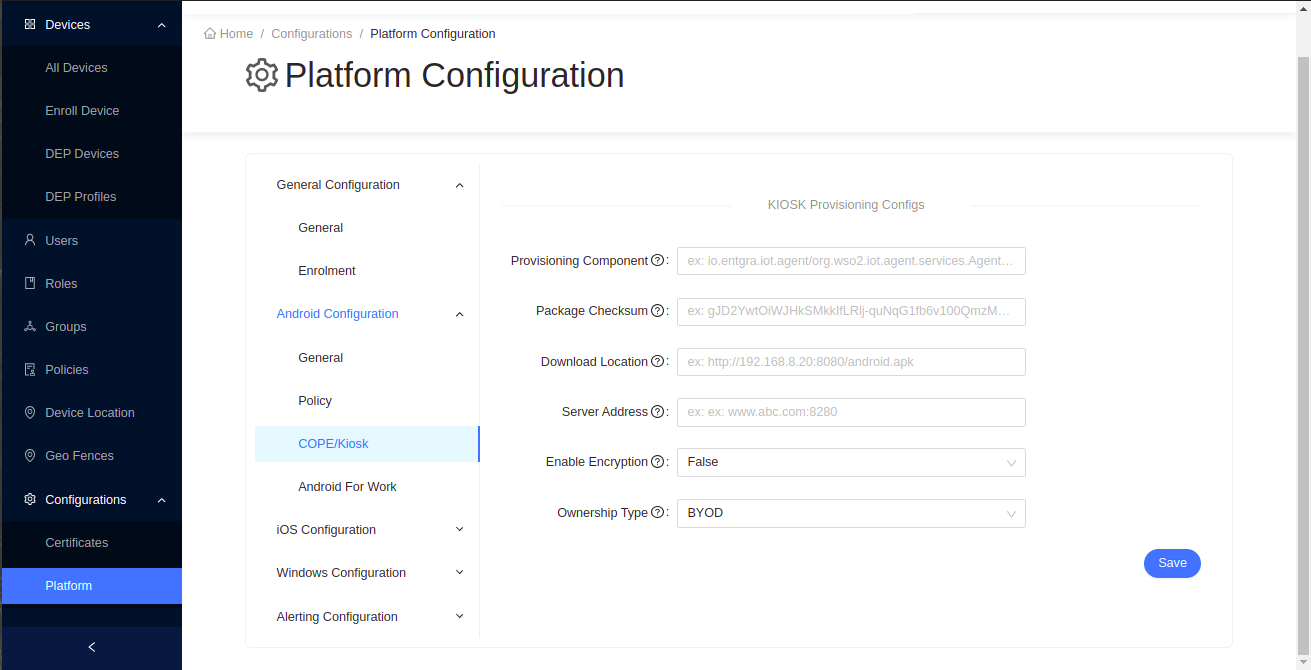
| Field | Details |
|---|---|
| Provisioning Component | Package name of the Entgra Android agent’s device policy manager component. This is always the bellow value, unless the package name is customized io.entgra.iot.agent2/org.wso2.iot.agent.services.AgentDeviceAdminReceiver |
| Package checksum | During the enrollment, this checksum is validated by Android to determine if the downoaded apk matches the checksum. Run the following command to get the checkSum value of the agent, cat <AGENT_APK_FILE_PATH> | openssl dgst -binary -sha256 | openssl base64 | tr '+/' '-_' | tr -d '=' |
| Download Location | Android agent download location. (ex: http://192.168.8.20:8080/android.apk) |
| Server Address | The address of the server. This is used as the server address when enrolling the device. (ex:https://gw.entgra.net:443 |
| Enable Encryption | Upon enrolment if this device must be encrypted, select this option. Not applicable to BYOD devices |
| Enable All System Apps | This will indicate whether all system apps should be enabled after the device is enrolled. |
| Ownership Type | Type of the ownership |
Android Enterprise Configurations
Configure Android Enterprise:
If you want to add Android Enterprise Configuration, enter the required fields and click Save to apply the changes.
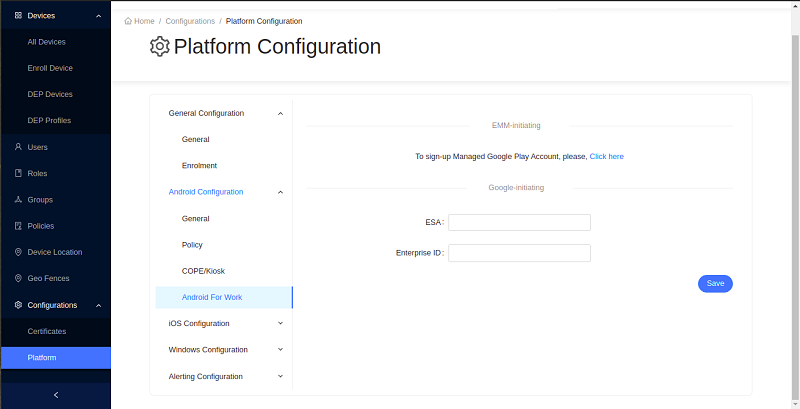
Follow our Android Enterprise Guide for details on the enterprise configurations for Android.
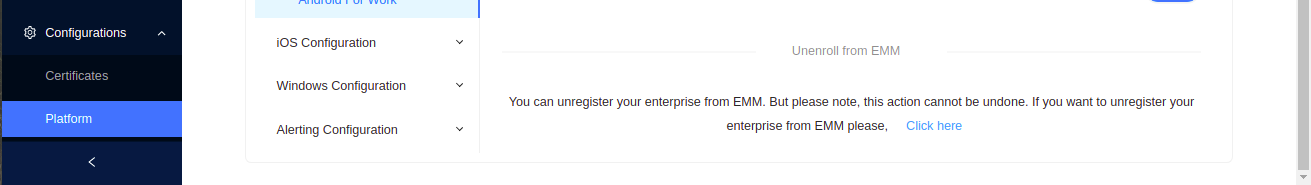
Unenroll Enterprise from EMM
If you want to Unregister your enterprise from the EMM server, click Unenroll. This action cannot be undone.
Installing Entgra Android Device Management App
Android devices are enrolled and managed using an application that is installed on the device, known as the Device Management Agent App. The Entgra Agent app can be installed by downloading it directly either from the Entgra IoT server, or via the Play store, as described below.
Download from Entgra IoT server
There is an agent app bundled with the IoT server and that can be downloaded to your mobile device and installed. >**Prerequisites** > >- The server has to be [downloaded and started](../server). > >- Must have been logged on to the server's [Endpoint Management Portal](../login). 1. Step 1: Click **+ Add** under the **Device** tab. 2. Step 2: Click **Android** under device types. 3. Step 3: Click **Get Android Agent** under device types. 4. Step 4: Scan the QR code using the mobile device. New Android OS version includes the QR code scanning app in-built. If this is not available, a QR code scanning app can be downloaded from the Play Store. Follow the QR code scanned link to download the agent to the device. Alternatively, this page can be assed via the mobile device browser’s itself (follow steps 1-3 on the phone’s broswer) and click on **Download APK** to download the APK to the device. 5. Step 5 Once the app is downloaded, click **Open**. Depending on the OS version of the device, unknown sources has to be enabled to install the agent. In Android 8 and upwards, once you click **Open**, the following screen will be displayed. Select **Allow** from this source and go back. 6. Step 6: Click **Install** to install the agent.Download from the Playstore
>**Prerequisites** > >- The server has to be [downloaded and started](../server). > >- Must have been logged on to the server's [Endpoint Management Portal](../login). Visit the link `https://play.google.com/store/apps/details?id=io.entgra.iot.agent` using your mobile device or go to Google Play Store app in the mobile device and search for Entgra Device Management Agent and install the app.Enroll Android Devices
This section describes the types of enrollment available for Android Devices. The available enrollment types are:
Android Enterprise Enrollment
Refer our Android Enterprise Guide section for the recommended enterprise work profile enrollment.
Fully Managed
Fully Managed type of enrollment is ideal for COPE (corporately-owned personally-enabled) devices where the organization gives out devices for its employees. With granular control over device data and security, and access to Android’s full suite of app management features, this type of enrollment offers comprehensive device management capabilities.
Some of the available features include setting the minimum password requirements on the device, ability to remotely wipe and lock the device, and setting up default responses to app permission requests. It is also possible to remotely install and/or remove apps with this type of enrollment.
Android Device Manual Enrollment as Fully Managed
Prerequisites
The server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Installing Entgra Agent section should have been followed.
Optionally, Basic Concepts of Android Device Management will be beneficial as well.
Steps
-
Enter the following command on terminal or console to enable the device owner.
adb shell dpm set-device-owner io.entgra.iot.agent/org.wso2.iot.agent.services.AgentDeviceAdminReceiver -
Open the Entgra Agent application.
-
Click Continue after reading the Disclaimer that appears.
-
On the next screen that appears next, click Manual Enrollment.
-
Next, click COPE Enrollment in the screen that appears.
-
Type in the server address which is the IP of the server and port as
8280. Click Start Registration. Type in the Username:admin, Password:adminthen click Sign In. -
If you agree to the policy agreement that is shown next, click Agree to proceed.
-
Click Activate in the device screen.
-
Click Allow if you agree to the request for permissions for access to the device as indicated.
-
Click Allow if you agree to using data usage monitoring to allow the server to check the data usage of the device.
-
Allow the agent to change Do not Disturb status which is used to ring the device.
Android Device Enrollment as Fully Managed using QR Code
Prerequisites
The server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Installing Entgra Agent section should have been followed.
Optionally, Basic Concepts of Android Device Management >will be beneficial as well.
- When enrolling a device using QR Code, the the Platform Configurations for an Android device should have been first set.
Steps
-
Open the Entgra Agent application.
-
Click Continue after reading the Disclaimer that appears.
-
In the screen that follows, click Enroll with QR Code.
-
In the server, select device ownership as COPE.
-
Scan QR code that is generated on the server.
-
The enrollment will be on hold until user enables the device owner.
-
Enter the following command in the terminal or on the console to enable device owner.
adb shell dpm set-device-owner io.entgra.iot.agent/org.wso2 .iot.agent.services.AgentDeviceAdminReceiver -
Click Agree in the screen that appears, if you agree to and accept the licence.
Android Device Enrollment as a Dedicated Device
The Dedicated type of Android Device Enrollment, also known as COSU (Corporately-Owned Single-Use), is widely used with fully managed devices that serve a specific purpose. Examples of this type of usage include employee-facing device usage such as in inventory management, field service management, transport, logistics as well as customer-facing device usages like kiosks, digital signage, hospitality check-in etc.
Some of the significant features of Dedicated devices are:
- Lock down devices to specific whitelisted apps
- Block users from escaping locked down devices to enable other actions.
- Set lock screen restrictions
- Device sharing between multiple users (such as shift workers or public-kiosk users)
- Suspend over-the-air (OTA) system updates over critical periods by freezing the OS version.
- Remotely wipe and lock work data
- Automatic compliance enforcement
- Lock app(s) to screen
- Automatic compliance enforcement
- Distribute apps silently
Android Device Enrollment as a Dedicated Device using QR Code
Prerequisites
The server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Installing Entgra Agent section should have been followed.
Optionally, Basic Concepts of Android Device Management >will be beneficial as well.
- When enrolling a device using QR Code, the the Platform Configurations for an >Android device should have been first set.
Steps
-
Set platform configurations as indicated in the prerequisties.
-
Click Enroll Device and select the device type.
-
In the server, select the device ownership as COSU (KIOSK).
-
Tap 6 times on the welcome screen after factory reset. Note: This only works for devices on and above android 9.0.
-
Scan the QR code that is generated on the server.
-
Read the license agreement and the privacy policy and then click Next to proceed with the enrollment.
Android Device Enrollment as a Dedicated Device using QR Code with Entgra Agent
Prerequisites
The server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Installing Entgra Agent section should have been followed.
Optionally, Basic Concepts of Android Device Management >will be beneficial as well.
- When enrolling a device using QR Code, the the Platform Configurations for an Android device should have been first set.
Steps
-
Set platform configurations as indicated in the prerequisites.
-
Click Enroll Device and select the device type.
-
On the server, select the device ownership as COSU (KIOSK).
-
Scan the QR code that is generated on the server.
-
If you agree to the policy agreement is shown, click Agree to proceed.
-
Click Allow if you agree to the request for permissions for access to the device as indicated.
-
Click Allow if you agree to using data usage monitoring to allow the server to check the data usage of the device.
-
Allow the agent to change Do not Disturb status which is used to ring the device.
-
Enter and confirm a PIN code, which is required by the administrator to perform any critical tasks with user consent. Then click Set PIN Code to complete the enrollment.
Android Device Enrollment as a Legacy Device
Legacy enrollment allows you to manage settings and apps on the device. This type of enrollment offers wider control over the device allowing features such as the ones indicated below:
-
Factory Reset Protection (FRP) - for managing devices and for recovering in the event of employee leaving.
-
Reset device passwords - secure this feature on encrypted devices. Block removal of the device administrator.
-
Admin controlled passcodes - that enable locking the user out of a device.
Android Device Legacy Manual Enrollment
Prerequisites
The server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Installing Entgra Agent section should have been followed.
Optionally, Basic Concepts of Android Device Management >will be beneficial as well.
Steps
-
Open the Entgra Agent application.
-
Click Continue after reading the Disclaimer that appears.
-
On the next screen that appears next, click BYOD Enrollment.
-
Click Skip and go to enrollment in the screen that appears next.
-
Type in the server address which is the IP of the server and port as
8280. Click Start Registration. Type in the Username:admin, Password:adminthen click Sign In. -
If you agree to the policy agreement that is shown next, click Agree to proceed.
-
Click Activate in the device screen.
-
Click Allow if you agree to the request for permissions for access to the device as indicated.
-
Click Allow if you agree to using data usage monitoring to allow the server to check the data usage of the device.
-
Allow the agent to change Do not Disturb status which is used to ring the device.
-
Enter and confirm a PIN code, which is required by the administrator to perform any critical tasks with user consent. Then click Set PIN Code to complete the enrollment.
Android Device Legacy Enrollment Using QR Code
Legacy enrollment is deprecated and is designed to take control of the device and data in a BYOD setting.
Prerequisites
The server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Installing Entgra Agent section should have been followed.
Optionally, Basic Concepts of Android Device Management >will be beneficial as well.
- When enrolling a device using QR Code, the the Platform Configurations for an >Android device should have been first set.
Steps
-
Open the Entgra Agent application.
-
Click Continue after reading the Disclaimer that appears.
-
In the screen that follows, click Enroll with QR Code.
-
In the server, select device ownership as BYOD.
-
Scan QR code that is generated on the server.
-
Click Activate in the device screen.
-
Click Allow if you agree to the request for permissions for access to the device as indicated.
-
Click Allow if you agree to using data usage monitoring to allow the server to check the data usage of the device.
-
Allow the agent to change Do not Disturb status which is used to ring the device.
-
Enter and confirm a PIN code, which is required by the administrator to perform any critical tasks with user consent. Then click Set PIN Code to complete the enrollment.
Enroll iOS
This section describes how an iOS device can be enrolled to the IoT server. Before moving into iOS device enrollment it would be beneficial to understand the basic concepts of iOS related MDM concepts.
Additional Server Configurations for Apple Devices
This section takes you through the additional server configurations required for setting up an iOS device.
Apple server configurations, both for iOS and Mac OS are given here in detail along with the platform configurations, based on the required enrollment method.
The configurations necessary for enrolling the device at the Apple DEP (Device Enrollment Program), for both iO and Mac OS, are listed in the section that follows.
Apple (iOS and MacOS) Server Configurations
Prior to enrolling an iOS device, there are some configurations that need to be done on the server.
Although iOS is a supported device type of Entgra IoT server, by default it is not bundled with the server.
Prerequisites
If you have not requested for iOS plugin before, please contact Entgra to get a copy.
If macOS support is needed in the plugin, please mention this in the description. As mentioned in system requirements, maven is needed to install the plugin.
Install iOS plugin
iOS device plugin is not bundled with the server as out-of-the-box and as mentioned in prerequisites, it has to be requested from Entgra. A zip file containing the installable will be sent by Entgra and this can be installed with Maven.
Steps
- Copy the iOS plugin zip mentioned in the prerequisites to
IOT_HOMEfolder and extract. - Using command prompt, goto
IOT_HOME/ios-feature-deployer/folder. - Execute the following command mvn clean install
-f ios-feature-deployer.xml. - When the following question is asked Do you agree? (y,n) Type y and Enter to agree. Else, n to abort.
Run iOS Configurator
iOS configurator is a script designed to cut down certain manual configurations related to iOS.
Steps
- Using command prompt, goto IOT_HOME/ios-configurator/ folder
- Press Enter key to provide the default value and provide the following mandatory information with the server machine’s IP address:
- Common Name
- Server address
Customizing the iOS Bundle ID
If the bundle ID for the iOS agent is changed, the following changes have to be applied to the server configurations.
Steps
-
Open
iot-server.shfile inIOT_HOME/binfolder and search for key-Dagent-bundleand add the agent bundle ID as the value. -
Example
-Dagent-bundle=“org.wso2.carbon.emm.mdmagent”.
Create MDM APNS Certificate
Communication from server to device (OS MDM client) about new commands are delivered through Apple push notification service (APNS). To facilitate this, the IoT server needs to communicate with APNS servers and this requires a special certificate. In order to create an MDM APNS certificate, one of the following is needed,
- MDM vendor signing certificate which allow an EMM vendor to sign MDM APNS certificates for their customers
- Get an MDM vendor to provide you with an MDM APNS certificate
Steps to get Entgra to provide you with an MDM APNS certificate
- Step 1
This is the fastest approach and Entgra provides this server to valid customers. To do this, execute the following 2 commands on the commands prompt. The values provided when running these commands have no operation importance.
openssl genrsa -des3 -out customerPrivateKey.pem 2048
openssl req -new -key customerPrivateKey.pem -out customer.csr
- Step 2
Keep the customerPrivateKey.pem file generate with above commands, secure along with the password used for private key. Email customer.csr file along with a description about the project details to contact@entgra.io to get a MDM APNS certificate. After an evaluation of the request, Entgra may send a file called plist_encoded
- Step 3
Go to the Apple Push Certificate Portal at https://identity.apple.com/pushcert/ and log in with an Apple ID. It is highly recommended not to use personal Apple IDs for this process and to create a separate Apple ID for the organization. This Apple ID is needed when these certificate needs to be renewed and failure to access this Apple ID in the future will result in having to re-enrol all the devices in production.
- If you are trying to renew the certificate, click Renew.
- If not, Click Create Certificate and agree to the terms and conditions.
- Upload the encoded
plist_encodedfile you received via email from Entgra. -
Download the generated MDM signing certificate
(MDM_Certificate.pem). The MDM signing certificate is a certificate for 3rd party servers provided by Apple. -
Step 4
Run the following command and note down the userID value in the output. This will later be indentified as the topic ID.
`openssl x509 -in MDM_Certificate.pem -text -noout`
- Step 5
Run the following 2 commands,
`openssl rsa -in customerPrivateKey.pem -out customerKey.pem
cat MDM_Certificate.pem customerKey.pem > MDM_APNSCert.pem`
- Step 6
Open the MDM Apple Push Notification service (APNs) Certificate (MDM_APNSCert.pem) and ensure that there is a line break between the contents of the two files.
Example: The content will look as follows:
—–END CERTIFICATE———-BEGIN RSA PRIVATE KEY—–
Therefore, add a line break to separate the 2 certificates after 5 - (dashes) so that the content will look like what’s shown below:
`-----END CERTIFICATE-----
-----BEGIN RSA PRIVATE KEY-----`
- Step 7
Run the following command to convert the MDM_APNSCert.pem file to the MDM_APNSCert.pfx file. You will need to provide a password when converting the file.
`openssl pkcs12 -export -out MDM_APNSCert.pfx -inkey customerPrivateKey.pem -in MDM_APNSCert.pem'
Decide Your Enrollment Method
Before moving on to next steps, a decision needs to be made according to the features required for the business usecase. As mentioned previously, iOS and MacOS has an in-built MDM client which is capable of performing majority of management tasks. However the agent is needed, if the business requirement needs the following feature,
- Location tracking
- Ring the device
- Send a short notification message to device
If the above 3 features are not mandatory, please skip ahead to adding Platform Configurations section.
Create Agent APNS Certificate
This certificate is required to carry out operations on the device that need to be triggered via the iOS agent, such as ringing the device, getting the device location, and sending notifications or messages to the device. Therefore, if you are not installing the iOS agent on your devices, you do not need this certificate and this section can be skipped.
- **Prerequisites- **
- You have to be enrolled in the Apple Developer Program as an individual or an organization before starting the iOS server configurations.
- A valid distribution certificate that you obtained from Apple.
- Step 1 Clone the ios-agent repository to a preferred location.
git clone https://gitlab.com/entgra/ios-agent
- Step 2
Open the emm-agent-ios from X-Code and follow the subsequent steps:
-
Change the org.wso2.carbon.emm.mdmagent Bundle Identifier to a value prefered. Example:
org.<ORGANIZATION_NAME>.emm.ios.agent -
Select the development team, provisioning profile and sign certificate from Xcode.
-
If you are unsure of how to select the development team, or adding the provisioning profile or signing the certificate via Xcode, see the blog post on How to export “in-house” developed iOS app as an enterprise application.
-
Step 3
Log in to the Apple Developer program and follow the subsequent steps:
-
Before you follow the steps, confirm that your machine is connected to the Internet and that Xcode has a valid developer account.
-
Navigate to Certificates, IDs & Profiles that is under Identifiers. Click App IDs and see if the Bundle ID that you defined under Xcode is listed here.
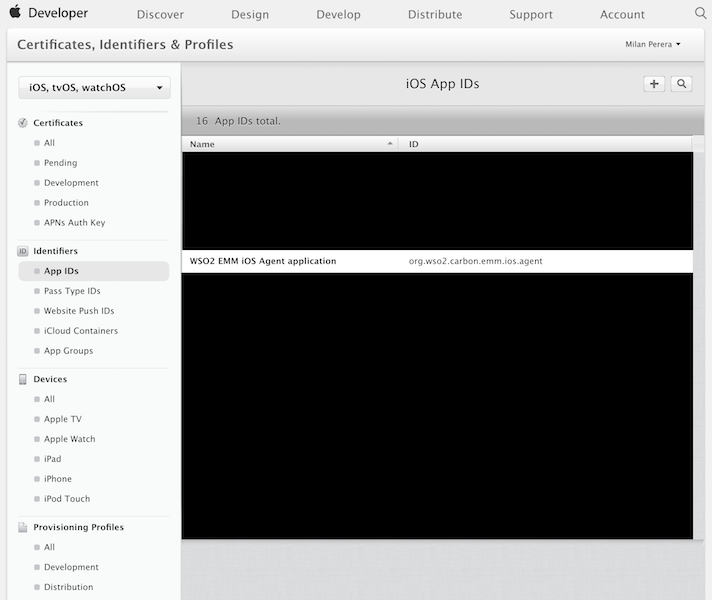
- Step 4
Click the Bundle ID, and click Edit.
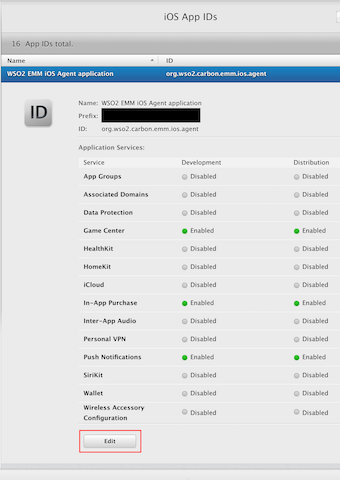
- Step 5
Creating an APNs SSL certificate:
Step 1. Select Push Notifications to enable the setting.
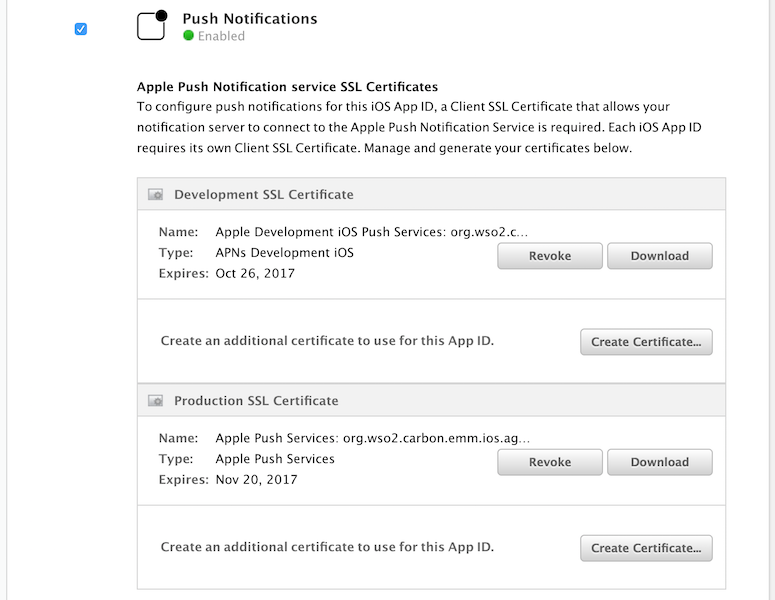
Once push notification is enabled, you are able to generate the development and production certificates.
Step 2. To try out the create certificate use case, let us create a development SSL certificate. Please note that the development SSL certificate is created only as an example. You can create a production SSL certificate if you have registered with the Apple Developer Program as an Organization.
Click Create Certificate that is under Development SSL Certificate.
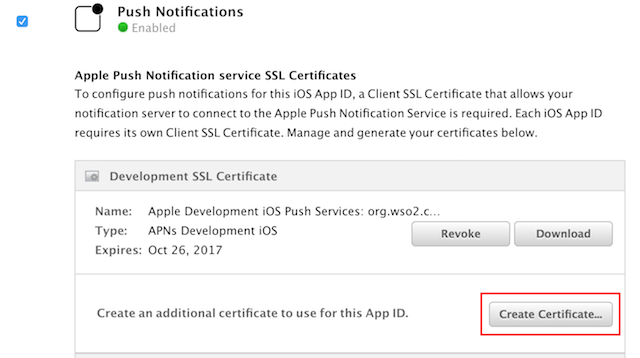
- Step 6
Creating a CSR file using the keychain access tool in the Mac OS:
Step 1. Launch the keychain access application. Step 2. On the menu bar click KeyChain Access > Certificate Assistant > Request a Certificate from Certificate Authority.
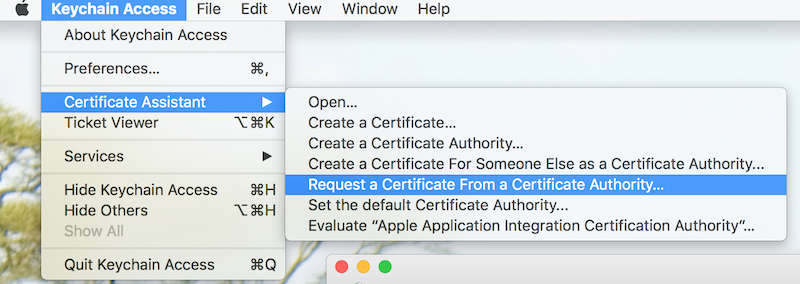
- Step 3
Define the email address, common name, select Saved to disk, and click Continue.
Example:
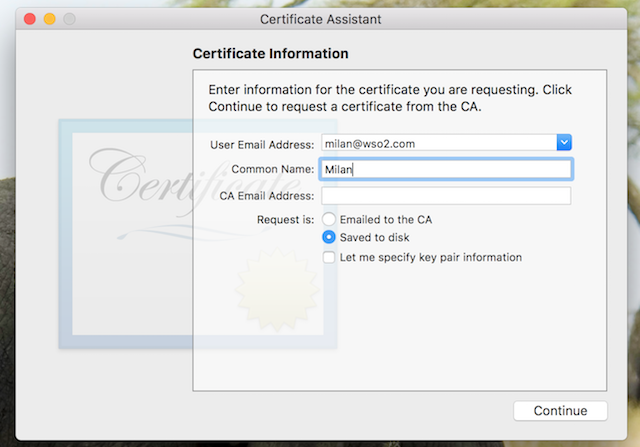
- Step 7
Go back to the Apple Developer Portal, upload the generated certificate, and click Continue.
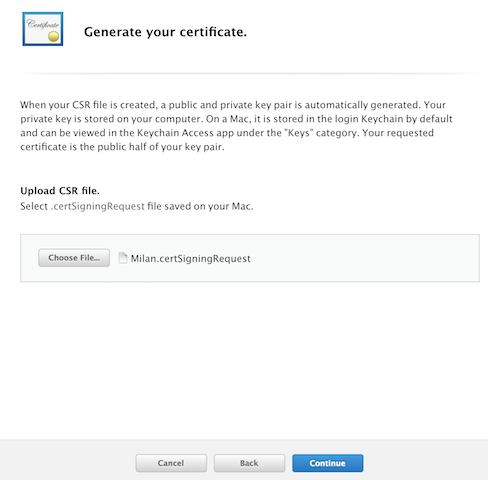
- Step 8
Exporting the certificate to the pfx format.
-
Click Download to download the file.
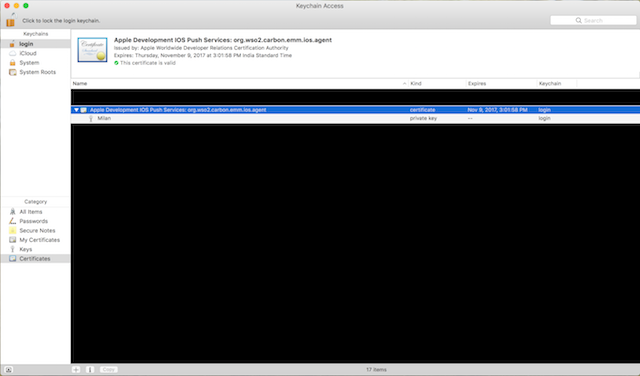
-
Double-click the downloaded file to open it with the Keychain access tool.
-
Right-click the certificate and select export.
-
Define the location where you wish to save the file and set a password for the exported file when prompted.
-
Rename the p12 extension of the file to pfx.
Add Platform Configurations
Before proceeding, note, if you require Apple DEP support, please complete Apple DEP configurations section first.
Steps
-
Log in to the device management console and Click > CONFIGURATION MANAGEMENT > PLATFORM CONFIGURATIONS > iOS Configurations and fill in the form with values you wish.
-
Use the generated MDM-APNS certificate for both the MDM certificate and the generated APNS certificate for the APNS certificate.
-
MDM Certificate: Upload the MDM APNS pfx file created
(MDM_APNSCert.pfx)
MDM Certificate Password: Give the same password you gave when converting the MDM_APNS certificate from the pem to the pfx format.
MDM Certificate Topic ID: Give the topic ID of the certificate. If you are unsure of the topic ID, refer step 6 under generating the MDM APNS certificate.
APNS Certificate: If you are using Agent and completed Create agent APNS certificate section, please use that pfx. If not upload the MDM_APNSCert.pfx here as well APNS
Certificate Password: Give the same password you gave when converting the Agent APNS certificate to the pfx format. If Agent is not used, provide the same password as MDM_APNSCert.pfx
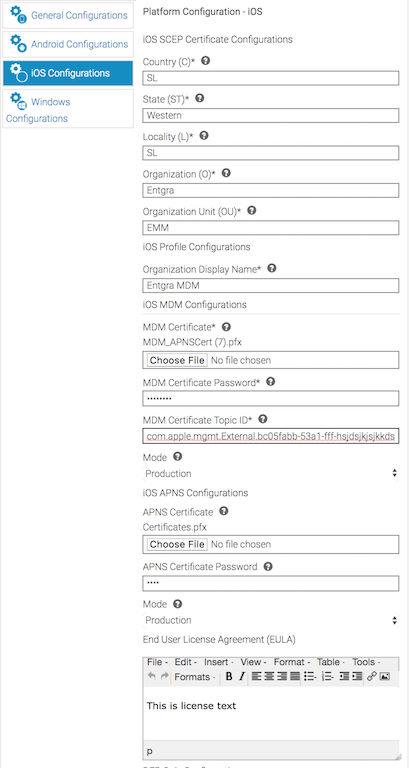
Tip: To learn more about each platform setting, hover your mouse pointer over the help tip.
Apple (iOS and MacOS) DEP Configurations
Device Enrollment Program (DEP) is a program provided by Apple to allow device management solutions to have control over corporate-owned devices. Let us take a look at what you need to do, to get started and understand why you need DEP.
Prerequisites
Apple server configurations must have been completed.
Benefits of using DEP Enables Zero Touch Provisioning (ZTP) for device enrollments for the convenience of IT administrators. Provides better control over iOS devices and provides the features described in the features section. Restrict the user from removing EMM Management from the device. Enrolling the Apple Device in the Enrollment Program The first step is to enroll your organization with Apple Device Enrollment Program (DEP) and link Entgra IoT Server’s EMM solution to your DEP portal. Follow the steps given below to enroll with DEP.
Steps ... Generate a DEP Token to Link EMM with Apple Now that the DEP account is created, EMM server must be made aware of this DEP account. In order to allow EMM server to talk to Apple DEP servers and link with the DEP account, a special server token has to be generated from Apple DEP portal and passed to EMM server.
Prerequisites
Download and install OpenSSL. Linux OS's have OpenSSL installed by default.
Steps ... Linking the Entgra with Apple DEP You can configure the device startup settings (activation) of the iOS devices, to skip configurations or include additional configurations. This is done by creating profiles in Entgra IoT Server and assigning them to the devices.
Steps ... Adding Devices to the Apple DEP Portal The Apple Device Enrollment Program (DEP) allows iOS devices purchased through the DEP program as well as those purchased outside of the program to be enrolled as supervised devices to a mobile device management system. You are required to add the devices to the Apple DEP portal to link the devices with the DEP system.
Adding Devices Purchased via DEP Steps ... Adding iOS Devices using the Apple Configurator The devices purchased outside DEP can be added manually to the DEP account. You need to plug in each device to a Mac and factory reset the device using THE Apple Configurator. Follow the steps given below:
Prerequisites
Devices that have an OS that is iOS 11 or higher. Apple Configurator 2.5 or higher.
Steps ... Creating and Assigning Activation Profiles to Devices Steps ... Enrolling DEP Devices Please refer iOS DEP Device enrollment section.
Enroll as BYOD
iOS Device Enrollment (BYOD) without Agent
Prerequisites
Server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Click Add Device
(https://{IP}:{port}/devicemgt/device/enroll).Click iOS under DEVICE TYPES.
Scan the QR code that appear with a QR code scanning app or type
https://{IP}:{port}/ios-web-agent/enrollmentin safari browser.
If the Device is above iOS 12.2
(If you have installed OS updates after March 2019)
If the Device is bellow iOS 12.2
iOS Device Enrollment (BYOD) with Agent
Prerequisites
Server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Click Add Device
(https://{IP}:{port}/devicemgt/device/enroll).Click iOS under DEVICE TYPES.
Scan the QR code that appears with a QR code scanning app or type
https://IP:port/ios-web-agent/enrollmentin safari browser.
If the Device is above iOS 12.2
(If you have installed OS updates after March 2019)
If the Device is below iOS 12.2
iOS DEP Enrollment
iOS DEP Device Enrollment (with/without agent)
All you need to do is start up the iOS device that was given to you by your organization and your device will be enrolled with EMM as a DEP device.
If your organization has configured the DEP profile to prompt for your username and password, you need to enter the username and password that is used within the organization.
Enroll macOS
Enroll macOS Device Manually
Prerequisites
The server has to be downloaded and started.
Must have been logged on to the server's Endpoint Management Portal.
Click iOS from DEVICE TYPES.
Type
https://{IP}:{port}/ios-web-agent/enrollmentin safari browser.
Steps
-
Copy the URL of QR code to the browser of the mac OS device.
-
Click Enroll without agent.
-
Click Install IoT Server Certificate.
-
Open Key Chain Acess Application.
-
Open the downloaded IoT Server Certificate.
-
Set trust to Always trust for the downloaded IoT Server Certificate.
-
Click Next.
-
Type the Username:
admin, Password:adminthen click Sign in. -
Accept the Licence Agreement to continue.
-
You will be prompted to confirm the installation of the profile to the device. Then click Install to install the profile to the device.
-
You will be prompted to confirm the installation of the Mobile Device Management profile. Then click Install to install the Mobile Device Management profile to the device.
Enroll Windows
Windows Server Configuration
The Entgra IoTS client sends requests to the Entgra IoTS server through a Proxy Server. The Windows Entgra IoTS protocol constructs a URI that uses the host name by appending the domain of the email address to the subdomain, enterpriseenrollment for the each device request. Therefore, you can either purchase a domain name or create a DNS entry in the http://enterpriseenrollment.
For example, discover the Entgra IoT server by sending a request through: http://enterpriseenrollment.
As the Entgra IoT server can not create Windows service endpoints it is advisable to use a proxy server between the device and the Entgra IoT server.
The following subsections are given as examples to guide you on how to configure the proxy server for Windows. You can use any proxy server for this task but we recommend that you use NGINX as it is simple to try out.
Nginx Configuration
A preferred server can be used as a proxy server between the device and the Entgra IoT server. The steps documented below is only an example of configuring the proxy server using NGINX, which is a known reverse proxy server. Follow the steps given below to configure the proxy Server: 1. Install NGINX in your production environment. Refer the following to install NGINX on a MAC or Ubuntu environment. * [nginx installation guide](https://docs.nginx.com/nginx/admin-guide/installing-nginx/installing-nginx-open-source/) 2. Get an SSL certificate. Make sure that the common name of the certificate you are getting matches the constructed URI. {{< hint info >}} The Entgra IoTS client sends requests to the Entgra IoTS server through a Proxy Server. The Windows Entgra IoTS protocol constructs a URI that uses the hostname by appending the domain of the email address to the subdomain, enterpriseenrollment for each device request. Therefore, you can either purchase a domain name or create a DNS entry in the http://enterpriseenrollment.EMAIL_DOMAIN format. {{< /hint >}} ### To Create the SSL certificate * Create a file called openssl.cnf with the below content[req]
distinguished_name = req_distinguished_name
req_extensions = v3_req
[req_distinguished_name]
countryName = SL
countryName_default = SL
stateOrProvinceName = Western
stateOrProvinceName_default = Western
localityName = Colombo
localityName_default = Colombo
organizationalUnitName = ABC
organizationalUnitName_default = ABC
commonName = dev.abc.com
commonName_max = 64
[ v3_req ]
# Extensions to add to a certificate request
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = dev.abc.com
DNS.2 = enterpriseenrollment.dev.abc.com
openssl genrsa -out server.key 2048
openssl req -new -out server.csr -key server.key -config openssl.cnf
openssl x509 -req -days 3650 -in server.csr -signkey server.key -out server.crt -extensions v3_req -extfile openssl.cnf
#user nobody;
worker_processes 1;
#error_log logs/error.log;
#error_log logs/error.log notice;
#error_log logs/error.log info;
#pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
#access_log logs/access.log main;
sendfile on;
#tcp_nopush on;
#keepalive_timeout 0;
keepalive_timeout 65;
#gzip on;
server {
listen 8080;
server_name localhost;
#charset koi8-r;
#access_log logs/host.access.log main;
location / {
root html;
index index.html index.htm;
}
#error_page 404 /404.html;
# redirect server error pages to the static page /50x.html
#
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root html;
}
# proxy the PHP scripts to Apache listening on 127.0.0.1:80
#
#location ~ \.php$ {
# proxy_pass http://127.0.0.1;
#}
# pass the PHP scripts to FastCGI server listening on 127.0.0.1:9000
#
#location ~ \.php$ {
# root html;
# fastcgi_pass 127.0.0.1:9000;
# fastcgi_index index.php;
# fastcgi_param SCRIPT_FILENAME /scripts$fastcgi_script_name;
# include fastcgi_params;
#}
# deny access to .htaccess files, if Apache's document root
# concurs with nginx's one
#
#location ~ /\.ht {
# deny all;
#}
}
# another virtual host using mix of IP-, name-, and port-based configuration
#
#server {
# listen 8000;
# listen enterpriseenrollment.dilan.me;
# server_name somename alias another.alias;
# location / {
# root html;
# index index.html index.htm;
# }
#}
# HTTPS server
#
#server {
# listen 443 ssl;
# server_name localhost;
# ssl_certificate cert.pem;
# ssl_certificate_key cert.key;
# ssl_session_cache shared:SSL:1m;
# ssl_session_timeout 5m;
# ssl_ciphers HIGH:!aNULL:!MD5;
# ssl_prefer_server_ciphers on;
# location / {
# root html;
# index index.html index.htm;
# }
#}
server {
listen 443 ssl;
server_name enterpriseenrollment.dilan.me;
ssl on;
ssl_certificate /usr/local/etc/nginx/ssl/certificate.crt;
ssl_certificate_key /usr/local/etc/nginx/ssl/private.key;
location /EnrollmentServer/Discovery.svc {
if ($request_method = GET) {
return 200;
}
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://192.168.8.100:8280/api/device-mgt/windows/v1.0/discovery/post;
proxy_http_version 1.1;
}
location /ENROLLMENTSERVER/PolicyEnrollmentWebservice.svc {
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://192.168.8.100:8280/api/device-mgt/windows/v1.0/certificatepolicy/xcep/1.0.0;
proxy_http_version 1.1;
}
location /windows-web-agent {
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://192.168.8.100:9763/windows-web-agent;
proxy_http_version 1.1;
}
location /ENROLLMENTSERVER/DeviceEnrollmentWebservice.svc {
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://192.168.8.100:8280/api/device-mgt/windows/v1.0/deviceenrolment/wstep/;
proxy_http_version 1.1;
}
location /ENROLLMENTSERVER/Win10DeviceEnrollmentWebservice.svc {
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://192.168.8.100:8280/api/device-mgt/windows/v1.0/deviceenrolment/enrollment;
proxy_http_version 1.1;
}
location /Syncml/initialquery {
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://192.168.8.100:8280/api/device-mgt/windows/v1.0/syncml/devicemanagement/1.0.0/request/;
proxy_http_version 1.1;
}
location /devicemgt {
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://192.168.8.100:8280/api/device-mgt/windows/v1.0/management/devicemgt/1.0.0/pending-operations/;
proxy_http_version 1.1;
}
}
include servers/*;
}
server {
listen 443;
server_name enterpriseenrollment.wso2.com;
ssl on;
ssl_certificate /usr/local/etc/nginx/ssl/star_wso2_com.crt;
ssl_certificate_key /usr/local/etc/nginx/ssl/enterpriseenrollment_wso2_com.key;
location /ENROLLMENTSERVER/PolicyEnrollmentWebservice.svc {
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://10.10.10.10:8280/api/device-mgt/windows/v1.0/certificatepolicy/xcep;
proxy_http_version 1.1;
}
Apache2 HTTP configuration
Any preferred server can be used as a proxy server between the device and the Entgra IoT server. The steps documented below is only an example of configuring the proxy server by using the Apache2 HTTP Server. The Apache Server can be configured using the forward or reverse proxy (also known as gateway) mode. The reverse proxy mode is used to configure Apache2\. You can download the Apache2 HTTP Server from [here](https://httpd.apache.org/download.cgi). Follow the steps given below to configure the proxy Server: #### Step 1: Configure reverse proxy A reverse proxy (or gateway) appears to the client like an ordinary web server with no special configuration required for the client. Ordinary requests for content is made by the client through the `name-space`. The reverse proxy redirects the requests, and returns the required output. The following modules are required to configure the reverse proxy: * `mod_proxy.so` This module deals with proxying in Apache. * `mod_proxy_http.so` This module handles connections with both the HTTP and HTTPS protocols. 1. Navigate to the `etc/apache2` directory and use the following command to enable the above modules: cd /etc/apache2 a2enmod proxy_http 2. Configure the `proxy.conf` file that is in the `/etc/apache2/mods-available` directory by including the configurations given below to the end of the file. ServerName localhost
ProxyRequests off
ProxyPreserveHost off
<Proxy *>
Order deny,allow
#Deny from all
Allow from all
</Proxy>
ProxyPass /ENROLLMENTSERVER/PolicyEnrollmentWebservice.svc http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/services/certificatepolicy/xcep
ProxyPassReverse /ENROLLMENTSERVER/PolicyEnrollmentWebservice.svc http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/services/certificatepolicy/xcep
ProxyPass /ENROLLMENTSERVER/DeviceEnrollmentWebservice.svc http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/services/deviceenrolment/wstep
ProxyPassReverse /ENROLLMENTSERVER/DeviceEnrollmentWebservice.svc http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/services/deviceenrolment/wstep
ProxyPass /Syncml/initialquery http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/services/syncml/devicemanagement/request
ProxyPassReverse /Syncml/initialquery http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/services/syncml/devicemanagement/request
ProxyPass /ENROLLMENTSERVER/Win10DeviceEnrollmentWebservice.svc http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/deviceenrolment/enrollment
ProxyPassReverse /ENROLLMENTSERVER/Win10DeviceEnrollmentWebservice.svc http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/deviceenrolment/enrollment
ProxyPass /devicemgt http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/management/devicemgt/pending-operations
ProxyPassReverse /devicemgt http://<server-ip>:<server-port>/api/device-mgt/windows/v1.0/management/devicemgt/pending-operations
ProxyPass /windows-web-agent http://server-ip>:<server-port>/windows-web-agent
ProxyPassReverse /windows-web-agent http://server-ip>:<server-port>/windows-web-agent
The default `<server-ip>:<server-port>` is `localhost:9443.`
Enrolling a Windows Device
- add an entry to the windows host files, for example:
192.168.8.100 dev.abc.com
192.168.8.100 enterpriseenrollment.dev.abc.com
-
Go to windows Settings > Accounts > Access to work or school > Enroll only in device management
-
A new window will appear to setup a work or school account. enter the email as:
admin@dev.abc.com
[!NOTE]
dev.abc.com is the dns provided when setting up the host file.
- once the email is submitted, the wizard will search for the organization and open a new window to log in to the IoT server admin. Once the login process is completed, it will enroll the device sync the policies
Additional Server Configurations for Windows
Multiple tenants can use Entgra IoTS while, maintaining tenant based isolation. The Windows configurations enable the tenants to customize the Windows settings based on their own requirements.
Follow the steps given below to configure the Windows platform:
-
Sign in to the Entgra IoT Console.
-
Click Configurations.
-
Select Platform configurations.
-
Go to Windows Configurations.
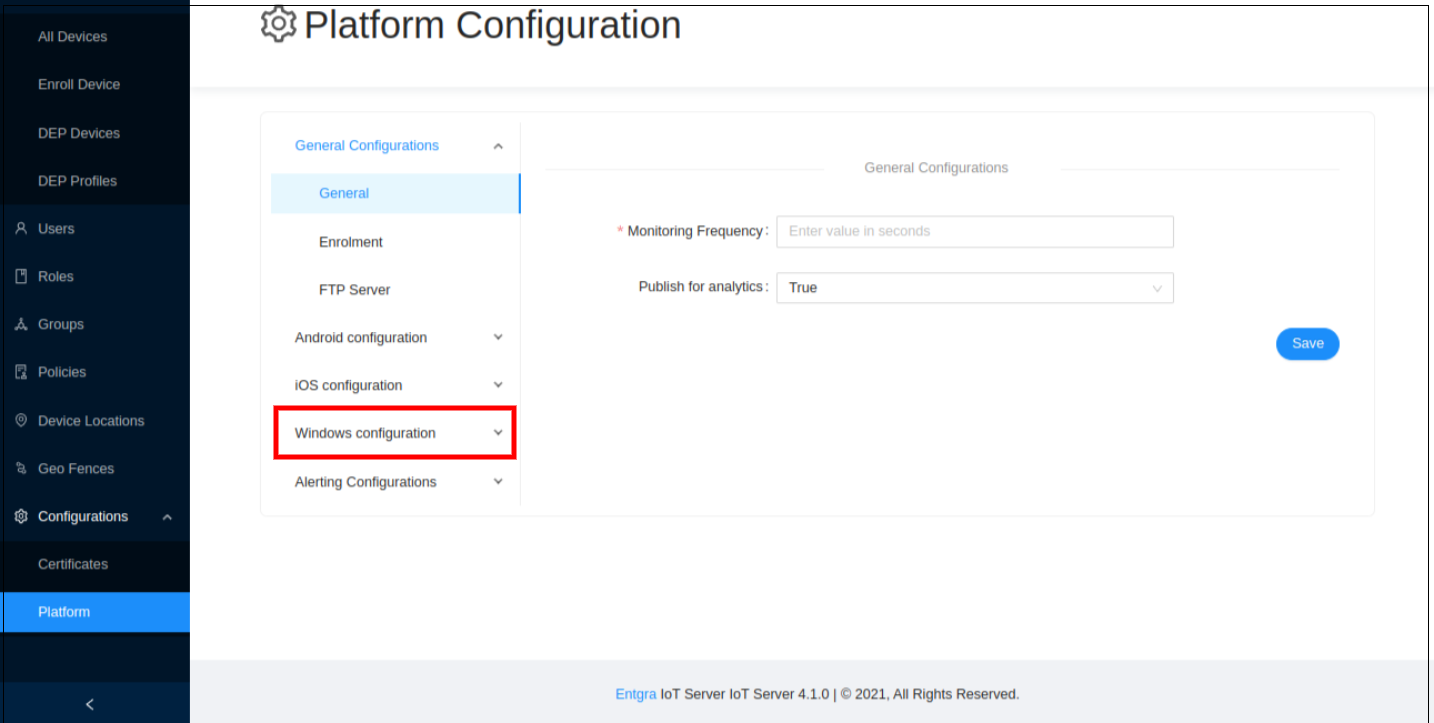
-
Select General Configurations.
-
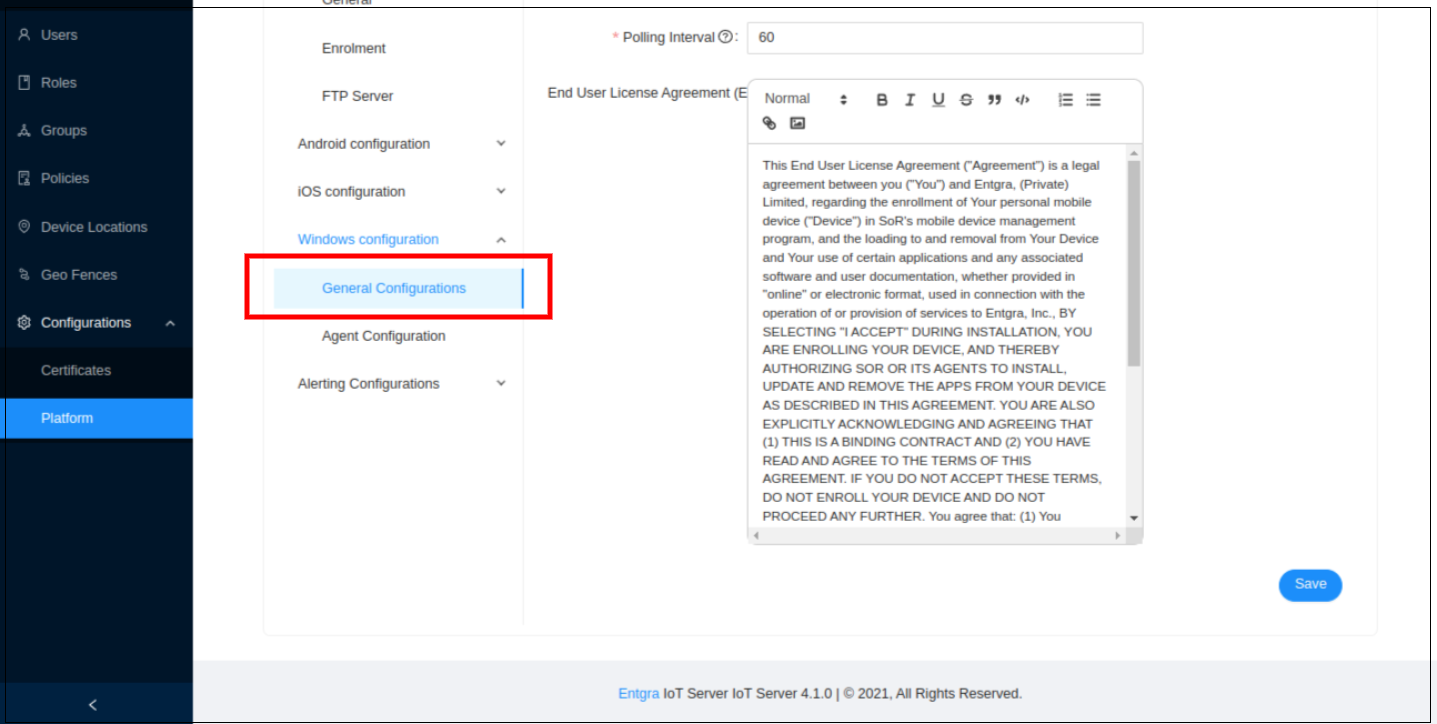
Enter the following:
-
Polling Interval - Specify the time period for the wake-up command to automatically trigger the Entgra IoT client as the notifier frequency. Ensure to specify the notifier frequency in seconds.
-
End User License Agreement (EULA) - Provide the license agreement that a user must adhere to, when enrolling an Windows device with Entgra IoT Server.
-
-
Click SAVE.
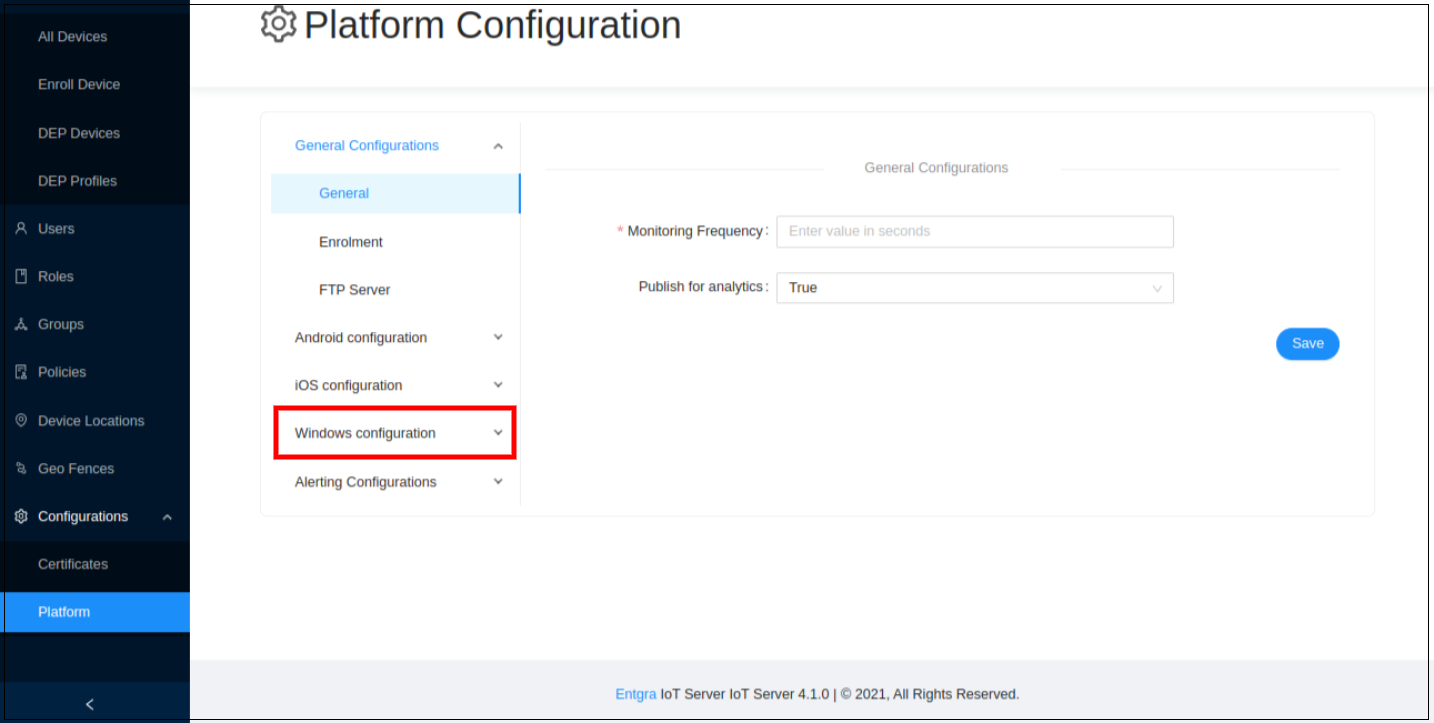
NOTE: Apart from the General Configurations, there is Windows Agent Configuration as well.
-
Go to Windows Configurations.
-
Select Agent Configuration.
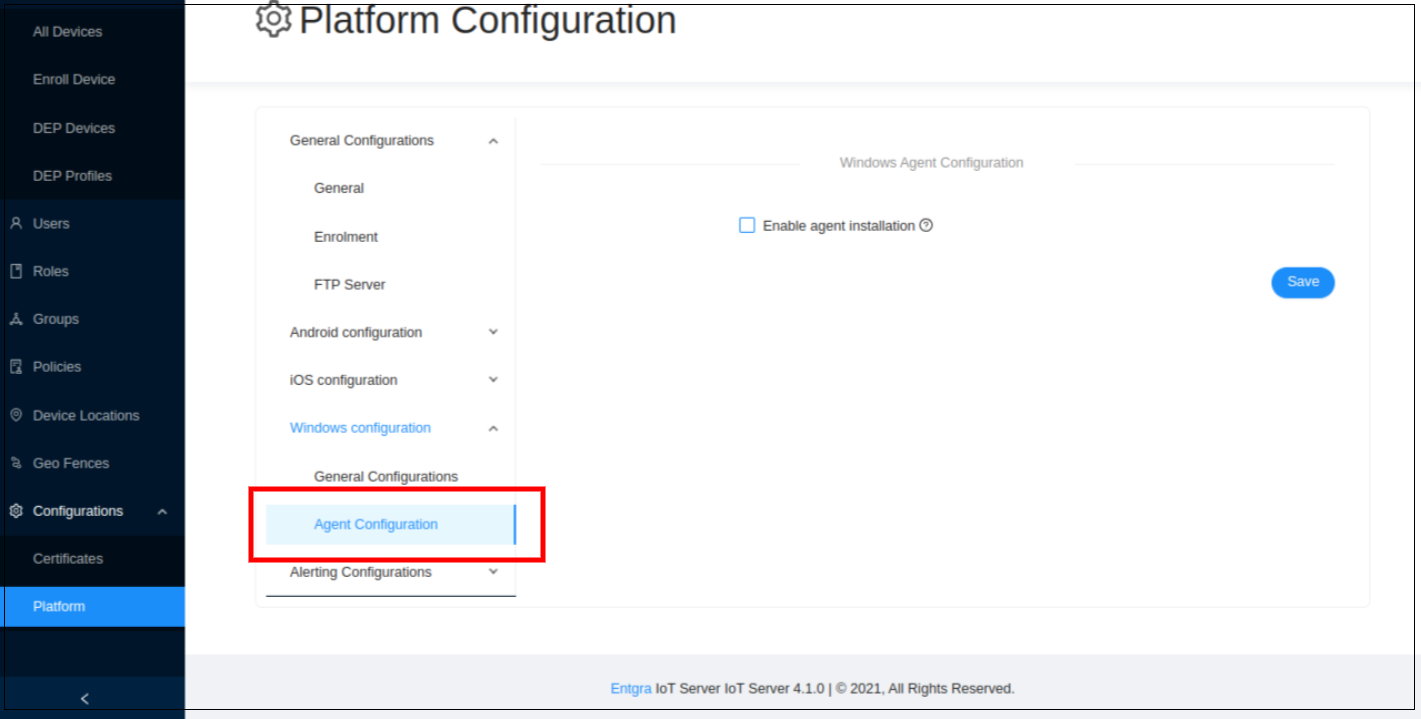
-
Click Enable Agent installation.
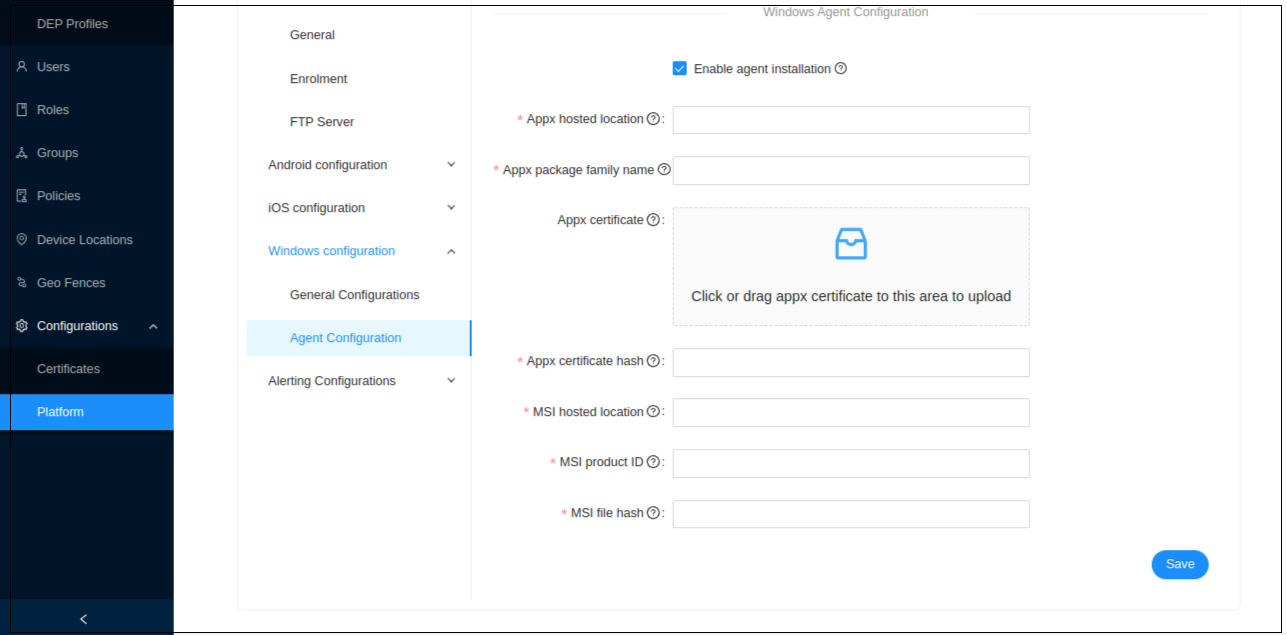
-
Enter the requested information given below:
-
Appx Hosted Location - Location of the appx package of the Windows agent where it hosted
-
Appx Package Family Name - This field should contain the family name of the Windows agent package
-
Appx Certificate - Upload the appx certificate
-
Appx Certificate Hash - Hash number of the appx certificate
-
MSI Hosted Location - Location of the MSI package of the Windows agent where it hosted
-
MSI Product ID - The product id is a GUID identifying Windows Installer package. It associates with an MSI file and can be used to verify sources
-
MSI File Hash - Hash number of the MSI file that needs to configure the MSI file for agent installation
-
Enroll a Windows Device
PREREQUISITES
- Server has to be downloaded and started.
- Must have been logged on to the server's Endpoint Management Portal.
- Click Add device
(https://{IP}:{port}/devicemgt/device/enroll).- Click Windows from DEVICE TYPES.
Steps
- Add host configuration to the windows host files.
- Add the server certificate to trusted root certification authorities.
- Go to access to work or school in Windows settings.
- Click enroll only in device management.
- Input
admin@in the pop-up window.
Enrollment Issue Diagnosis
You may encounter issues while trying to enroll your Windows devices to the server. There are tools that can help diagnose the enrollment or device management issue accurately for Windows devices managed by the MDM server. By using these tools, you can examine the MDM logs collected from the desktop to determine the root cause of the issue.
- How to Diagnose MDM Failure in Windows 10
Reference: Diagnose MDM failures in Windows 10
Follow the steps below to download the MDM Diagnostic Information log from Windows PC:
- Enroll the device to the MDM server.
- Go to Settings > Accounts > Access Work or School.
- Click on the Info button of the account.
- At the bottom of the page, select the Create Report button under Advanced Diagnostic Report section.
- Click Export.
- Go to C:/Users/Public/Documents/MDMDiagnostics to see the exported report.
That report contains detailed information on the areas given below:
- Device info
- Connection info
- Device management account
- Certificates
- Enrolled configuration sources and target resources
- Managed policies
- GPCSEWreapper policies
- Blocked grouped policies
-
Unmanaged policies
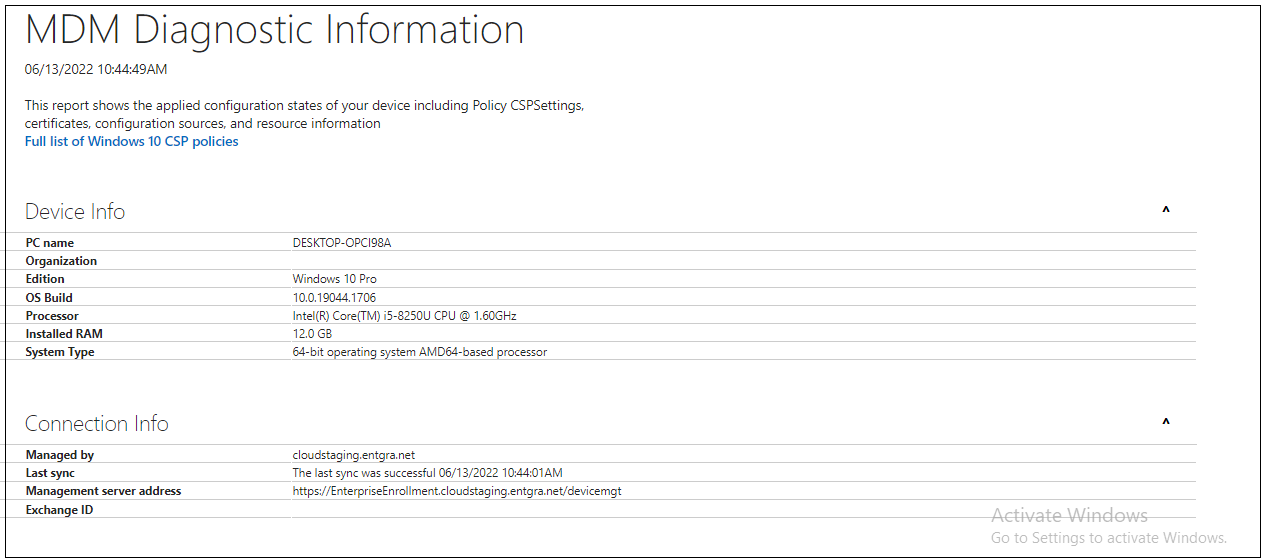
Before you work with Fiddler, you have to install it to the Windows machine that you want to diagnose.
- Enroll the device to the MDM server.
-
Go to this link to download the Fiddler: https://www.telerik.com/download/fiddler?_ga=2.66045742.1046222453.1655091182-1922922192.1653555788
-
Install it to the machine.
- Open Fiddler Classic.
- Event Viewer
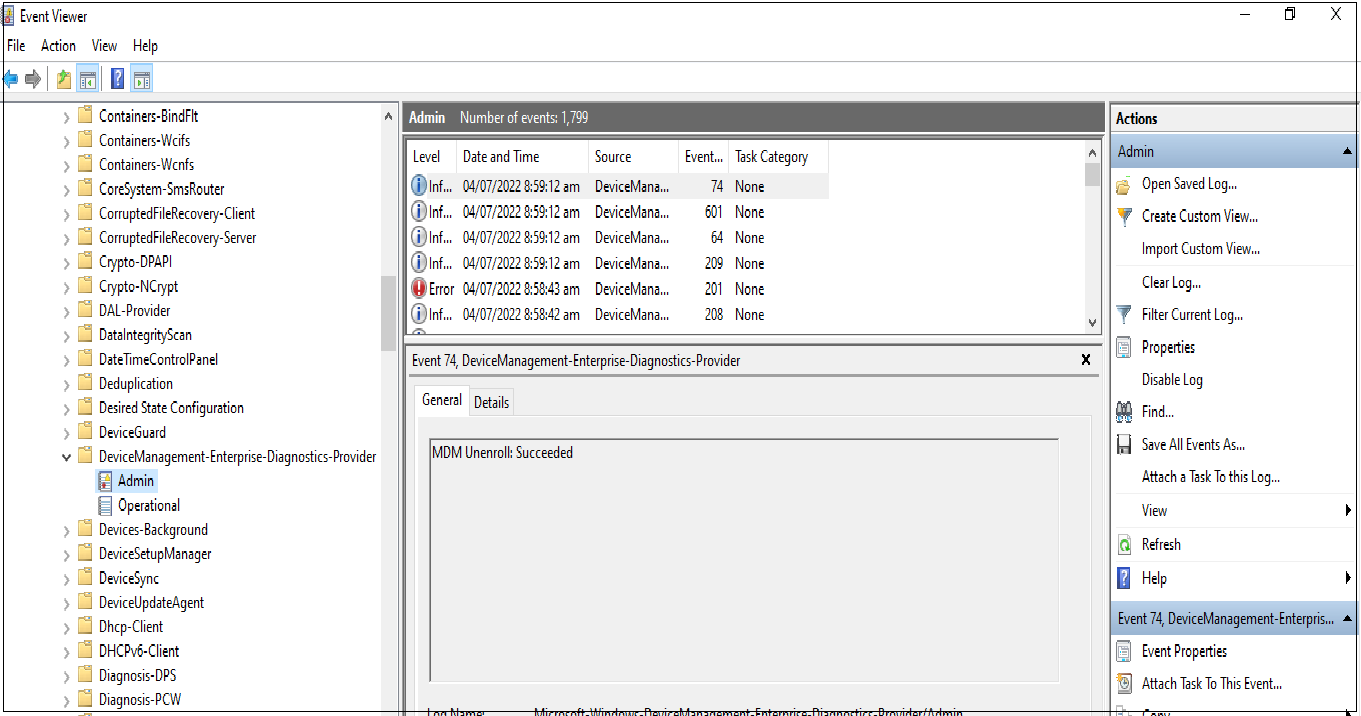
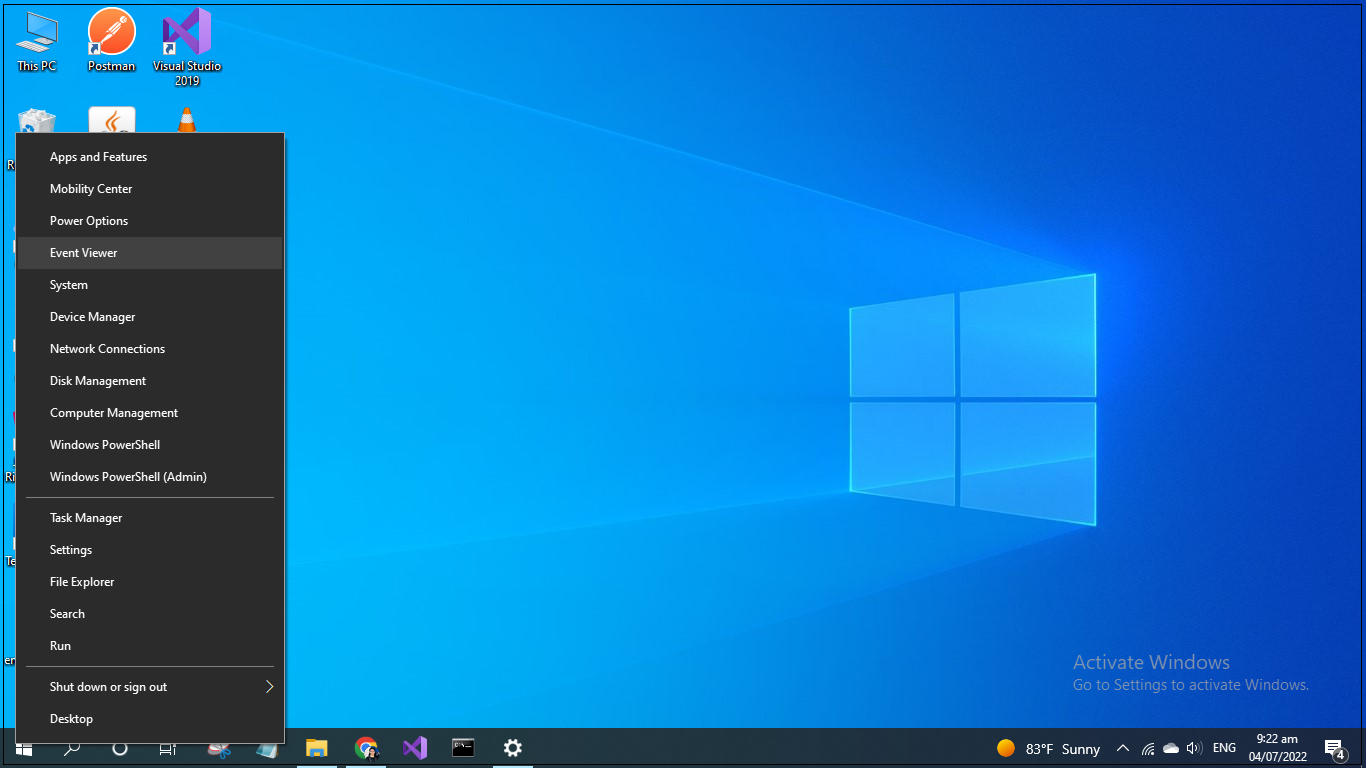
Microsoft Windows Server Event Viewer is a monitoring tool that shows a log of events that can be used to troubleshoot issues on a Windows-based system. Follow the steps below to open the Event View:
- Click Start > Control panel > System and security > Administrative tools > Event viewer Or;
-
Right click Start and select Event viewer.
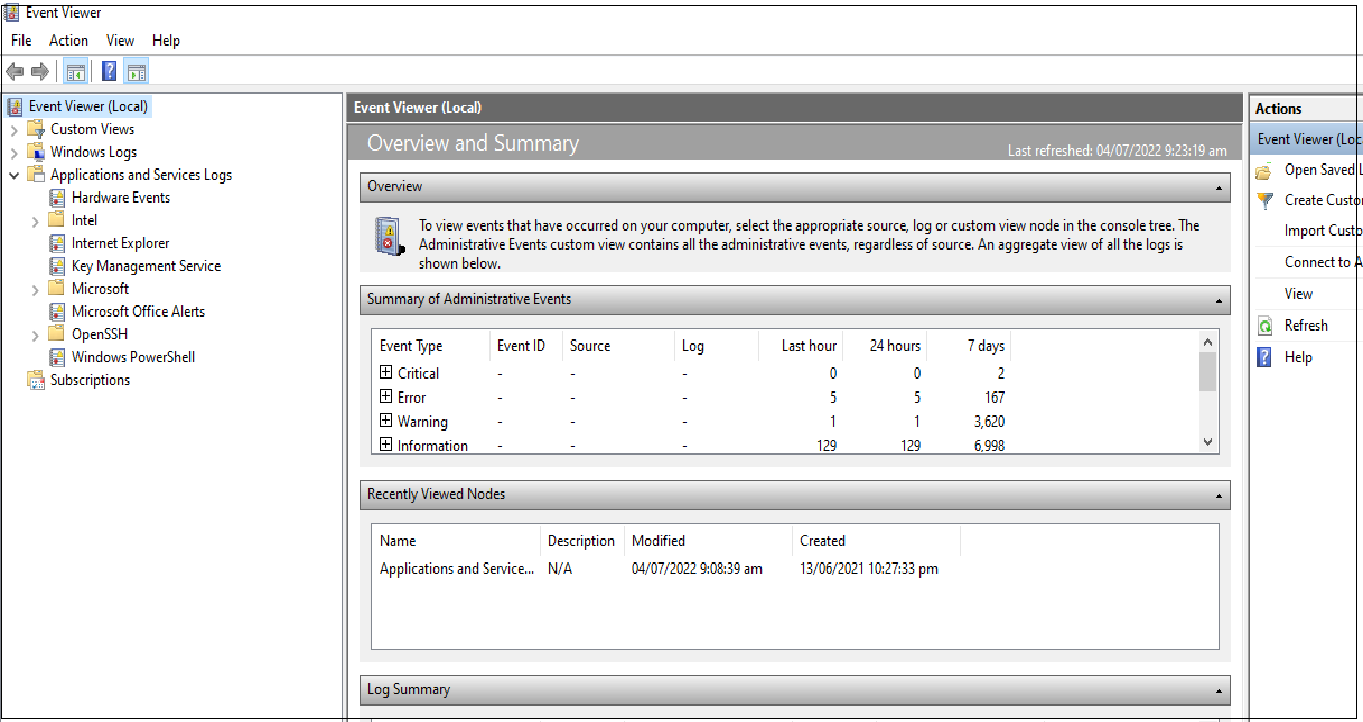
-
Then go to the Applications and Services logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin.